The Most Read Cybersecurity Blogs of 2020
2020.
The year when we baked a lot of bread.
We wore sweats to work.
We erased the line between work and personal lives.
We hung out on zoom and not just for work meetings, but for happy hours with our work and non-work friends.
And some of us also wrote a lot of blogs… (126 to be precise) on various cybersecurity and IT topics. Our blogs were read by nearly 40,000 people, who spent an average of 12 minutes reading each blog. Among our readers were hundreds of CISOs and CIOs of the Fortune 1000 companies.
We discussed topics such as cybersecurity visibility, risk-based vulnerability management, cyber-resilience, asset inventory, reporting to the board of directors, Patch Tuesdays, cyber risk calculation, and gamification of cybersecurity posture improvement.
Some of our blogs were useful (like the 9 Slides You Must Use in Your Board Presentation), and ended up in boardroom presentations.
Some challenged the status quo (4 Reasons Why Your Asset Inventory is Inaccurate) and inspired positive change at a few organizations.
Some were controversial (Stop Blaming the CISO for a Breach).
Some were funny (Adventures of CISO Ed & Co. – Pandemic Edition).
Some were, well, unexpectedly popular (Top 14 Cybersecurity Zoom Backgrounds). But they were all great (excuse the shameless brag, please!)
Here is a recap of our 6 most popular blogs of 2020.
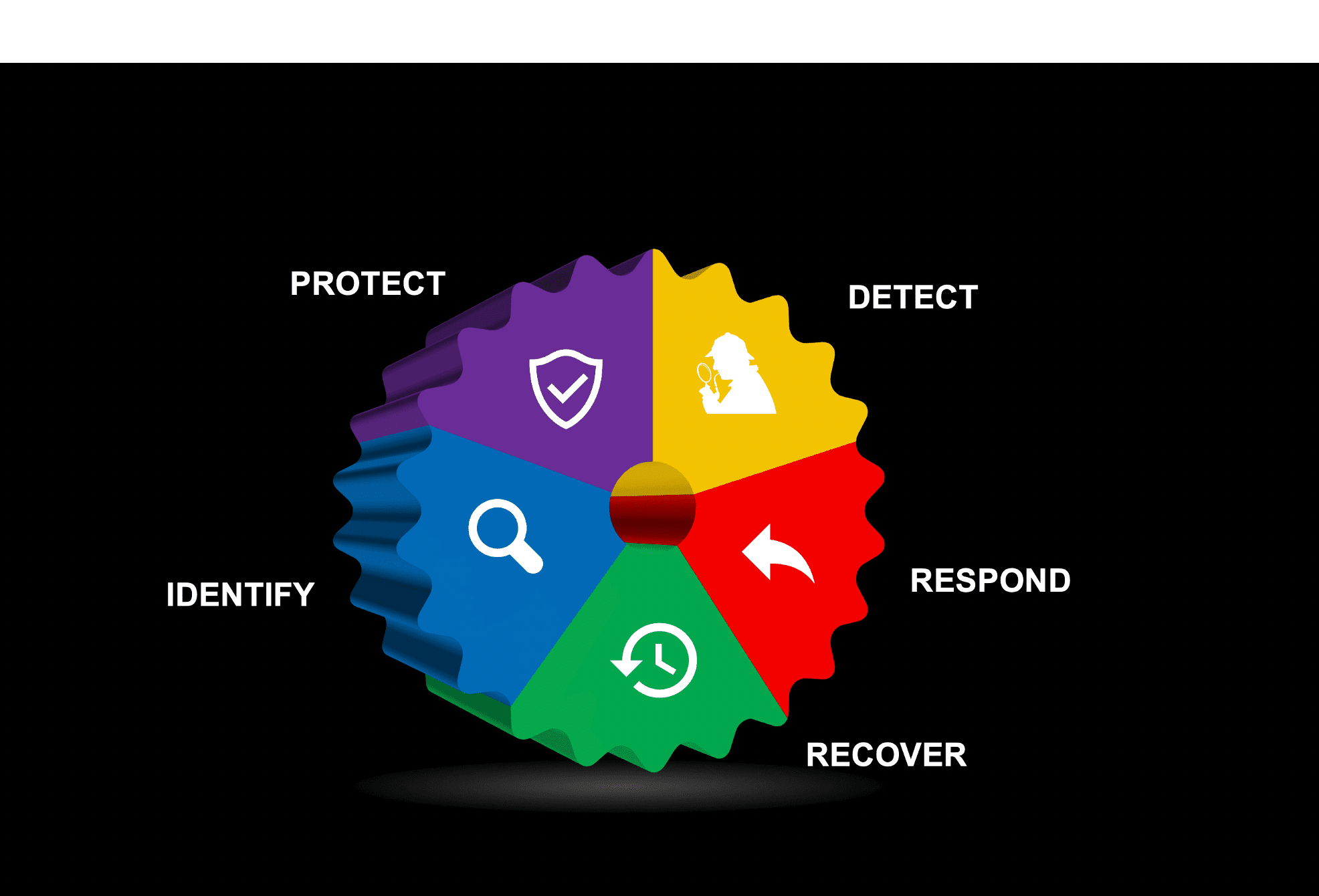
#6 – How to Operationalize the NIST Cybersecurity Framework
While the NIST Cybersecurity Framework offers excellent guiding principles to architect your cybersecurity defenses, it can be difficult to dive into and implement. Many cybersecurity leaders found this blog-series useful for understanding how to align their existing cybersecurity programs with the NIST framework.

#5 – 5 Mistakes CISOs Make in Their Board Presentation
In this blog, we summarized 5 common mistakes CISOs make in their board presentation and how you can avoid them
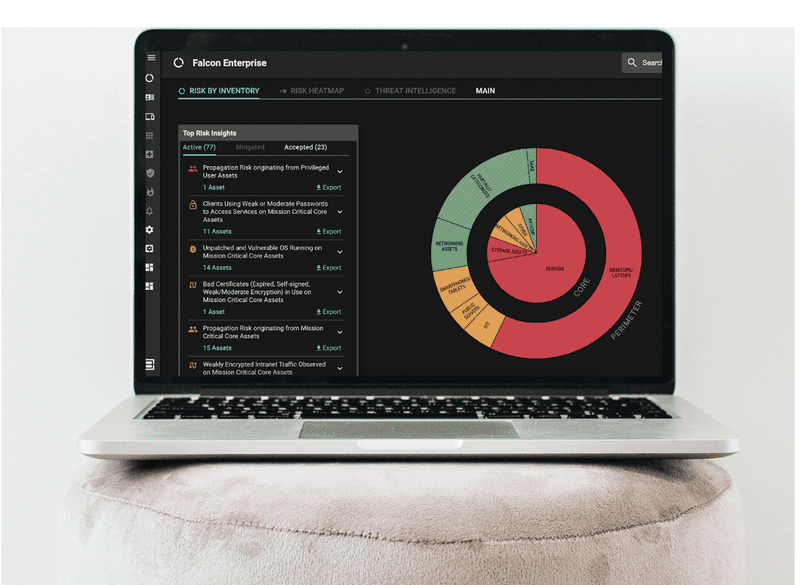
#4 – Under-Resourced Team? Here’s How to Minimize Breach Risk
This blog provides 3 key steps that under-resourced teams can take to while continuing to make progress towards reducing breach risk to acceptable levels.
