Threat Hunting Framework: Three Steps to Translate Threat Reports into Actionable Steps
Thanks to Sally Vincent and Dan Kaiser from the LogRhythm Labs team for developing the process and guiding content described in this post.
Threat research can be an invaluable asset to security teams when attempting to formulate a proactive stance or reactive response. Whether the subject is a previously undocumented attack type or a new variant of a well-known threat, research can provide much-needed context and insight to help practitioners identify and resolve gaps in their security program in order to avoid being exploited.
However, techniques, methods, and actions found in threat research don’t always easily translate into practical steps you can take to prevent, detect, mitigate, or respond should a particular attack occur. While research can offer up specifics that can educate you on what occurs during an attack, what you really need is a threat hunting framework that transforms those details into concrete strategies and actions based on the cybersecurity frameworks you rely on – including MITRE ATT&CK® and NIST – to make the research truly valuable.
Our LogRhythm Labs team is no stranger to this. In fact, they’ve developed a three-step “Intelligence to Readiness Pipeline” to help make this process easier. Continue reading for an overview of these steps — mapping a report to ATT&CK techniques, vetting techniques, and reviewing the techniques through a Purple Team exercise — including video demos of each step in action from a recent webinar with UWS. And if you’d like to watch the full process from start to finish, you can find the full webinar recording at the bottom of this page, which uses a report on Maze ransomware as an example.
Step 1: Break Threat Intel Report into Keywords Automatically and Map to MITRE Techniques
Some threat reports may already have a list of ATT&CK techniques that are relevant to the report. But if that’s not the case, there are two main ways you can translate report content into techniques:
- Use an automated threat hunting tool such as MITRE Threat Report ATT&CK Mapper (TRAM). As stated by MITRE: “Our hope is that automating mapping to ATT&CK can reduce analyst fatigue, increase ATT&CK coverage, and improve consistency and accuracy of threat intelligence mappings.”
- Run a search against keywords from the report using Google or Attackcti, “[a] Python module to access up to date ATT&CK content available in STIX via public TAXII server.”
And how do you figure out what keywords to search for? You can get these by either:
- Looking at the document’s HTML tags
- Pulling out important sentences
Then you can simply search for the tags and/or full sentences to determine the relevant ATT&CK techniques.
Sally and Dan did this with the Maze threat report along with the help of Jupyter Notebook. Get a full sense of their process in this 5-minute video.
Step 2: Vet and Prioritize Techniques
Once you have gathered a list of techniques, the next step is to determine which techniques to prioritize in order to best set up your team for success against the threat in question.
There are several ways you can approach technique prioritization. You can base it on:
- Frequency: Focus on the techniques that are mentioned most frequently from the threat report.
- Where the techniques fall in the kill chain: Focus on techniques happening earlier in the kill chain so that you can detect them prior to exfiltration and encryption of data.
- Detection volume or noisiness: Focus on the techniques that aren’t as noisy. This will make it easier to sift through and distinguish malicious behavior from normal behavior, which is important to do quickly.
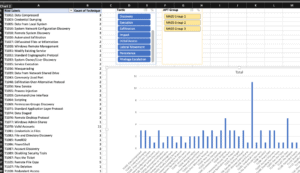
Figure 1: Example of a volume analysis showing how many times certain techniques are mentioned in a threat report
Step 3: Stage Purple Team Exercise
Once you have vetted and finalized the techniques, the final step is to stage a Purple Team exercise. The goal of this exercise is to increase your coverage of techniques and reduce the detection and mitigation time. A Purple Team exercise is where a Red Team and Blue Team work closely together and run through a series of “open book” exercises. The Red Team simulates the techniques in the environment and the Blue Team demonstrates the techniques that can be detected either through manual hunting or automated analytics.
Below are several best practices when conducting the Purple Team exercise, as suggested by Dan Kaiser:
- Tight communication and collaboration between the Red and Blue teams: Each side needs to communicate the actions they are taking, their findings, and their challenges so that the other side can assist.
