U.S. Indicts North Korean Hackers in Theft of $200 Million
The U.S. Justice Department today unsealed indictments against three men accused of working with the North Korean regime to carry out some of the most damaging cybercrime attacks over the past decade, including the 2014 hack of Sony Pictures, the global WannaCry ransomware contagion of 2017, and the theft of roughly $200 million and attempted theft of more than $1.2 billion from banks and other victims worldwide.

Investigators with the DOJ, U.S. Secret Service and Department of Homeland Security told reporters on Wednesday the trio’s activities involved extortion, phishing, direct attacks on financial institutions and ATM networks, as well as malicious applications that masqueraded as software tools to help people manage their cryptocurrency holdings.
Prosecutors say the hackers were part of an effort to circumvent ongoing international financial sanctions against the North Korean regime. The group is thought to be responsible for the attempted theft of approximately $1.2 billion, although it’s unclear how much of that was actually stolen.
Confirmed thefts attributed to the group include the 2016 hacking of the SWIFT payment system for Bangladesh Bank, which netted thieves $81 million; $6.1 million in a 2018 ATM cash out scheme targeting a Pakistani bank; and a total of $112 million in virtual currencies stolen between 2017 and 2020 from cryptocurrency companies in Slovenia, Indonesia and New York.
“The scope of the criminal conduct by the North Korean hackers was extensive and longrunning, and the range of crimes they have committed is staggering,” said Acting U.S. Attorney Tracy L. Wilkison for the Central District of California. “The conduct detailed in the indictment are the acts of a criminal nation-state that has stopped at nothing to extract revenge and obtain money to prop up its regime.”
 The indictments name Jon Chang Hyok (a.k.a “Alex/Quan Jiang”), Kim Il (a.k.a. “Julien Kim”/”Tony Walker”), and Park Jin Hyok (a.k.a. Pak Jin Hek/Pak Kwang Jin). U.S. prosecutors say the men were members of the Reconnaissance General Bureau (RGB), an intelligence division of the Democratic People’s Republic of Korea (DPRK) that manages the state’s clandestine operations.
The indictments name Jon Chang Hyok (a.k.a “Alex/Quan Jiang”), Kim Il (a.k.a. “Julien Kim”/”Tony Walker”), and Park Jin Hyok (a.k.a. Pak Jin Hek/Pak Kwang Jin). U.S. prosecutors say the men were members of the Reconnaissance General Bureau (RGB), an intelligence division of the Democratic People’s Republic of Korea (DPRK) that manages the state’s clandestine operations.
The Justice Department says those indicted were members of a DPRK-sponsored cybercrime group variously identified by the security community as the Lazarus Group and Advanced Persistent Threat 38 (APT 38). The government alleges the men reside in North Korea but were frequently stationed by the DPRK in other countries, including China and Russia.
Park was previously charged in 2018 in connection with the WannaCry and Sony Pictures attacks. But today’s indictments expanded the range of crimes attributed to Park and his alleged co-conspirators, including cryptocurrency thefts, phony cryptocurrency investment schemes and apps, and efforts to launder the proceeds of their crimes.
Prosecutors in California also today unsealed an indictment against Ghaleb Alaumary, a 37-year-old from Mississauga, Ontario who pleaded guilty in November 2020 to charges of laundering tens of millions of dollars stolen by the DPRK hackers.
The accused allegedly developed and marketed a series of cryptocurrency applications that were advertised as tools to help people manage their crypto holdings. In reality, prosecutors say, the programs were malware or downloaded malware after the applications were installed.
A joint cyber advisory from the FBI, the Treasury and DHS’s Cybersecurity and Infrastructure Agency (CISA) delves deeper into these backdoored cryptocurrency apps, a family of malware activity referred to as “AppleJeus. “Hidden Cobra” is the collective handle assigned to the hackers behind the AppleJeus malware.
“In most instances, the malicious application—seen on both Windows and Mac operating systems—appears to be from a legitimate cryptocurrency trading company, thus fooling individuals into downloading it as a third-party application from a website that seems legitimate,” the advisory reads. “In addition to infecting victims through legitimate-looking websites, HIDDEN COBRA actors also use phishing, social networking, and social engineering techniques to lure users into downloading the malware.”
The alert notes that these apps have been posing as cryptocurrency trading platforms since 2018, and have been tied to cryptocurrency thefts in more than 30 countries.
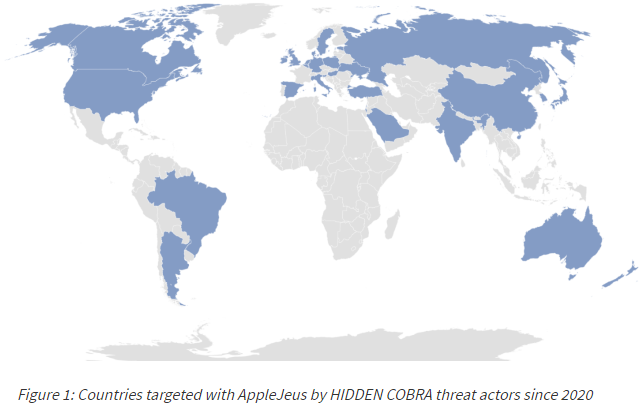
Image: CISA.
For example, the DOJ indictments say these apps were involved in stealing $11.8 million in August 2020 from a financial services company based in New York. Warrants obtained by the government allowed the FBI to seize roughly $1.9 million from two different cryptocurrency exchanges used by the hackers, money that investigators say will be returned to the New York financial services firm.
Other moneymaking and laundering schemes attributed to the North Korean hackers include the development and marketing of an initial coin offering (ICO) in 2017 called Marine Chain Token.
That blockchain-based cryptocurrency offering promised early investors the ability to purchase “fractional ownership in marine shipping vessels,” which the government says was just another way for the North Korean government to “secretly obtain funds from investors, control interests in marine shipping vessels, and evade U.S. sanctions.”
A copy of the indictments is available here (PDF).
*** This is a Security Bloggers Network syndicated blog from Krebs on Security authored by BrianKrebs. Read the original post at: https://krebsonsecurity.com/2021/02/u-s-indicts-north-korean-hackers-in-theft-of-200-million/





