SafeBreach Coverage for US-CERT Alert (AA23-158A) – CVE-2023-3462 MOVEit Vulnerability
On June 7th, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory highlighting the recent efforts of threat actors to disseminate CL0P ransomware. The various malicious indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) being leveraged by the threat actors are listed in US-CERT Alert (AA23-158A) – CL0P Ransomware Gang Exploits CVE-2023-34362 MOVEit Vulnerability.
According to the advisory, the CL0P ransomware gang also known as TA505 began exploiting a previously unknown SQL injection vulnerability CVE-2023-34362 in Progress Software’s managed file transfer (MFT) solution called MOVEit starting May 27, 2023. The internet-facing solution was infected with a web shell named LEMURLOOT which was then leveraged to steal the underlying data from the MOVEit databases. This campaign is similar to the previous zero-day exploits leveraged by TA505 against the Accellion File Transfer Appliance (FTA) and the Fortra /Linoma GoAnywhere MFT servers.
Technical Details
CL0P has been previously leveraged as a Ransomware as a Service (RaaS) in large-scale spear-phishing campaigns that used a verified and digitally signed binary to bypass system defenses. CL0P was previously known for its use of the “double extortion” tactic of stealing and encrypting victim data, refusing to restore victim access and publishing exfiltrated data on Tor. CL0P or TA505 is one of the largest phishing and malspam distributors worldwide having compromised more than 3,000 U.S.-based organizations and 8,000 global organizations. TA505 has previously targeted several file transfer applications including the following:
- Between 2020 and 2021, TA505 exploited several 0-days to install a web shell named DEWMODE on internet-facing Accellion FTA servers.
- In January 2023, CL0P targeted a 0-day vulnerability, CVE-2023-0669 to target the GoAnywhere MFT platform impacting nearly 130 victims over 10 days.
Exploiting CVE-2023-34362 (MOVEit Transfer Vulnerability) – In May 2023, the CL0P ransomware group exploited a SQL injection 0-day vulnerability, CVE-2023-34362 to install a web shell named LEMURLOOT on MOVEit Transfer web applications. This webshell was originally named human2.aspx with the intention of masquerading as the legitimate human.aspx file present in the MOVEit software. Once installed, this web shell generates a random 36-character password for authentication. This web shell interacts with HTTP requests containing a header field named X-siLock-Comment. Post-authentication with the web shell, the CL0P operators pass commands to the web shell allowing them to:
- Retrieve Microsoft Azure system settings and enumerate the underlying SQL database.
- Store a string sent by the operator and then retrieve a file with a name matching the string from the MOVEit Transfer system.
- Create a new administrator-privileged account with a randomly generated username and LoginName and RealName values set to “Health Check Service.”
- Delete an account with LoginName and RealName values set to ‘Health Check Service.’
NOTE – Progress Software, creators of MOVEit have discovered the vulnerability and have issued guidance on known affected versions, software upgrades, and patching. Details can be found here.
Important Note for SafeBreach Customers – Coverage for AA23-158A (CVE-2023-34362 MOVEit Vulnerability)
As soon as details were made available, the SafeBreach Labs teams mapped existing attacks and added new attacks to the Hacker’s Playbook immediately. It is important to note that existing SafeBreach customers already had a certain degree of coverage against some of the behavioral and IOC-based attacks being leveraged by TA505. Please run/ re-run the attacks listed below to ensure your environments are protected against this threat actor.
