Vulnerable MFA (MFA Prompt Bombing)

The term “MFA prompt bombing” is cropping up more and more in the security space, and while it sounds like yet another attack phrase coined for maximum scare value, the threat is real. HYPR has written extensively about one growing type of MFA prompt bombing — push attacks. That’s the technique used in the most recent hack of Uber.
With a valid username and password in hand — a trivial step when there are 15 billion compromised credentials floating around — the attacker essentially blasts the targeted victim with push notifications until the user accepts, granting the attacker access to the account. In this post, we look at the characteristics of MFA prompt bombing attacks and how businesses can reinforce their security infrastructure against them.
MFA Prompt Bombing on the Rise
Uber is only the most recent member of the dubious club of organizations that have been breached using MFA prompt bombing techniques. It’s a signature move by the Lapsus$ hacking group and it’s how hackers gained access to Cisco’s networks earlier this year. It’s also not a new technique. The Russian state-sponsored hacking group Cozy Bear has used this tactic in its attacks against businesses and governmental organizations across the globe.
The 2022 State of Passwordless Security report found a 33% year over year increase in these attacks, and that was based on data collected before Lapsus$ reared its head.
How MFA Prompt Bombing Works
MFA prompt attacks rely on the very human phenomenon of MFA fatigue. People typically log into many applications, systems and services each day using multiple authentication methods. Many MFA providers grant access by accepting a phone app push notification or receiving a phone call and pressing a key as a second factor. For example, Uber used push notifications through a Duo authenticator app. An attacker can usually issue multiple push notifications or keep calling until their request is finally accepted.
Throw in some additional social engineering interactions and it’s inevitable that at least some people will approve an illegitimate login. In the case of Uber, the attacker described their simple yet effective strategy:
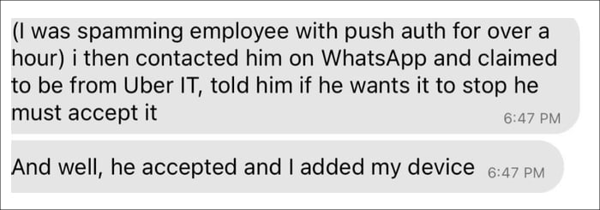 Source: Graham Cluely
Source: Graham Cluely
Common MFA Prompt Bombing Methods
The attacker obtains the initial username and password login credentials by obtaining them from online sources, brute force attacks or any of the other common methods to compromise passwords. The attacker uses those credentials to:
- Send a string of MFA prompts in order to irritate the target into finally accepting one to make it stop.
- Send one or two requests a day in order not to arouse suspicion from the target and detection by monitoring tools.
- If the attacker doesn’t have the initial login credentials, they can use a slightly more sophisticated process that gets the target to initiate the login process, for example by sending a phishing email, SMS or even a WhatsApp message. A possible such flow is illustrated below:
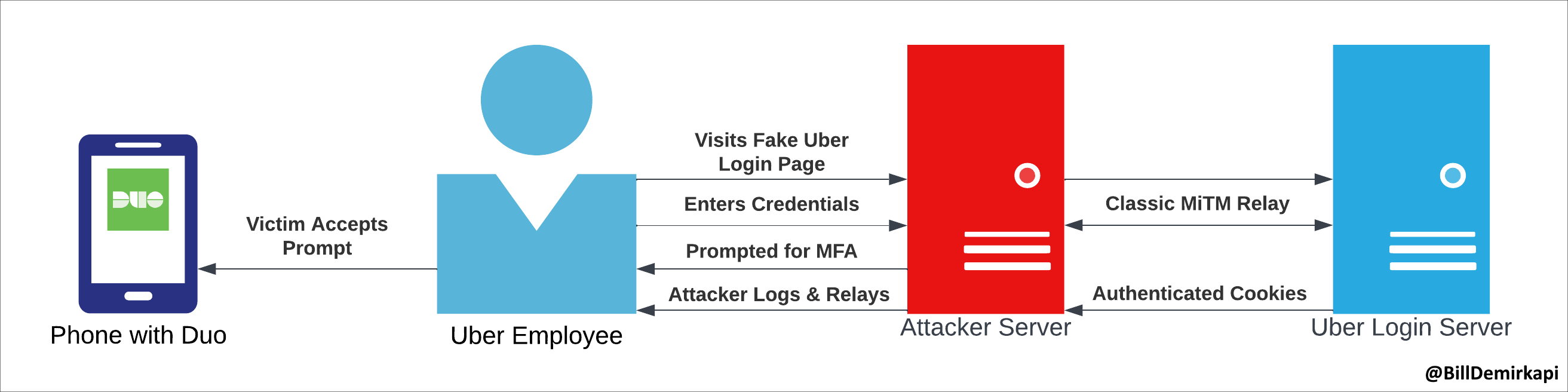 Diagram courtesy of @BillDemirkapi
Diagram courtesy of @BillDemirkapi
Once hackers gain account access, they can add their device to the account and/or change the credentials and lock out the account owner. Depending on the victim’s permissions, they can then access connected resources and systems, upload infostealers or other malware, and find system vulnerabilities to exploit.
