We’d Like to Help Capital One Prepare for the Next “Paige”
The Capital One data breach has put cyber risk management in the spotlight. From a scenario-building perspective, it’s the kind of story that gives the Axio team global attention and serves as a flagship use-case for the Axio360 platform. We’ve even written a book outlining how to drive continuous cybersecurity improvement if you want to jump right into the solution.
But returning to the Capital One data breach, here’s a scenario recap:
- The drama couldn’t be more captivating (106+ million customer records stolen and disclosed online).
- The hacker in question couldn’t be more memorable (the incident was fueled more by revolutionary ideals than monetary gain).
- And the consequences couldn’t be more devastating. The bank must now incur a fine of $80M by the Office of the Comptroller of the Currency.
Capital One Unfairly Singled Out by the OCC
On August 7th, 2020, the Office of the Comptroller of the Currency (OCC) said Capital One failed to “establish effective risk assessment processes” before transferring its operations to the public cloud and did not “correct the deficiencies in a timely manner.”
As the hacker Paige Thompson is allowed to “roam” freely in the Seattle area before her case goes to trial, the bank is now required to enhance its cybersecurity security defenses and submit a plan to the Federal Reserve within 90 days outlining how it intends to do so. They must also submit an internal audit of the firm’s risk management program.
This $80M fine by the OCC sends a strong message from regulators about how they would like to look at cybersecurity planning. Regardless of the technological sophistication of the victim, the hundreds of millions of dollars spent on cybersecurity investment, and immense controls put in place, it’s not enough. Organizations must demonstrate a clearly documented cybersecurity plan.
Matching Capital One’s Internal and External Customer Experience for Best of Class Cybersecurity
Taking a step back before discussing cybersecurity planning, it’s important to understand Capital One was always a technology first organization. Back in 2018, in an article in Information Week, their CIO Rob Alexander talked about how he “transformed his organization from an IT shop in a bank into a software company with Agile development, public cloud, new talent, open source technology, and machine learning.” This kind of strategy was necessary to provide the very best external customer experience.
Concurrently, this type of rapid growth probably resulted in an enormous amount of new systems and processes to monitor and detect against. Behind the scenes, internal organizations such as security, risk, compliance, and IT had to collaborate 24/7 to ensure that all data flowed freely without interruption. They too, required an excellent customer experience amongst themselves to efficiently complete their tasks.
It’s impossible to point fingers at any one person, process or technology at Capital One. There’s been a great deal written about the technicalities behind the event. The way in which the hacker, Paige Thompson gained access to the company’s cloud instances demonstrated a deep understanding of Identity and Access Management policies for Amazon Web Services and exploiting very unique vulnerabilities in specific configurations. How can the internal organizations of Capital One have this same level of understanding? The question begets, what constitutes a good cybersecurity plan?
Having Complete Visibility for Improvement and Satisfying the Demands of Regulators
Using a strong cyber risk methodology can quickly satisfy the demands of regulators. It also can serve as the ground truth for an organization on the cutting edge of technology, such as Capital One. For example, assessing the maturity of a cloud security program in one dynamic dashboard can allow security and risk leaders to quickly determine and communicate the most appropriate controls and processes necessary for cyber posture improvement, in regard to identity and access management.
We don’t dispute that achieving higher maturity levels in this category is an easy task. But we’ve seen it done by approaching cybersecurity program management in a holistic manner, with action items, targets for improvement, and a roadmap that the entire team has real time-visibility into.
Prioritization can be as intuitive as dragging and dropping an item on a Kanban board. We call it baby cyber steps that drive forward momentum. No organization should be confined to a stroller and never grow up because there are just too many things to do and it’s too difficult. With the right approach to cyber posture improvement from day one, Axio360 can ensure empowerment for every single team member.
