The Jeopardy of Zombie APIs
Let’s unveil the hidden threats to Organizations. In the current digital landscape, organizations are exposed to a variety of risks. There is a rise in Zombie APIs ranking among the deadliest. No, we are not speaking about the zombies in horror films. Here, we’re talking about a perilous phenomenon called the zombie systems in the Application Programming Interfaces.
Introduction
Zombie APIs require proactive action to mitigate cyber threats. To find and address vulnerabilities, one must be sure to conduct frequent security audits, which also include the application of security updates. Firewalls, intrusion detection systems, and antivirus software are examples of effective security measures that can assist detect and stop unauthorized access. It is also essential to promote good cyber hygiene and give employees the information and skills necessary to spot and report suspicious behavior through employee awareness and training programs.
These infected devices constitute a serious security flaw. If not addressed, it could have disastrous effects on the organizations. In this blog, we would explore the vulnerabilities, vulnerability issues, and potential hazards that the zombie systems may present. We would moreover speak of the detrimental effects they have on organizations.
Zombie APIs: The Vulnerability Dilemma
Let’s first examine what zombie systems are and how they emerge before getting into the details. In any computer system, a zombie is an Internet-connected computer that has been infected by a hacker using a computer parasite, or any trojan horse program. This plays a major part of destructive actions at remote command and control of the hackers. Malware infestations, botnets, or other unauthorized access techniques could result in a compromise.
Systems that function in a zombie fashion have two drawbacks. Zombie APIs are often seen to be an essence of malicious purposes. These malicious purposes can be DDoS attacks, spam distribution, and malware distribution. Second, and perhaps more importantly, they act as a breeding ground for additional attacks. This gives hackers access to confidential organizational data without authorization, crippling systems, or even demanding ransom.
Organizational Effects of Zombie APIs
Now that we are mindful of the vulnerability problem, let’s investigate the wide-ranging effects that zombie APIs have on businesses. Check over the statistics below:
Financial Losses: According to a study done by a cyber security organization, zombie APIs helped cyberattacks expense organizations around the world $45 billion in 2022. These monetary losses are the result of several things, including operations disruptions, data breaches, and reputational harm.
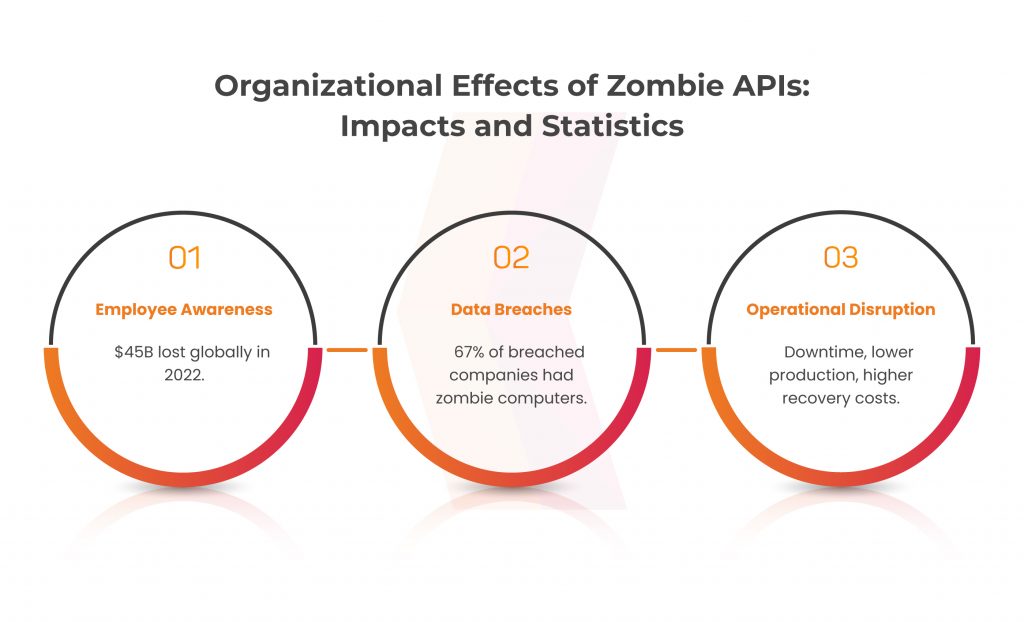
Data breaches: Zombie APIs can act as a point of entry for hackers to infiltrate a company’s network and obtain unauthorized access to sensitive information. In their network, 67% of companies that had a data breach in the previous year had zombie computers, according to a survey by a Cyber Security organization.
Operational disruption: When zombie APIs penetrate the network of an organization, they can seriously affect the regular operations of the company. The infected devices are involved in malicious activities. This results in network congestion, system lag, or even total system failure. This interruption frequently causes downtime, lower production, and higher recovery expenses.
