What is Incident Response? Plans, Templates and Tools
The world of security threats is ever-shifting, and the stakes couldn’t be higher. Security professionals – analysts, SOC managers, CISOs and more – stand on the frontlines to defend organizations from the relentless onslaught of cyber threats. But what happens when the enemy breaches your defenses? How do you respond when chaos strikes and your digital fortresses are under attack?
That’s where incident response comes into play. From IR plans to popular frameworks and tools, it’s important to stay informed and prepared.
What is Incident Response?
To put it simply, incident response is a systematic approach to addressing and managing security events within an organization. It encompasses the processes, tools and strategies employed to detect, respond to and recover various types of security incidents, including:
- Phishing attacks
- Ransomware
- Supply chain attacks
- DDoS attacks
- Insider Threats
The goal is to minimize the impact of an incident and restore normal operations promptly while preserving vital assets and data.
What is an Incident Response Plan?
An incident response plan (IRP) is a documented set of guidelines and procedures that outlines the steps to be taken during a security incident. It provides a structured approach to effectively handle event and ensures action is swift, efficient and consistent across the organization.
An IRP can include predefined roles and responsibilities, communication protocols, incident categories, escalation procedures and technical steps.
Why is an IRP Important?
Having a well-defined IRP is crucial for several reasons:
Minimizes Damage: A timely and well-executed IRP can help minimize the impact of a security incident, reducing downtime, financial losses, and potential damage to the organization’s reputation.
Compliance and Legal Requirements: Many industries and regulatory bodies require organizations to have an IRP in place to meet compliance standards. A robust plan demonstrates a commitment to security and can assist in fulfilling legal obligations.
Rapid Recovery: An IRP enables organizations to recover swiftly from security incidents, restoring normal operations and mitigating any disruption to critical services.
Stakeholder Confidence: By demonstrating a proactive and competent approach, organizations can instill confidence in their customers, partners, and stakeholders, reinforcing trust and maintaining a positive reputation.
Incident Response Plan Templates
Security professionals can save time and kickstart their processes faster with IRP templates. Various providers and institutions have created templates to gain inspiration from:
What are the Incident Response Steps?
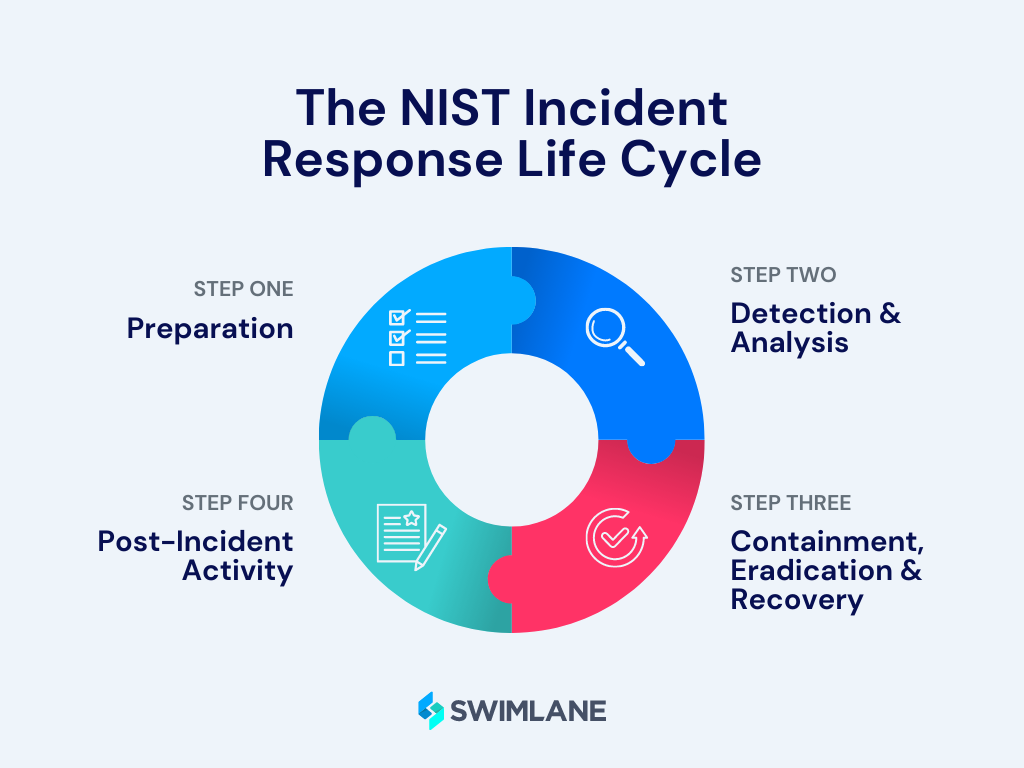
The incident response lifecycle consists of several interrelated phases that guide security professionals through the process of managing and resolving security incidents. For instance, The National Institute of Standards and Technology (NIST) framework includes:
1. Preparation: Establish an IRP, define roles and responsibilities, assemble an incident response team and implement necessary security controls and technologies.
2. Detection and Analysis: In this phase, security incidents are detected through various monitoring and alerting mechanisms. Incident analysts investigate the incidents, gather evidence and assess the impact and severity of each incident.
3. Containment, Eradication and Recovery: Once an incident has been confirmed, immediate action is taken to contain the incident, prevent further damage, eradicate the threat and recover affected systems and data.
4. Post-Incident Analysis: After the incident has been resolved, a comprehensive analysis is conducted to determine the root cause, identify any weaknesses in the security posture and implement measures to prevent similar incidents in the future.
There are similar steps in the SANS incident response plan, which is broken up into six key steps:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lessons Learned
Although different frameworks may present these phases in slightly varied ways, the core stages remain consistent.
Automating Incident Response Processes
Incident response automation involves leveraging technology and tools to streamline and accelerate the incident response process. Automation can assist in several areas, including incident detection, data collection, analysis, containment, and recovery.
By automating repetitive tasks, security teams can focus on higher-value activities, such as triaging more complex alerts and threat hunting. Additionally, automation can improve response times, reduce human error and enhance overall incident management efficiency.
Learn more about automated incident response.
Incident Response Automation Solutions & Tools
Incident response automation has emerged as a valuable solution to streamline security incident management. It enables security teams to respond swiftly and effectively to security incidents. Some standard incident response tools that organizations can leverage include:
- Low-Code Security Automation
- Security Orchestration, Automation and Response (SOAR)
- Security Information and Event Management (SIEM)
- Extended Detection and Response (XDR)
- Endpoint Detection and Response (EDR)
Learn more about Managing Security Alerts with an Incident Response Platform.
In today’s ever-evolving threat landscape, incident response is critical to a company’s security strategy. Modern security teams should implement a well-designed incident response plan and leverage automation to help minimize the impact of incidents, protect critical assets and maintain a secure environment.

Gartner: Selecting the Right SOC Model
‘Security and risk management leaders often struggle to convey the business value of their security operations centers to nonsecurity leaders, resulting in reduced investment, poor collaboration and eroding support…’ — Access this Gartner SOC Model report – courtesy of Swimlane.
The post What is Incident Response? Plans, Templates and Tools appeared first on Low-Code Security Automation & SOAR Platform | Swimlane.
*** This is a Security Bloggers Network syndicated blog from Blog Archives - Low-Code Security Automation & SOAR Platform | Swimlane authored by Ashlyn Eperjesi. Read the original post at: https://swimlane.com/blog/incident-response/