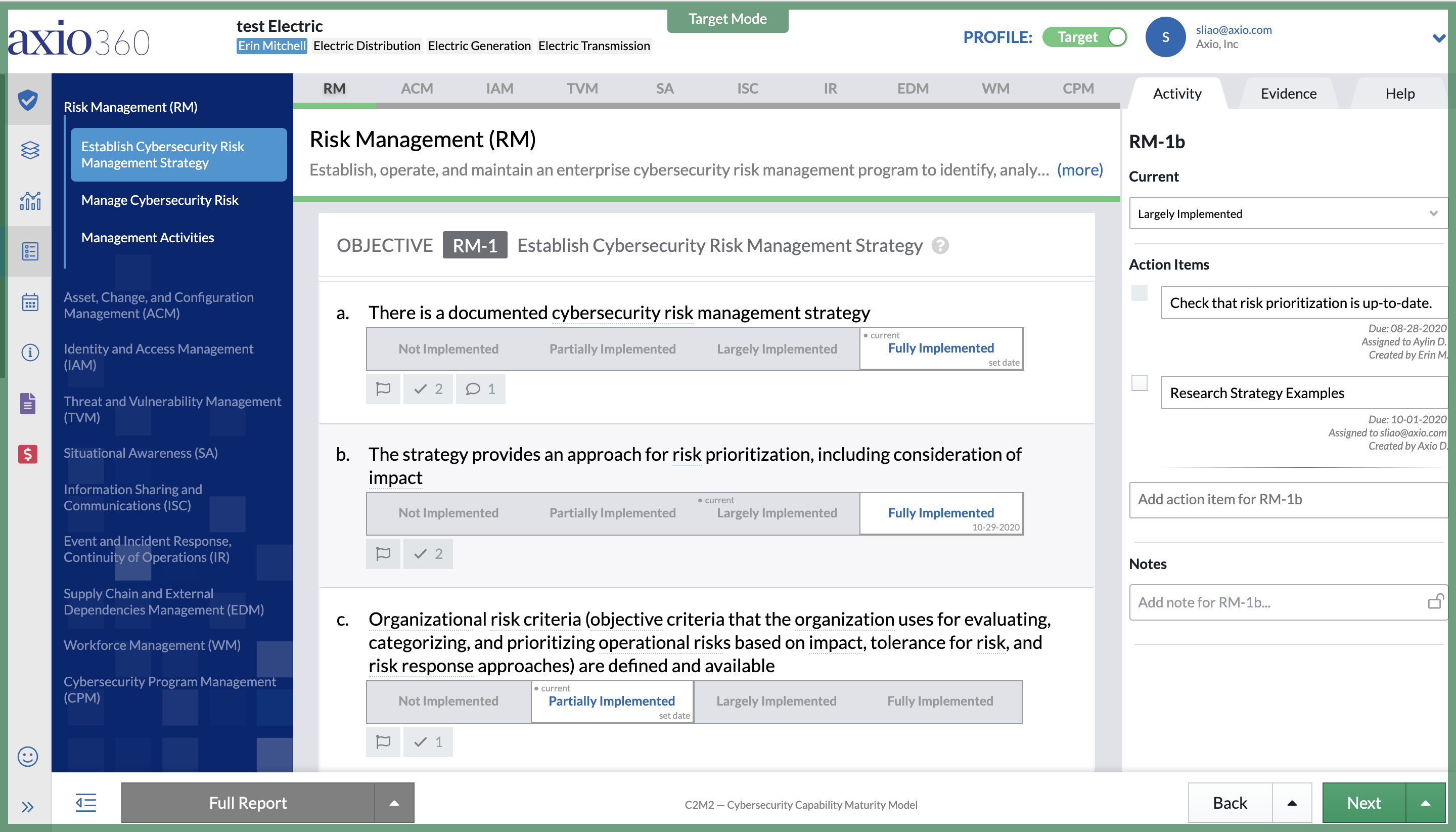
The Fastest (and best) Way to Document Your Cybersecurity Improvement Roadmap
We could only imagine the size of Capital One’s security organization; all the initiatives they have planned for improvement already, and all things they want to better secure. But in this point in time, there are multiple business functions within (and outside) the security org that need to quickly collaborate for forward-moving cybersecurity planning. Only a small fraction of these can realistically get done in 90 days. Right now, Capital One’s CISO has been presented with the tall task of quickly understanding and prioritizing the most important cybersecurity initiatives, and then presenting a plan of action in a clear and concise manner. Fortunately, 90 days is plenty of time. Our platform Axio360 has handled similar tasks in as little as 2 days.
Above, we’ve emphasized above the importance of continuously assessing how susceptible you are to a cyber incident through the evaluation of your entire cybersecurity program. For Capital One, this includes examining the organization’s people, processes, and technology. This rigorous self-evaluation identifies deficiencies and is a critical starting point for improvement. However, an assessment exercise on its own can’t improve cyber posture. Taking a step back, it is important to understand that assessments have multiple purposes. Is the intention of an assessment just an exercise in compliance to “check the box” or is it actually measuring how mature the program is? In order to truly improve your cyber program, measuring maturity is necessary. The less mature your practices, controls, and processes are, the more susceptible you are to a cyber-attack. When you have a measurement of your maturity you are on the right track and can prioritize improvements. However, the bridge on the path to cyber improvement is cyber risk quantification. This is the capability to quantify the cyber risk scenarios your organization is most susceptible in business terms (dollars). This approach would give Capital One’s CISO a much better use of time and resources in such a complex security organization.
Prioritizing cybersecurity improvements is what shifts an organization from a defend everything mindset to a defend what matters risk-based approach to cybersecurity. It also gives you the ability to defend your decisions by communicating them in easy-to-understand language. The concept is based on understanding the financial impact of your organization’s particular cyber scenarios if they would occur. Axio360 is built on this particular 4-step methodology we will summarize:
- Identify relevant cyber loss scenarios.
- Calculate scenario losses.
- Prioritize cybersecurity improvements.
- Communicate risk effectively.