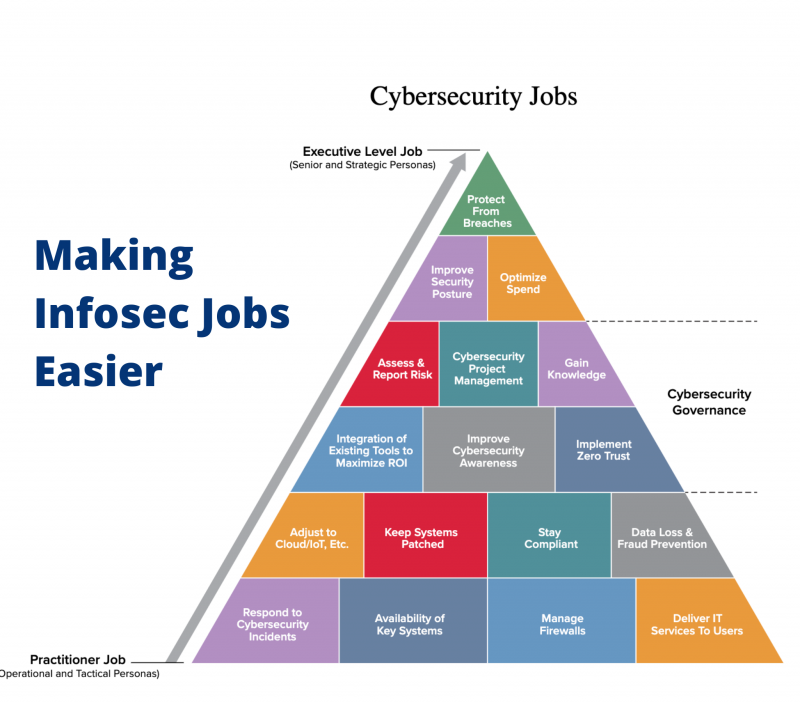
#3 – Making Infosec Jobs Easier: Improving Security Posture
This blog series examined the different “jobs” that a cybersecurity team has to perform to understand what makes these jobs hard, and how AI, automation and other new techniques can help.

#2 – What NOT to Do in Your First 90 Days as a CISO
Whether you’re a first time CISO or a new CISO to the organization, your first 30-60-90 days can be interesting, umm.. , daunting!
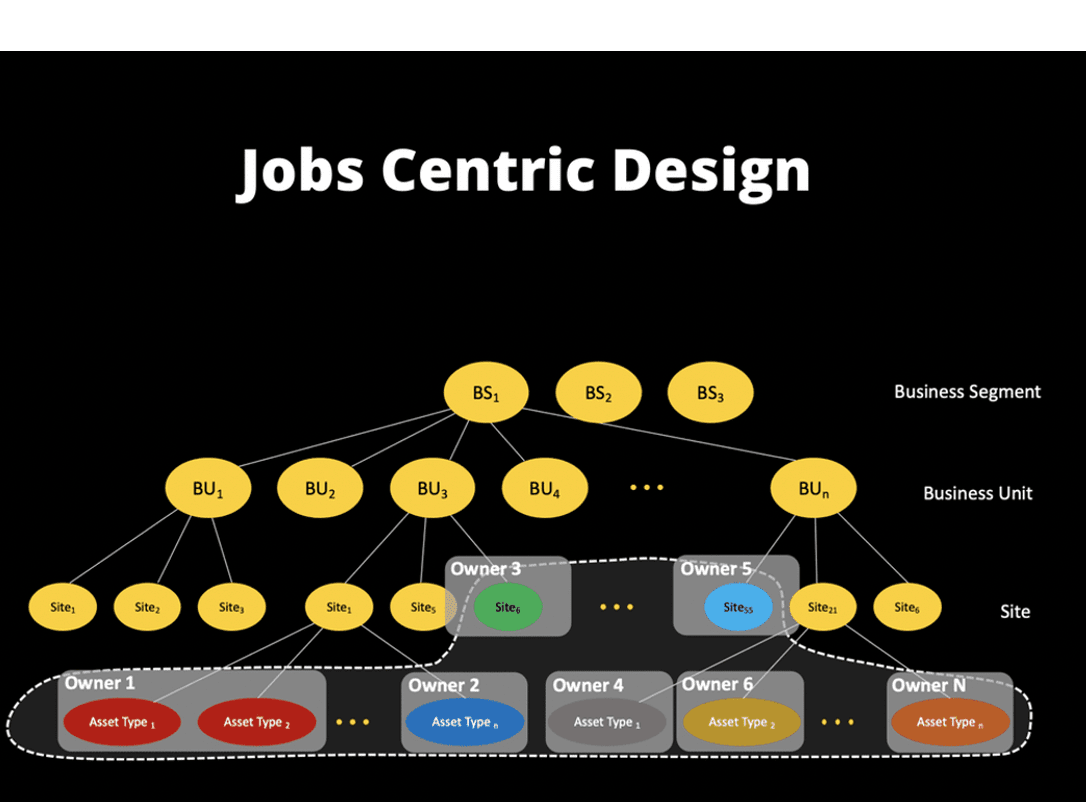
#1 – Job Centric Design: The Next Generation of Cybersecurity
This blog recapped some of the ways in which AI can be used to discover, prioritize, and mitigate unseen vulnerabilities and show a single, comprehensive, and up-to-date picture of the organization’s security posture.