Existing IOC-based Attacks
- #8814 Write TrueBot (c0f8ae) downloader to disk
- #8815 Transfer of TrueBot (c0f8ae) downloader over HTTP/S
- #8816 Transfer of TrueBot (c0f8ae) downloader over HTTP/S
- #8817 Email TrueBot (c0f8ae) downloader as a ZIP attachment
- #8818 Email TrueBot (c0f8ae) downloader as a ZIP attachment
Existing and Updated Behavioral Attacks
- T1129 – Shared Modules
- #8364 Load custom shared module via LoadLibrary
- T1546.011 – Event Triggered Execution: Application Shimming
- #8022 Application Shimming
- T1055 – Process Injection
- #2246 Hooking of GetSystemTime function using mavinject.exe with a custom DLL
- #4136 Execute EXE file using process hollowing (PowerShell)
- #7220 Process Injection – Thread Execution Hijacking
- #8359 Process Injection – Asynchronous Procedure Calls
- #8358 Process Injection – KernelCallbackTable
- T1070 – Indicator Removal
- #8357 Clear RDP connections history (Windows)
- #7554 Clear Windows Event Logs
- #2302 Modify the timestamp of a file using Powershell
- #2245 Indicator Removal on Host (Windows)
- #2251 Network Share Connection Removal
- #2244 Windows Management Instrumentation Event Subscription
- T1574.002 – Hijack Execution Flow: DLL SideLoading
- #6809 Execute DLL by signed executable (igfxtray.exe)
- T1018 – Remote System Discovery
- #2222 Discover Remote Systems using PowerShell
- #6581 Discover domain computers using LDAP method
- T1021.002 – Remote Services: SMB/Windows Admin Shares
- #6483 Agentless lateral movement via SMB and RCE, using Token duplication
- #6513 Agentless lateral movement via SMB and RCE, using Mimikatz
- #6550 Agentless lateral movement via SMB and RCE, using Impersonated user
- T1113 – Screen Capture
- #8004 Capture Screen using Powershell
- #6411 Screen Capture (Windows)
- Meterpreter related attacks
- #7659 Pre-execution phase of Meterpreter malware
- #262 Remote Control using Meterpreter to Execute Persistence Commands
- #263 Remote Control using Meterpreter to Change System Configuration
- #264 Remote Control using Meterpreter to Execute File Commands
- #1042 Remote Control using Meterpreter to Execute File Commands
Newly Added IOC-Based Attacks
- #8940 Write LEMURLOOT (348e43) webshell to disk
- #8941 Transfer of LEMURLOOT (348e43) webshell over HTTP/S
- #8942 Transfer of LEMURLOOT (348e43) webshell over HTTP/S
- #8943 Email LEMURLOOT (348e43) webshell as a ZIP attachment
- #8944 Email LEMURLOOT (348e43) webshell as a ZIP attachment
- #8945 Write LEMURLOOT (0ea051) webshell to disk
- #8946 Transfer of LEMURLOOT (0ea051) webshell over HTTP/S
- #8947 Transfer of LEMURLOOT (0ea051) webshell over HTTP/S
