SafeBreach Coverage for Prestige Ransomware & Text4Shell Vulnerability (CVE-2022-42889)
The SafeBreach Platform has been updated with coverage for the newly discovered Prestige ransomware and the Text4Shell vulnerability (CVE-2022-42889). SafeBreach customers can select and run these attacks from the SafeBreach Hacker’s Playbook to ensure coverage against these advanced threats. Additional details about the threat and our coverage can be seen below.
to ensure coverage against these advanced threats. Additional details about the threat and our coverage can be seen below.
Prestige Ransomware
On October 11, researchers from the Microsoft Security Threat Intelligence Center (MSTIC) observed a threat campaign targeting transportation and other logistics industries in Ukraine and Poland. These targeted attacks involved the use of a novel ransomware variant labeling itself “Prestige ranusomware”.
According to the MSTIC, attackers had ransomware payloads deployed to all victim networks within one hour of each other using one of three methods. Some of the victims were previously targeted with HermeticWiper. MSTIC also noted that “Despite using similar deployment techniques, the campaign is distinct from recent destructive attacks leveraging AprilAxe (ArguePatch)/CaddyWiper or Foxblade (HermeticWiper) that have impacted multiple critical infrastructure organizations in Ukraine over the last two weeks.”
Technical Details
In all attacks, threat actors had already gained access to highly privileged credentials like DomainAdmin. It is thought that these credentials could have been acquired via a previous compromise. Three distinct methods were leveraged for ransomware deployment.
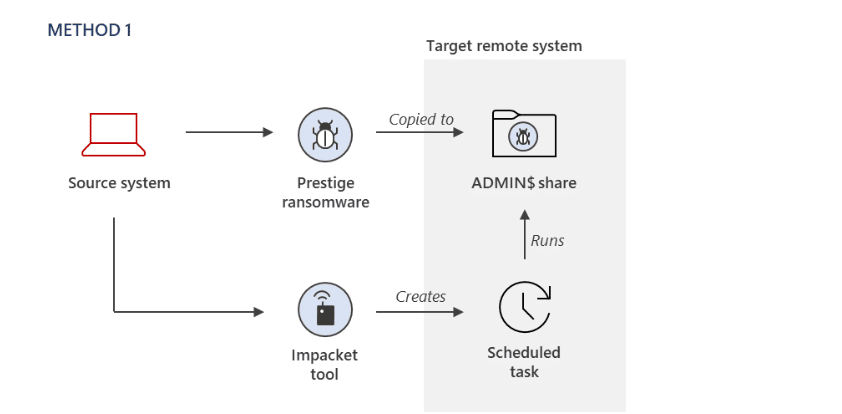
- Method 1 – The ransomware payload was copied to the ADMIN$ share of a remote system, and an open-source script-based tool for remote code execution called Impacket WMIexec was used to remotely create a Windows Scheduled Task to target systems and execute the malicious payload.
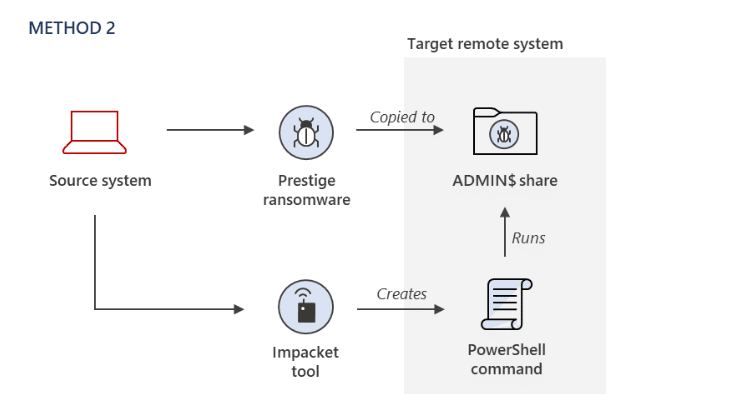
- Method 2 – The ransomware payload was copied to the ADMIN$ share of a remote system, and Impacket was used to remotely invoke an encoded PowerShell command on target systems to launch the malicious payload.
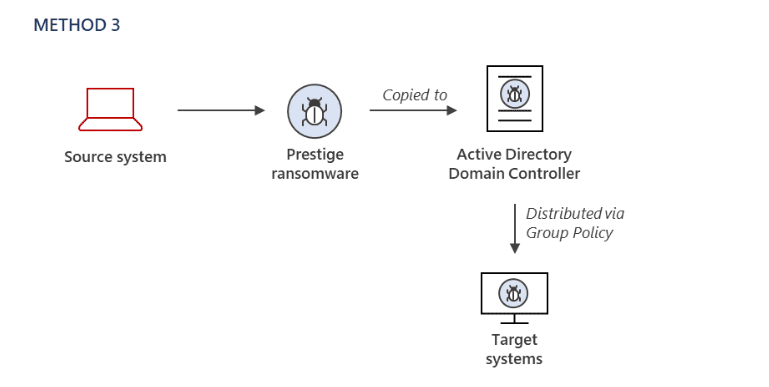
- Method 3 – The payload was copied to an Active Directory Domain Controller and was then deployed to the target systems using the Default Domain Group Policy Object.