Final Thoughts
When we reflect on the list of blogs above, we couldn’t help but wonder why these particular ones were the most popular out of the so many we wrote. Perhaps, it is because of the common theme running through this set:
Security leaders are frustrated with their inability to accurately measure and understand their attack surface. As a result, their cybersecurity decisions are based on gut feeling and incomplete data. They worry about unseen risks and vulnerabilities and struggle with how they can get better visibility. CISOs want tools that can help their teams perform their jobs efficiently and effectively. They want to be data-driven and better ownership of cyber-risk across their organizations.
Here’s to better cybersecurity posture visibility and for more insight-driven automation in the cybersecurity teams’ daily tasks in 2021!
See Balbix Live
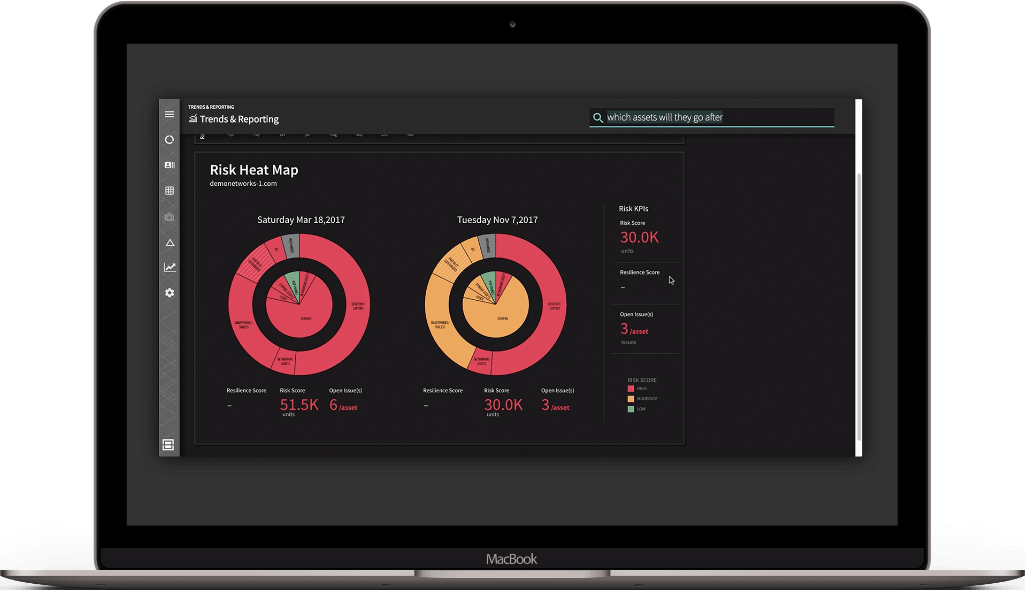