- Documentation: The Red Team must document how they simulated an adversarial action (which tools they used, the command-line parameters they used, which machines and devices were attacked, etc.). The Blue Team needs to document how they detected the adversarial action (which security tools and log sources provided the information, whether the action was detected by real-time analytics or if the team had to hunt to find evidence of the action, etc.) as well as gather the artifacts/evidence of the detection.
- Measurement: The Blue Team needs to record how long it took to detect a given action (Time to Detect or TTD) so that analysis can be performed to identify improvement areas and to compare performance over successive Purple Team engagements.
- Using the ATT&CK framework: The MITRE ATT&CK framework has become the standard knowledge base of adversarial tactics, techniques and procedures (TTPs). Structuring your purple team engagements around ATT&CK will make everything easier.
- Commitment to improving and automating your detections: If the Blue Team had to hunt to uncover an adversarial action, they should engineer a real-time detection for it whenever possible.
LogRhythm offers several features that can be useful for Purple Team exercises through our Case Management functionality. Case Management provides a container for all data relevant to incidents varying from playbooks and log evidence to categorizations and auditing. It enables accurate threat detection and response by ensuring that threats are proactively identified, prioritized based on organizational risk, and rapidly investigated within the LogRhythm Platform for streamlined incidence response.
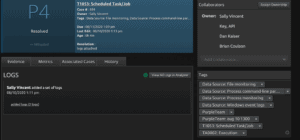
Figure 2: LogRhythm Case Management interface
Some of the features that can be particularly useful during a Purple Team exercise include:
Case Tags: Case tags allow you to add categorization to your cases. These tags will then allow you to search for cases more easily and pull performance reporting and metrics per tag.
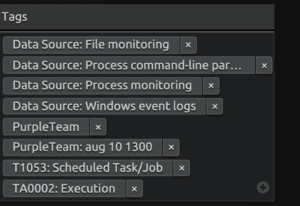
Figure 3: Case Tags within LogRhythm Case Management
Case Playbooks: Case playbooks allow you to ensure that incidents are handled in a methodical and repeatable way and procedures can be assigned to individual members of the team.
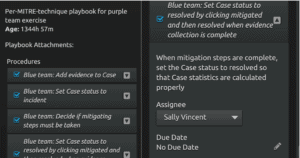
Figure 4: Case Playbooks within LogRhythm Case Management
Case Metrics: Case metrics allow you to measure the timeliness of detection and response and track your improvement over time.
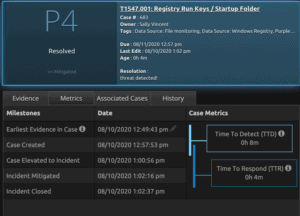
Figure 5: Case Metrics within LogRhythm Case Management
Case Metrics Dashboards: These dashboards allow you to look at aggregated data from individual cases by trend, status, and priority.
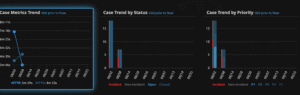
Figure 6: Case Metrics Dashboards within LogRhythm Case Management
Case API: Case API allows you to work with the features of the case programmatically. For example, you can use the case API to query MITRE and populate cases with data source requirements.
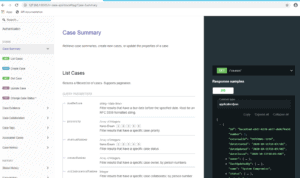
Figure 7: Case API within LogRhythm Case Management
To help you visualize the process from start to finish, Dan and Sally presented a full demo of Purple Team exercise using LogRhythm Case Management. Watch the demo here to get the best practices for setting up your Purple Team exercise.
Prepare Your Team to Defend Against Potential Threats
We hope the three-step “Intelligence to Readiness Pipeline” by Sally and Dan makes it easier for your security team to translate threat reports into actionable steps that can prepare your team to defend against potential threats. If you would like to see the full demo videos and learn more about how our security experts used this process to make a Maze ransomware report actionable, we encourage you to check out the video below.
The post Threat Hunting Framework: Three Steps to Translate Threat Reports into Actionable Steps appeared first on LogRhythm.
*** This is a Security Bloggers Network syndicated blog from LogRhythm authored by Chi Doan. Read the original post at: https://logrhythm.com/blog/threat-hunting-framework-three-steps-to-translate-threat-reports-into-actionable-steps/