When you use the Axio360 platform, you begin by building and prioritizing loss scenarios that would most impact the business, and then simulating a range of financial losses for each scenario using Monte Carlo methods and our unique model. This step can be completed in a few hours. From there, you can identify the necessary business and technical solutions, as well as their costs, and compare the risk reductions each solution will provide. These visualizations and models will allow you to communicate financial risk at all levels of business, from C-level executives to practitioners. Scenario-based analysis can be some of the most powerful tools executives have, giving them insight into requirements for business continuity, as well protecting the value of the shareholders’ investments. If you’d like to learn more about cyber risk quantification, you can download our eBook: Making the Business Case for Cybersecurity Investment
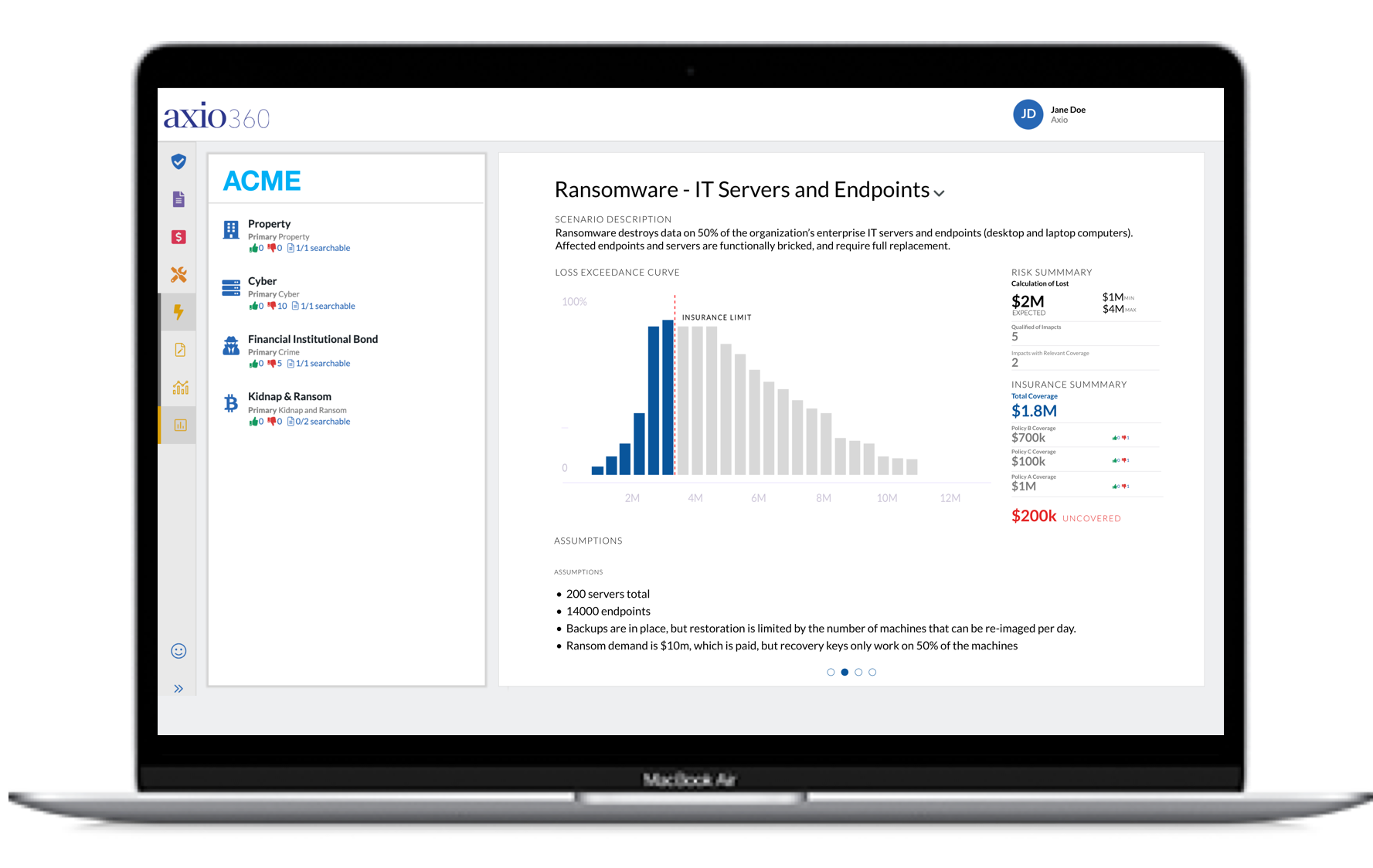
The Axio360 platform is designed to drive rapid business impact with each cybersecurity decision. The reporting capabilities in the platform allow a clear view of the ROI of planned security projects.
*** This is a Security Bloggers Network syndicated blog from Axio authored by Axio. Read the original post at: https://axio.com/insights/wed-like-to-help-capital-one-prepare-for-the-next-paige/