- #8948 Email LEMURLOOT (0ea051) webshell as a ZIP attachment
- #8949 Email LEMURLOOT (0ea051) webshell as a ZIP attachment
- #8950 Write Truebot (0e3a14) downloader to disk
- #8951 Transfer of Truebot (0e3a14) downloader over HTTP/S
- #8952 Transfer of Truebot (0e3a14) downloader over HTTP/S
- #8953 Email Truebot (0e3a14) downloader as a ZIP attachment
- #8954 Email Truebot (0e3a14) downloader as a ZIP attachment
What You Should Do Now
The playbook has been updated with attacks that map to the IOCs identified in this US-CERT Alert. SafeBreach customers can now validate their security controls against these TTPs and IOCs in multiple ways.
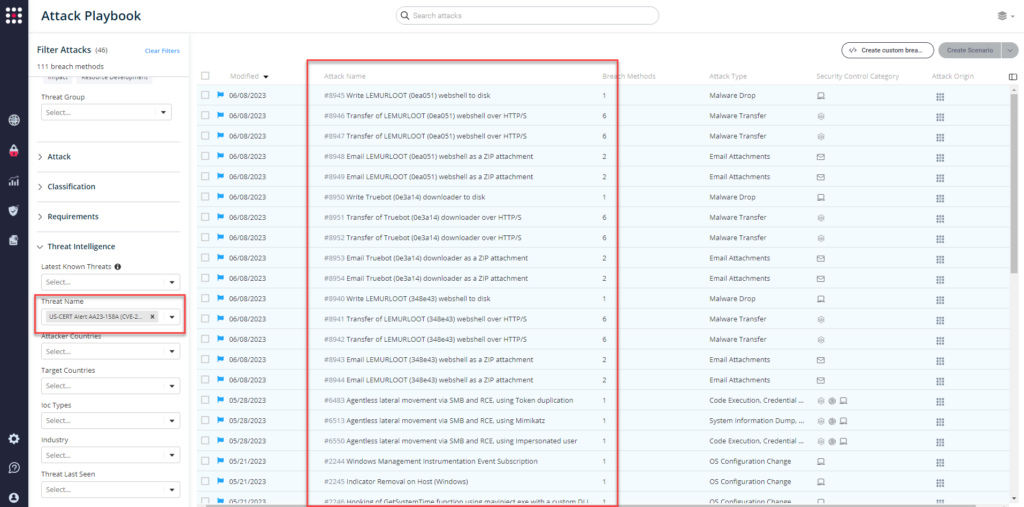
From the Attack Playbook, select and filter attacks related to US-CERT Alert AA23-158A. Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
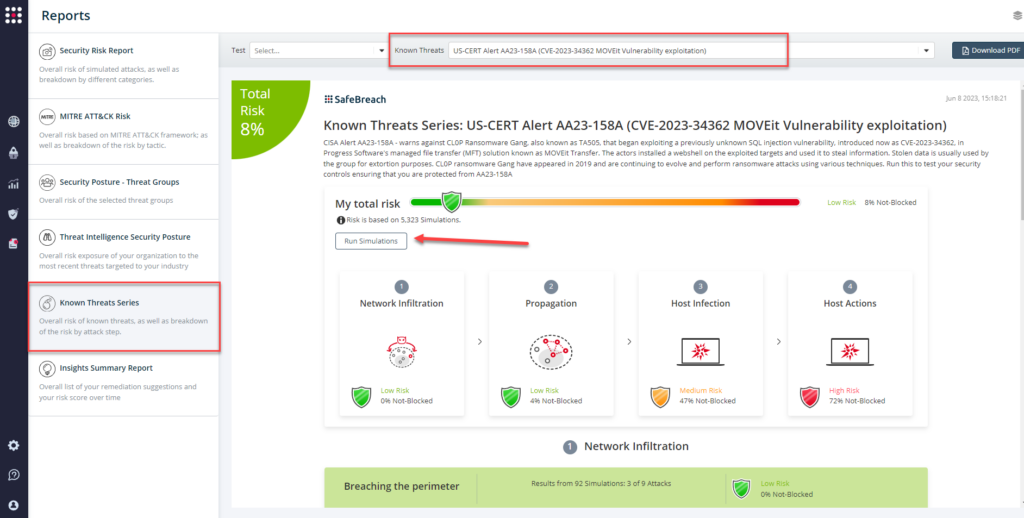
From the Known Attack Series report, select the AA23-158A (CVE-2023-34362 MOVEit Vulnerability exploitation) report and select Run Simulations which will run all attack methods.
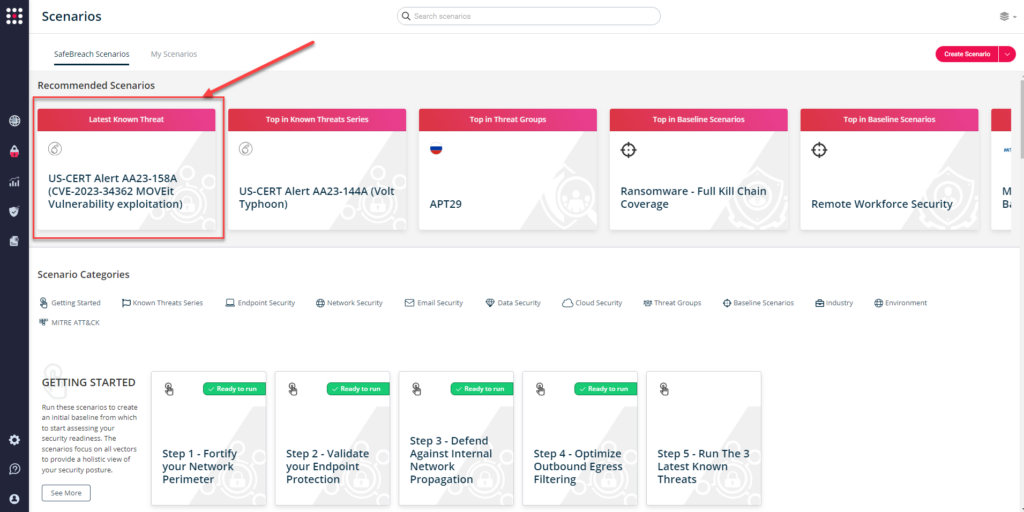
You can also go to “SafeBreach Scenarios” page and choose the AA23-158A (CVE-2023-34362 MOVEit Vulnerability exploitation) scenario from the list of available scenarios.
NOTE: CISA recommends continually validating your security program, at scale, in a production environment to ensure optimal performance against the growing threat of advanced cyber threats. Additional recommendations include:
- Reduce the threat of malicious actors using remote access tools by auditing remote access tools, reviewing logs for execution of remote access software, requiring authorized remote access solutions, and blocking both inbound and outbound connections on common remote access software ports.
- Implement application controls to manage and control the execution of software, including allowing listing remote access programs.
- Strictly limit the use of RDP and other remote desktop services.
- Disable command-line and scripting activities and permissions.
- Restrict the use of PowerShell, using Group Policy, and only grant to specific users on a case-by-case basis.
- For detailed information about mitigations and incident response, please refer to the full advisory
You Might Also Be Interested In
The post SafeBreach Coverage for US-CERT Alert (AA23-158A) – CVE-2023-3462 MOVEit Vulnerability appeared first on SafeBreach.
*** This is a Security Bloggers Network syndicated blog from SafeBreach authored by Kaustubh Jagtap. Read the original post at: https://www.safebreach.com/resources/blog/safebreach-coverage-for-us-cert-alert-aa23-158a-cve-2023-34362-moveit-vulnerability/