Featured Downloads

The Preventative, Developer-Driven Approach to Software Security
The focus on automation, tooling and reactive responses to cyber threats can no longer stand alone against an increasingly sophisticated threat landscape, where attackers are also employing advanced tools to successfully breach even the most protected networks and systems. What ... Read more

Future Frontiers: Why Developers Need to Go Beyond the OWASP Top 10 for Secure Coding Mastery
In 2021, we usher in a new era for the fabled OWASP Top 10. This latest release reveals some significant shake-ups, with Injection flaws finally being toppled from the top spot in favor of Broken Access Control vulnerabilities. Brand new ... Read more

OWASP Top 10 API: Strategies for Smart Developers
Threats to cybersecurity these days are ubiquitous and relentless. It’s become so bad that trying to keep up with them after programs are deployed has become almost impossible. However, in this age of DevSecOps, continuous delivery, and more data paydirt ... Read more
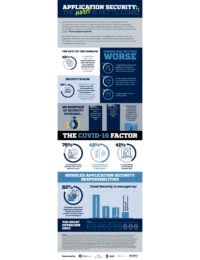
Application Security: The Best/Worst Is Yet to Come
In the wake of recent high-profile breaches, all eyes are on application security. Yet, application security hasn’t always received the attention during the application development process it deserves. Many organizations deploy applications with known vulnerabilities to meet their deadlines, with ... Read more

Adopting a Strategic Mindset for Cloud-Native Application Protection
With more applications being developed in a cloud-native fashion, using containers and serverless architecture, organizations should think about smarter, more efficient and more reliable ways to protect their applications. Cyberattackers are more innovative and are achieving more success in compromising ... Read more

Identity: The Real Key to Security
Identity and access management (IAM) has long been touted as an effective way to ensure data security by providing access only to those who have the correct permissions. In today’s increasingly distributed IT environment, more organizations look for zero-trust computing ... Read more
Security Boulevard Library
Welcome to our library of security-related resources. Here you will find whitepapers, ebooks, and more – all that will help you in your security journey. Access requires only a free registration. Search, scroll through and download what you like.

Container Security 101: Understanding the Basics of Securing Containers
By now it’s apparent to cybersecurity teams everywhere that the proverbial container genie is out of the bottle. Developers have widely embraced containers because they make building and deploying so-called cloud native applications simpler than ever. Not only do containers eliminate much of the friction typically associated with moving application ... Read more
Prisma

Security Challenges in the Cloud: Solving for Visibility and Protection Across Architectures
With the rise of cloud native applications, IT organizations in the never-ending pursuit of increased agility have now started to embrace new platforms at faster rates than ever before. There are now no less than three distinct layers of cloud native abstractions that are simultaneously being employed to run varying ... Read more
Prisma

How to Identify Compromised Devices with Certainty
It seems like there is an endless amount of exciting new devices these days, capable of things people never thought possible. But as with any technology stack, all devices come with inherent risks. Most security products only protect a fraction of all endpoints or require an agent to be installed ... Read more
Core Security

How to manage SAP-User Accounts and Access Rights with Identity Manager
Learn how you can simplify the management of SAP-user accounts and their access rights. Native SAP tools fall short and aren’t useful across the entire ecosystem. Read this white paper to see how your organization can integrate SAP-user data with your identity and access management (IAM) system and processes. One ... Read more
One Identity

SAP Customer Stories
Why struggle with IAM, especially when it comes to SAP? One Identity Manager is a comprehensive IAM solution that’s certified by SAP to work seamlessly with the growing portfolio of SAP modules. With Identity Manager, you can dramatically simplify and improve user lifecycle management, governance and authentication for all your ... Read more
One Identity

The State of DevSecOps
For years now, IT’s mantra has been “move quickly and break things.” To increase agility, companies adopted innovative and quick development practices. Great redesigns took place in the wake of DevOps. However, in this rush to implement forward-thinking practices, many teams eschewed security. No longer can institutions disregard security requirements ... Read more
Security Boulevard

The Second Wave of IT Security: How Today’s Leaders See the Future
As network security issues grew in the 1970s, and the 1980s brought the widespread use of the internet, the IT security profession expanded to address the malicious threats and innocent user mistakes of highly connected users and machines. Today, the security industry is experiencing what could be called a renaissance ... Read more
Security Boulevard

A Simple Guide to Successful Penetration Testing
How effective are your existing security controls against a skilled adversary? Discover the answer with penetration testing. The main difference between a penetration test and an attacker is permission. A hacker won’t ask for permission when trying to expose your critical systems and assets, so pen test to protect. A ... Read more
Core Security

Doing Identity Access Right
Caring for your company data as one of your most valuable assets can seem like a constant balancing act. In a world of corporate hacks and ransomware, keeping your data under digital lock and key is absolutely essential. But so is allowing your employees to use it to do their ... Read more
Core Security

Speed and Scale: How Machine Identity Protection is Crucial for Digital Transformation and DevOps
Digital transformation requires new approaches to security, demanding the protection of machine identities that enable authentication and encryption required for secure machine-to-machine communication. Solving machine identity protection challenges within DevOps environments, requires a fundamentally new approach. Information Security teams must deliver a frictionless, automated solution that allows DevOps engineers to ... Read more
Venafi