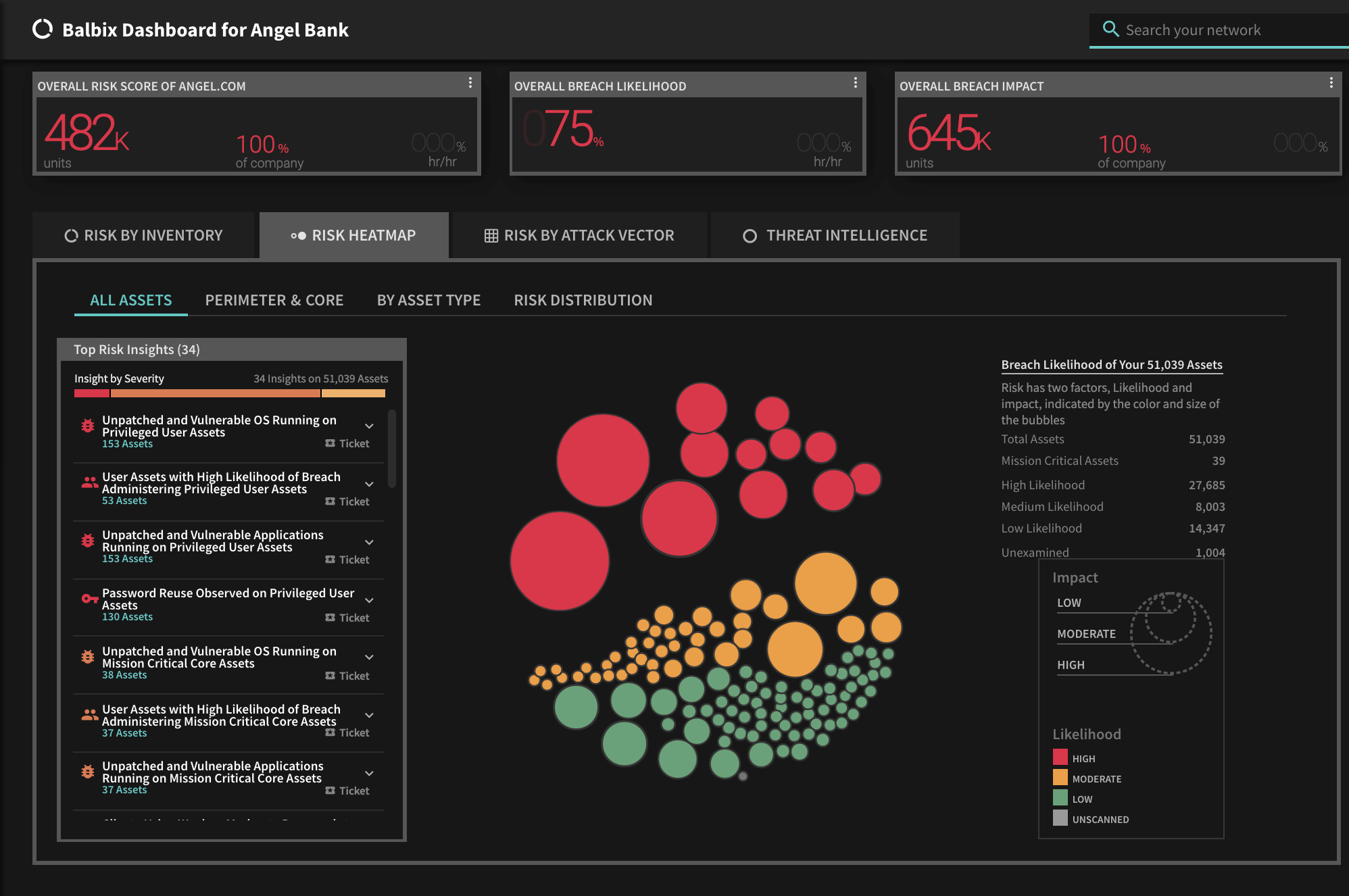
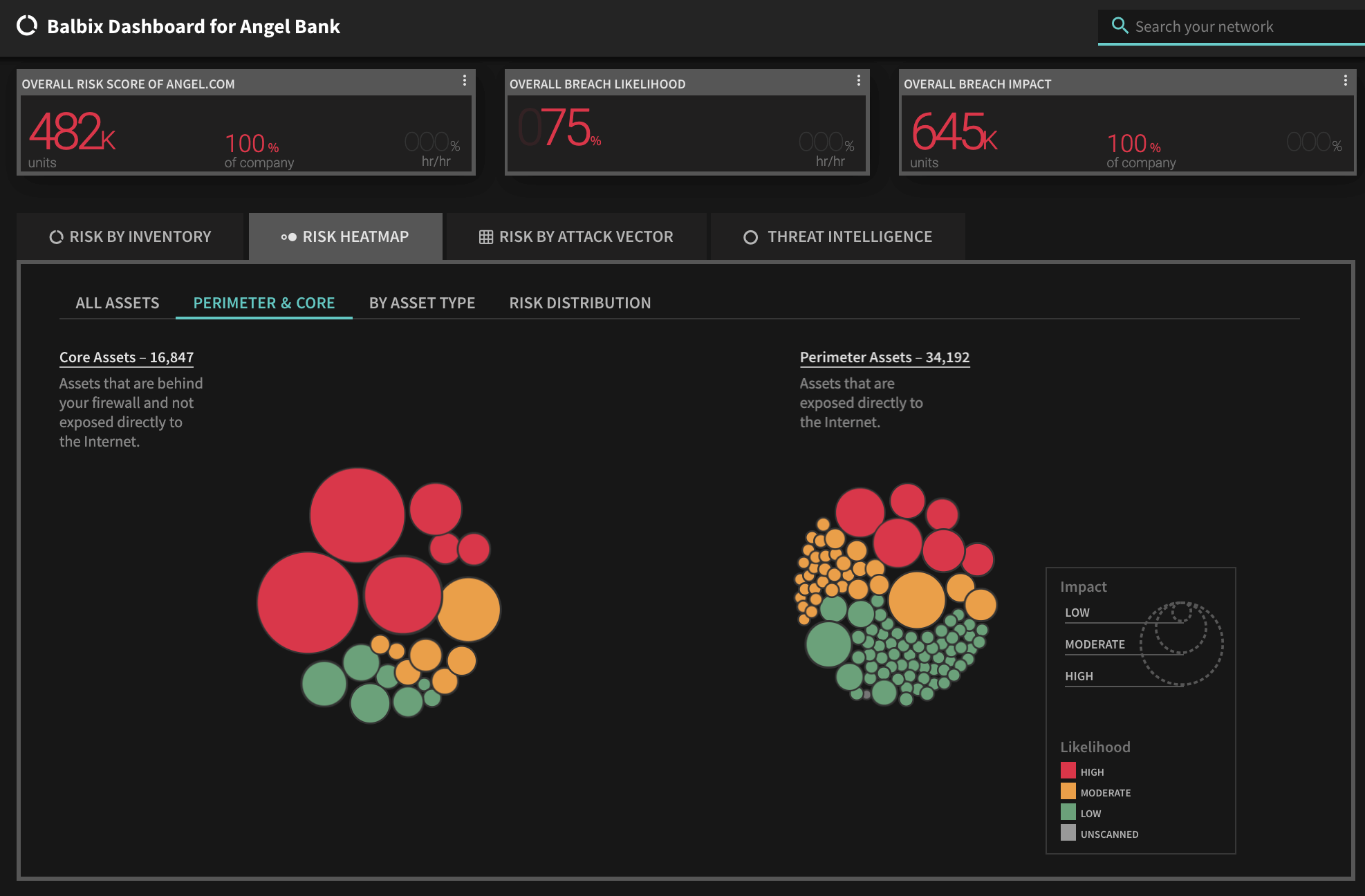
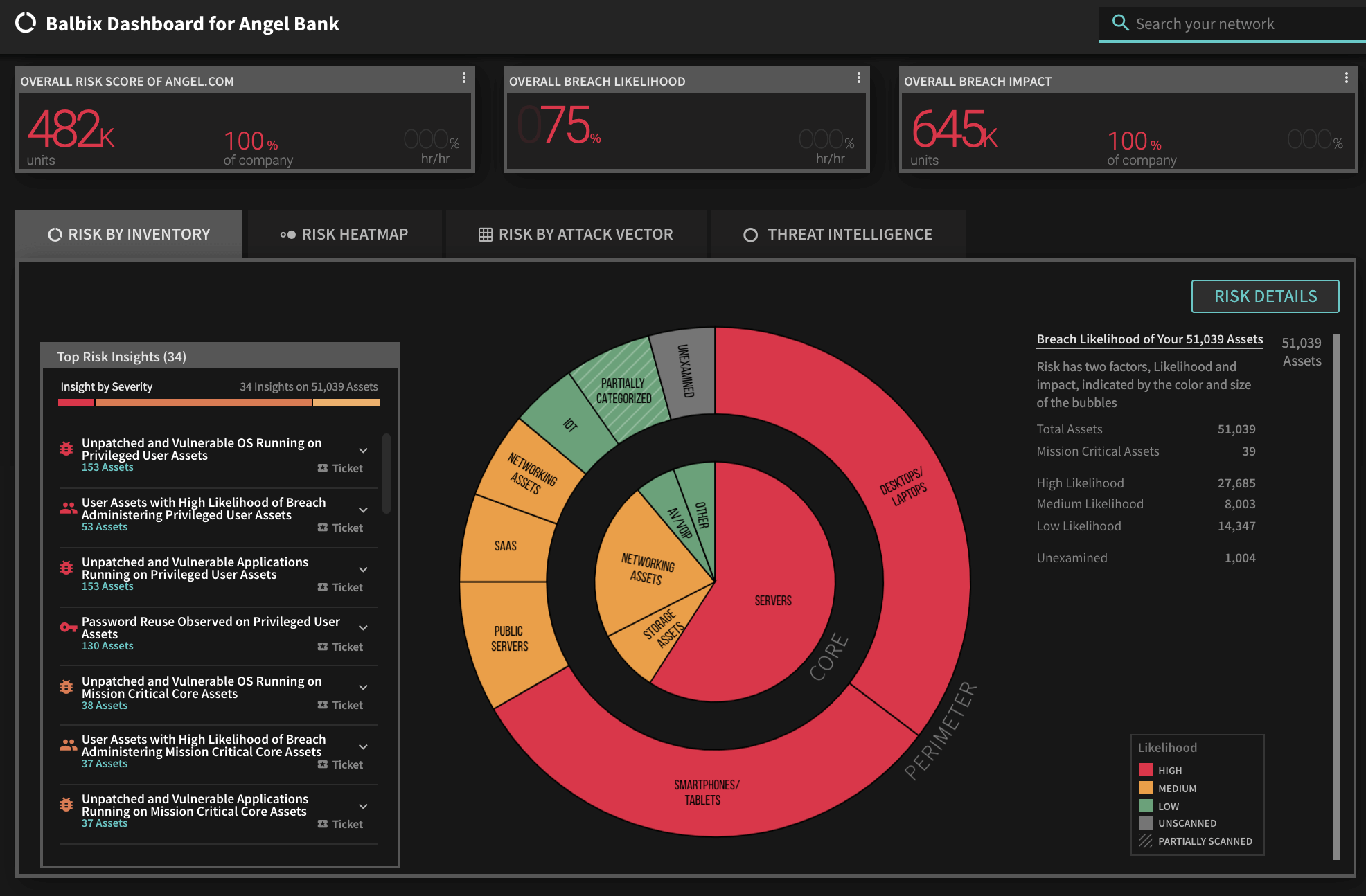
*** This is a Security Bloggers Network syndicated blog from Blog – Balbix authored by Ruchika Mishra. Read the original post at: https://www.balbix.com/blog/most-read-cybersecurity-blogs-2020/