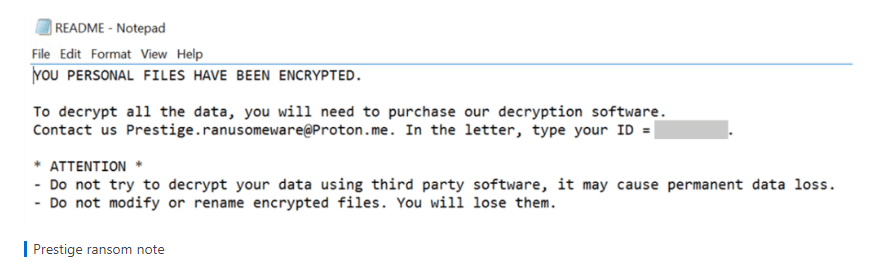
The Prestige ransomware requires administrative privileges to run, and it attempts to stop the MSSQL Windows service to ensure successful encryption. It also leaves the following ransom note in the root directory of each drive.
Lastly, Prestige deletes the backup catalog from the system to hinder system and file recovery.
SafeBreach Coverage of Prestige Ransomware
The SafeBreach platform has been updated with the following attacks to ensure our customers can validate their security controls against the new ransomware variant.
- #7324 Execute the Prestige Ransomware on user files (Host-Level)
- #7775 – Write Prestige malware to disk (Host-Level)
- #7776 – Transfer of Prestige malware over HTTP/S (Lateral Movement)
- #7777 – Transfer of Prestige malware over HTTP/S (Infiltration)
- #7778 – Email Prestige malware as a ZIP attachment (Lateral Movement)
- #7779 – Email Prestige malware as a ZIP attachment (Infiltration)
Text4Shell Vulnerability (CVE-2022-42889)
A security researcher has identified a critical new vulnerability CVE-2022-42889 that is similar to the previously identified Spring4Shell and the Log4Shell vulnerabilities. This vulnerability exists in v1.5 to v1.9 of the Apache Commons Text. This vulnerability arises from insecure defaults when Apache Commons Text performs variable interpolation, which basically is the process of looking up and evaluating string values in code that contain placeholders. This vulnerability can give unauthenticated attackers a way to remotely execute code on servers running applications with the affected component.
The Apache Software Foundation (ASF) released an updated version of the software (Apache Commons Text 1.10.0). NIST has urged users to upgrade to Apache Commons Text 1.10.0, which would disable the problematic interpolators by default.
SafeBreach Coverage of CVE-2022-42889
The SafeBreach platform has been updated with the following attack to ensure our customers can validate their security controls against the Text4Shell vulnerability
- #7816 – Remote exploitation of an Apache Commons Text library Text4Shell (CVE-2022-42889)
SafeBreach also recommends the following remediation actions to ensure better protection against this threat:
- Ensure network Intrusion Prevention System (IPS) is deployed on the network and configured with a policy to block known attack signatures. E.g., Apply a policy on the inspected traffic and set critical and high-confidence attack signatures to block and prevent the payload over the network. IPS signatures update policy should be set to update as promptly as possible and in accordance with the requirements set by the business.
- Identify encrypted traffic inspected by the network IPS and determine if the risk of having the encrypted traffic left uninspected is acceptable or it should be inspected to identify malicious payloads, traffic anomalies, and known attack signatures. Encrypted traffic can be inspected by installing the private keys used for the creation of the SSL\TLS communication or by implementing SSL offload and inspecting the clear traffic. The IPS vendor may suggest additional product-specific approaches to inspect encrypted traffic.
- If applicable, implement and configure a Web Application Firewall to inspect the traffic and apply a policy to block malicious payload.
Interested In Preparing Against Advanced Ransomware?
SafeBreach now offers a complimentary and customized real-world ransomware assessment (RansomwareRx) that can allow you to gain unparalleled visibility into how your security ecosystem responds at each stage of the defense process. This ransomware assessment includes:
- Training – Understand the methodology around ransomware attacks, persistent threats, and malware attacks.
- Assessment – Review goals and ensure simulation connection to our management console and all configurations are complete.
- Attack Scenario – Run safe-by-design, real-world ransomware attacks across the cyber kill chain on a single device of your choice.
- Report – Receive a custom-built report that includes simulation results and actionable remediation insights.
Empower your team to understand more about ransomware attacks, methodologies, and behaviors—all through the lens of the attacker. Request your complimentary RansomwareRx assessment today.
The post SafeBreach Coverage for Prestige Ransomware & Text4Shell Vulnerability (CVE-2022-42889) appeared first on SafeBreach.
*** This is a Security Bloggers Network syndicated blog from SafeBreach authored by Kaustubh Jagtap. Read the original post at: https://www.safebreach.com/resources/blog/safebreach-coverage-for-prestige-ransomware-and-text4shell-vulnerability-cve-2022-42889/