Organizations work on one major factor, trust. Any security compromise can significantly harm the brand. Customers, partners, and other stakeholders stop having faith in the company’s capacity to safeguard private data. 78% of consumers responded in a survey as per research that they would stop doing business with a company, that did not adequately safeguard their data.
Organizations rely on trust, thus a security compromise can significantly harm their brand. Customers, partners, and other stakeholders stop having faith in the company’s capacity to safeguard confidential information. 78% of the people surveyed responded in survey research that they would stop doing business with an organization that did not sufficiently secure their data.
Mitigating the Zombie Threat
Fortunately, organizations can take proactive measures to reduce the cyber threats brought on by zombie systems. Here are some sensible tactics to take into account:
Regular Security Audits: Conduct thorough security audits regularly to find any potential network and device vulnerabilities. Address any discovered flaws very away, and make sure that all systems have the most recent security patches installed.
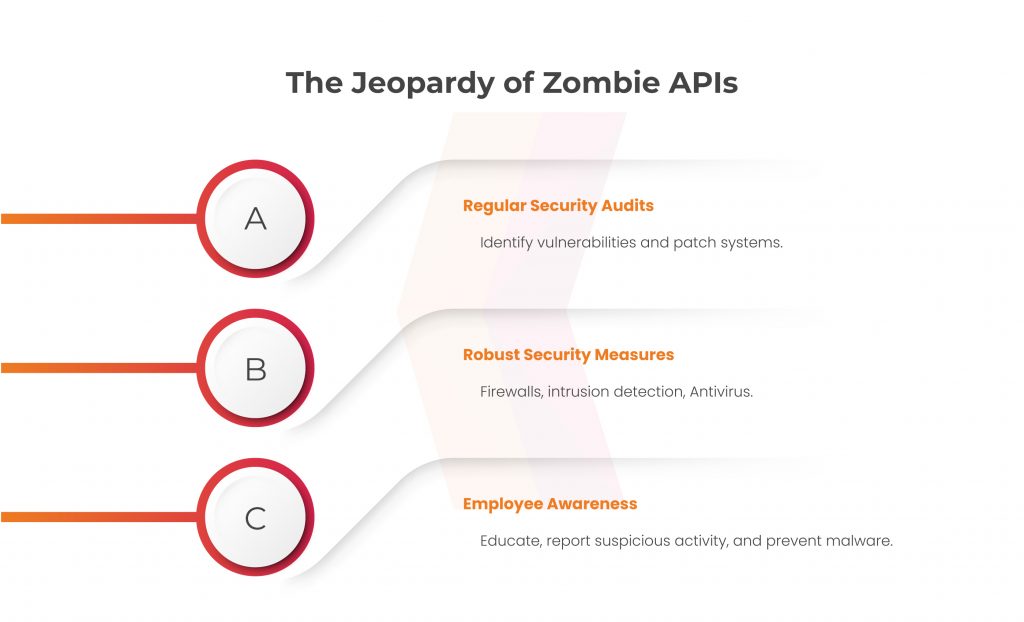
Robust Security Measures: Implement firewalls, detection of intrusions networks, and antivirus software as part of a multi-layered security strategy. Additionally, to find and stop shady network behavior, think about deploying sophisticated cyber threat intelligence tools.
Employee Awareness and Training: Educate employees on the dangers of zombie systems and the value of maintaining good cyber hygiene over the internet. Regularly educate them on how to spot suspicious activity and report it to prevent malware from spreading within the company.
Conclusion
In conclusion, organizations in the digital age face serious cyber threats from the emergence of zombie APIs. Hackers may use these infected gadgets for illegal activities such as DDoS attacks, spam distribution, and virus distribution. Additionally, they act as a breeding ground for new assaults, compromising organizational data and seriously interfering with business operations.
There are numerous negative implications of zombie systems on enterprises. In recent years, zombie system attacks have caused billions of dollars in losses on a global scale. These vulnerable systems have enabled data breaches that have allowed unauthorized access to sensitive data, harming reputations and deteriorating trust among consumers. Zombie systems can generate operational disruptions that result in downtime, lost productivity, and higher recovery costs.
In a nutshell, Kratikal offers an extensive approach to tackling the problem of zombie APIs by combining innovative technology. Kratikal works on proactive monitoring, rigorous testing, threat information, and robust training programs. Organizations that work hand in hand with Kratikal may boost their API security posture and protect their digital assets. This is done by the escalating threats posed by criminal actors abusing API vulnerabilities.

Organizations may reduce the risks connected with zombie APIs and safeguard their priceless assets by taking some proactive measures. To preserve the security, trust, and resilience of organizations in the constantly changing digital era, protection against this hidden cyber threat is crucial.
The post The Jeopardy of Zombie APIs appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Riddika Grover. Read the original post at: https://kratikal.com/blog/the-jeopardy-of-zombie-apis/