Mitigation measures
There are a few basic steps you can take to decrease the likelihood of a successful MFA prompt bombing attack.
- Improve awareness of MFA spamming/ social engineering attacks: Conduct user training on malicious MFA notifications and techniques attackers use.
- Limit the number of MFA requests your system allows to be sent.
- Require additional context
- Implement monitoring and warning mechanisms to detect suspicious MFA prompt activity.
However, some of these measures can create user friction and confusion and none of them are really effective as they don’t address the root cause. Namely, the MFA methods themselves.
Vulnerable MFA Puts Organizations at Risk
Prompt bombing is not the only way to bypass traditional MFA. Last month the 0ktapus attacks grabbed headlines, with attackers breaching Okta-native authentication controls to gain access to the Okta SSO instances of more than 130 organizations. You can listen to a podcast on the 0ktapus attacks here (disclaimer: I’m one of the hosts).
What the Uber breach, the 0ktapus attacks and others really show is something we already knew — any security method that expects people to be the gatekeeper will be vulnerable. The latest Verizon DBIR found that 82% of successful cyberattacks involve the human element.
While any MFA is better than none, legacy password and MFA combinations, which require people to become secret keepers and evolving attack detectors, simply are not sufficient. The only real solution is to use phishing-resistant MFA as recommended by the OMB and CISA.
Passwordless MFA Eliminates MFA Prompt Bombing
Fully passwordless MFA based on FIDO standards meets the definition of phishing resistance set by CISA and does not have any secrets that can be phished or intercepted.
Some solutions providers support some level of FIDO authentication, but use vulnerable methods as fallbacks, which attackers are quick to take advantage of. These are not fully passwordless MFA.
Passwordless MFA that supports QR code scanning, like HYPR True Passwordless™ MFA, provides the strongest protection against MFA fatigue attacks as it eliminates the attack vector entirely. Additionally, a FIDO2 Token coupled with HYPR can produce a phishing-resistant authentication flow, mitigating this attack vector across the array of enterprise use cases.
One of the most worrisome parts of the Uber attacks was that the hacker appears to have gained access to Uber’s Privileged Account Managed solution, which could give broad access to the most sensitive systems. Privileged account management systems are one of the first things that should be protected with passwordless MFA solutions.
With all this, it should be remembered that Uber is not alone and the company and its employees are by no means to blame for their attacker’s actions. Especially as they followed the majority of commonly accepted authentication security practices. We wish their security and response teams the best in these challenging days.
As @IanColdwater so aptly put it: “If phishing a single employee can lead to everything in your infrastructure being compromised that easily, that employee is not to blame.”
![]()
*** This is a Security Bloggers Network syndicated blog from HYPR Blog authored by Ryan Rowcliffe, Field CTO, HYPR. Read the original post at: https://blog.hypr.com/mfa-prompt-bombing






