Back to Basics – Network Design
Networking is fun. It should also be pragmatic. There are many networks in production that have been architected like a service provider network, or how networking companies want them designed. This is not to say that these networks aren’t providing service, as they all are, just not to the scale of an ISP. These designs are likely implemented by people who love networking and just want to see as much of it as possible, at the expense of being impractical and expensive.
While robust and highly scalable, in most (outside of ISP’s all) environments this is like putting out a match with a firehose.
An illustration.
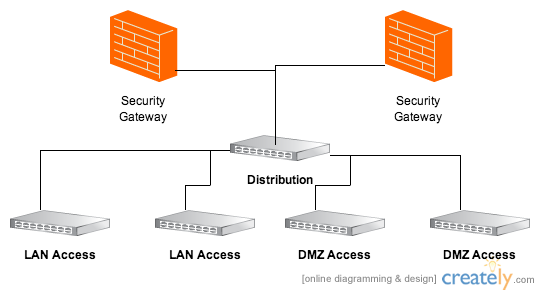
Many environments attempt to employ a very robust architecture like the one diagramed above that contains;
- Border Routers that connect to the Internet and are the first hop for the IPs provided by the ISP.
- Core Routers or Switches that handle routing between internal networks.
- Distribution Routers or Switches that aggregate Access Switches. They will either pass traffic between locally connected access switches or forward traffic up to the core.
- Access Switches that provide physical ethernet connectivity for endpoints (clients and servers).
- Security Gateways that may include multiple layers of firewalls, Network IPS, Web Gateway, and Email Gateway.
For better management and security all of this functionality can and should be collapsed into 2-3 layers.
- Firewalls (we will use security platform in placement of for a better description)
- Access/Distribution Switches
- Capital cost savings. We have eliminated at least three layers of physical appliances. While the cost of individual security gateways may increase due to their larger capacity, there is still cost savings of 50% on the overall equipment costs due to the reduction of metal boxes.
- Operational cost savings. All of the complex routing and filtering is being done on a single security gateway (or HA pair). Most of the daily modifications and troubleshooting will be on a single pair of devices. The switches can all be in simple layer2 mode. This is less places to look for trouble which saves time. Because the operational team will be spending most of their time in the security appliances they will develop strong skills fast which will also reduce the time to repair. Lest we forget rack space, power, and cooling.
- Better security. The more traffic that we route on an internal core network the less traffic will be visible to the security gateways. By putting the default gateway for all networks on the security gateway traffic between those networks will be scrutinized.
*** This is a Security Bloggers Network syndicated blog from Insecurity authored by asdfasdfasdfasdf. Read the original post at: http://stephenperciballi.blogspot.com/2014/04/back-to-basics-network-design.html