The Rise of Mobile Phishing and How to Handle It
The pandemic has revolutionized the way we communicate. Gone are the days when we had to get off the couch to talk with coworkers and employees. Nowadays, you just need access to a cell phone to Zoom, send emails, and schedule meetings. This convenience comes at a price, though.
With over 15 billion cell phones in the world, it’s no wonder that malicious actors turn to mobile devices to steal data and private information. Remote work and BYOD cultures have paved an even easier path for hackers to target enterprise employees. One of the most damaging attacks: mobile phishing.
Phishing attacks have been around since the mid-1990s when they originally targeted emails. Today, they’re more sophisticated and becoming more prevalent on mobile devices. The high frequency at which mobile phishing attacks occur means more work for security operations center (SOC) teams to manage. Continue reading to learn more about the growing threat of mobile phishing and how to handle it.
What Is Mobile Phishing?
Mobile phishing is a type of phishing attack that uses mobile devices, such as smartphones and tablets, to deliver malicious content. Historically, phishing attacks have been conducted through email messages and web pages. However, as the internet has become increasingly mobile-friendly and people are spending more time on their phones than ever before (for example, Americans spend almost 4.8 hours a day on their smartphones), cybercriminals have turned their attention to this new avenue for victimizing users.
Mobile phishing attacks may be harder to detect because they extend beyond regular email phishing. SMS-based attacks (smishing), malicious voice calls (vishing), and app-based phishing have exploded in popularity – and severity. And they’re harder to defend against because they’re designed specifically for mobile devices and rely on your trust in legitimate apps you already use regularly:
-
SMS/text messaging – phishing texts commonly impersonate banking apps, shipping providers, and even your CEO.
-
Voice mails – it’s more than your car’s extended warranty, vishing attacks will mimic the IRS, loan providers, and more.
-
Facebook Messenger – beware of suspicious links in messages, even from your Facebook Friends.
-
WhatsApp – attacks can target victims within the app and via email.
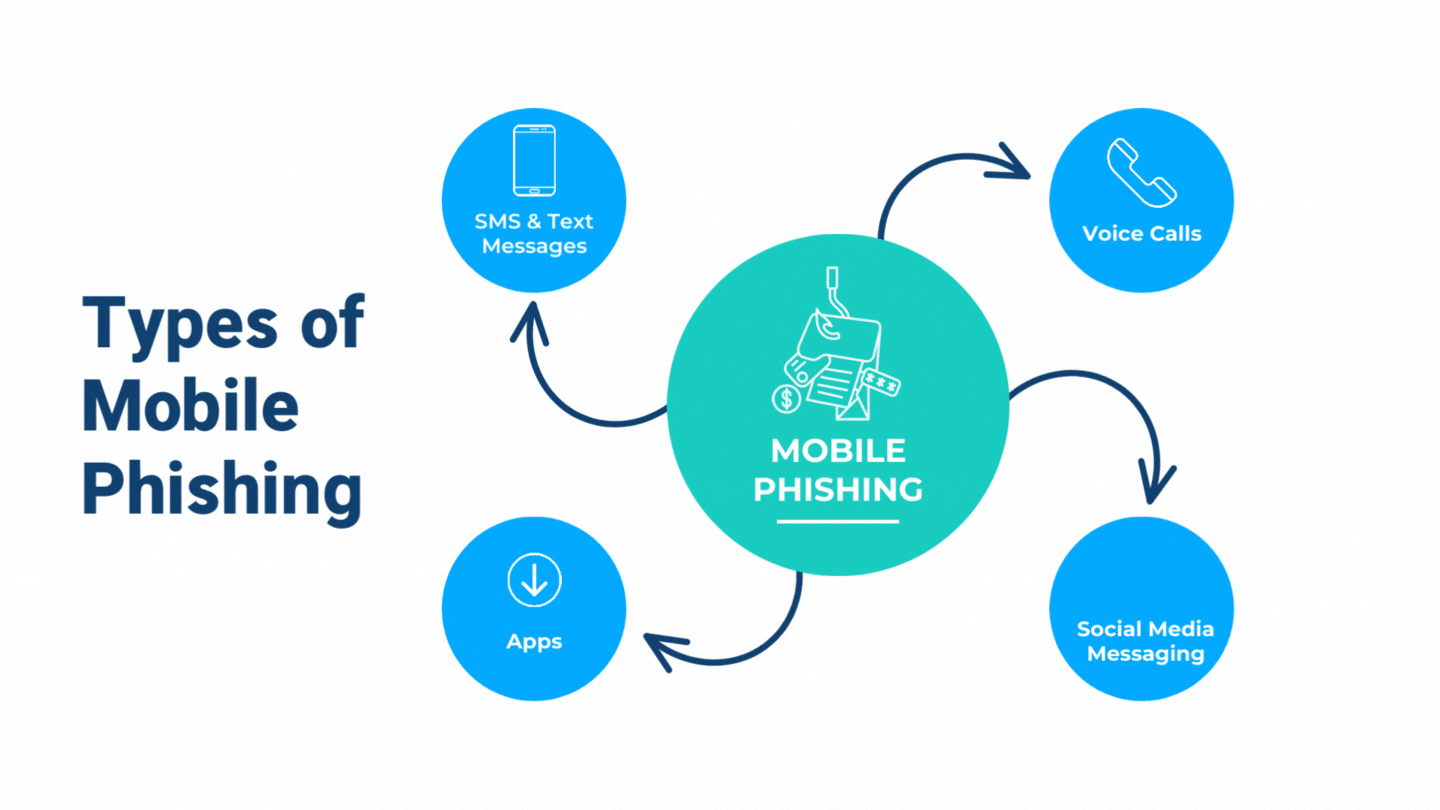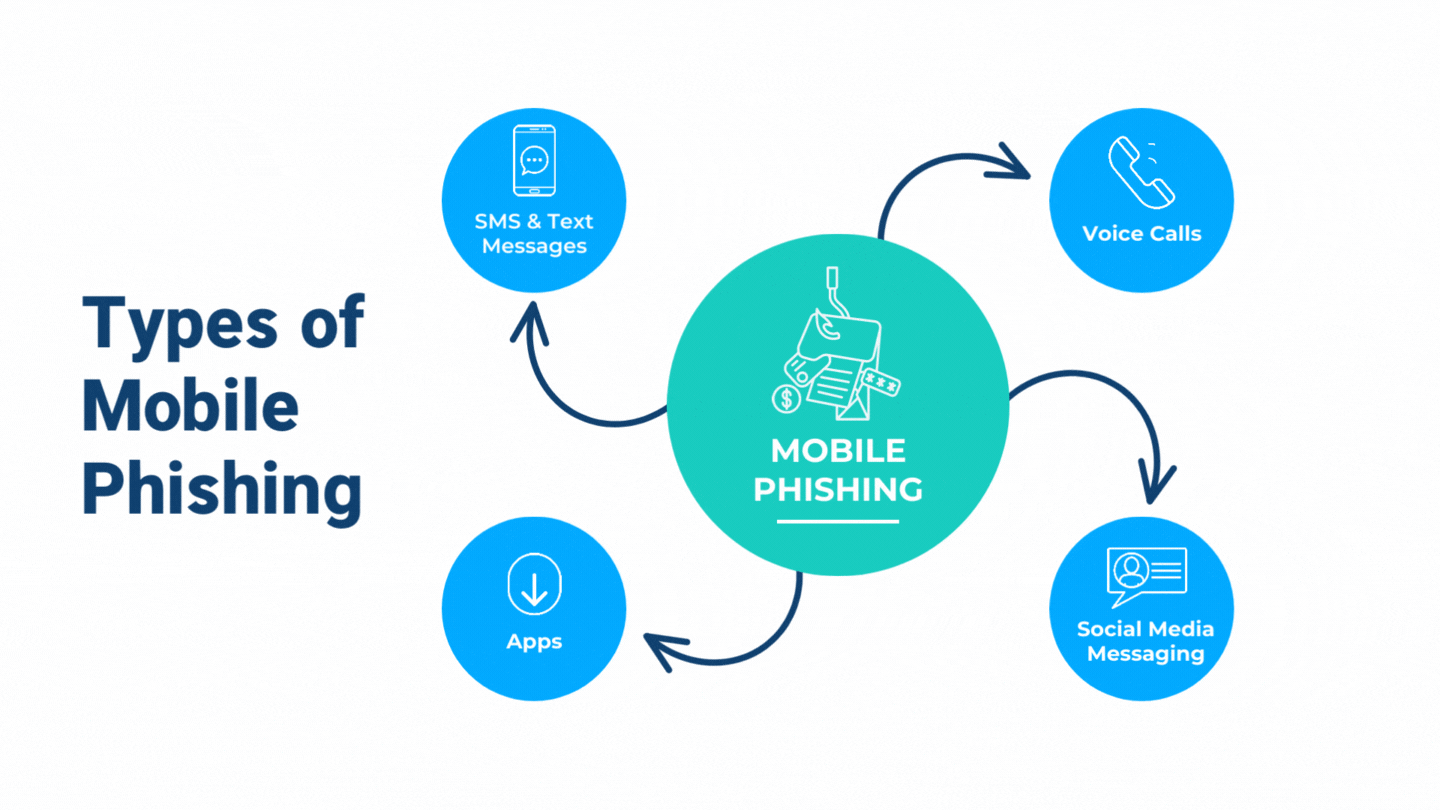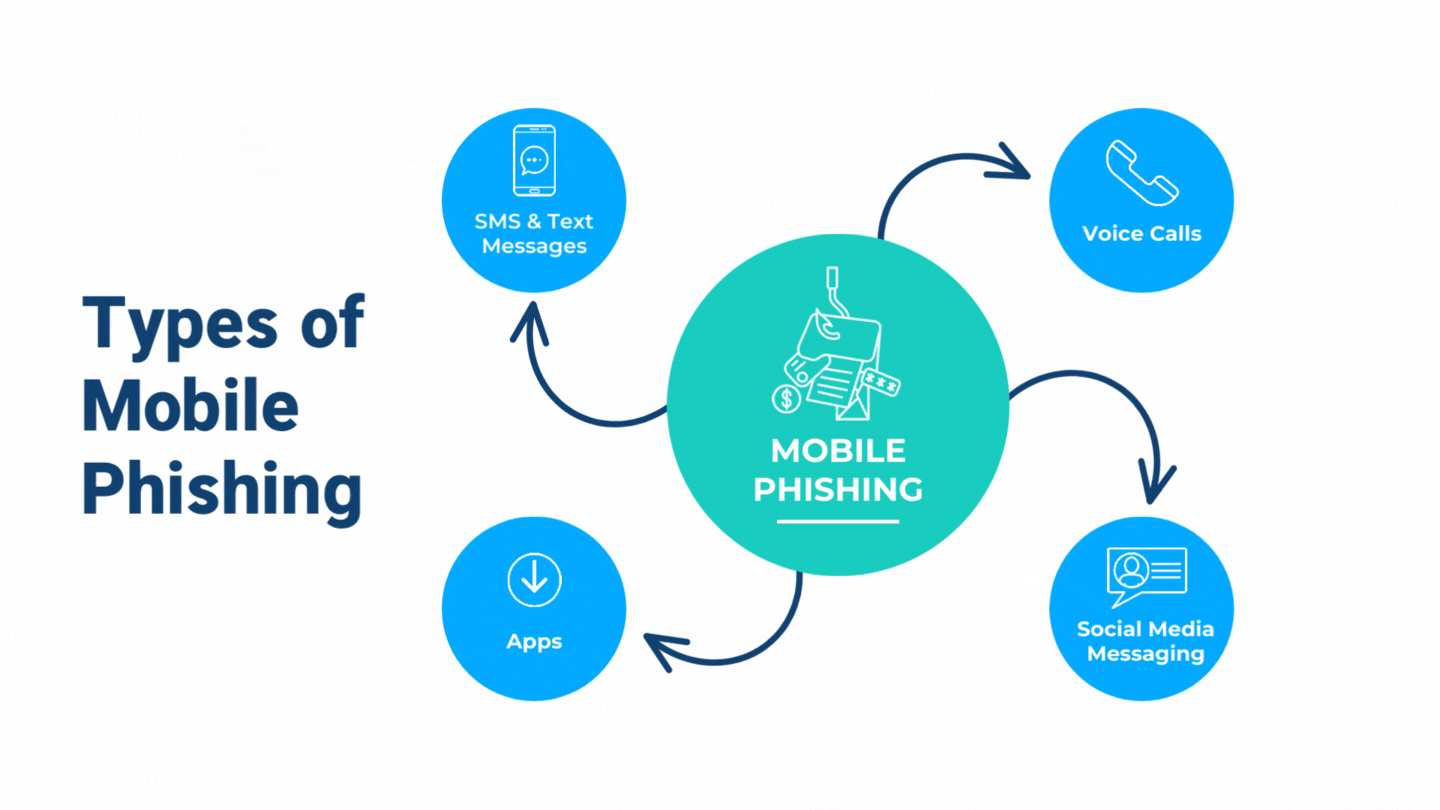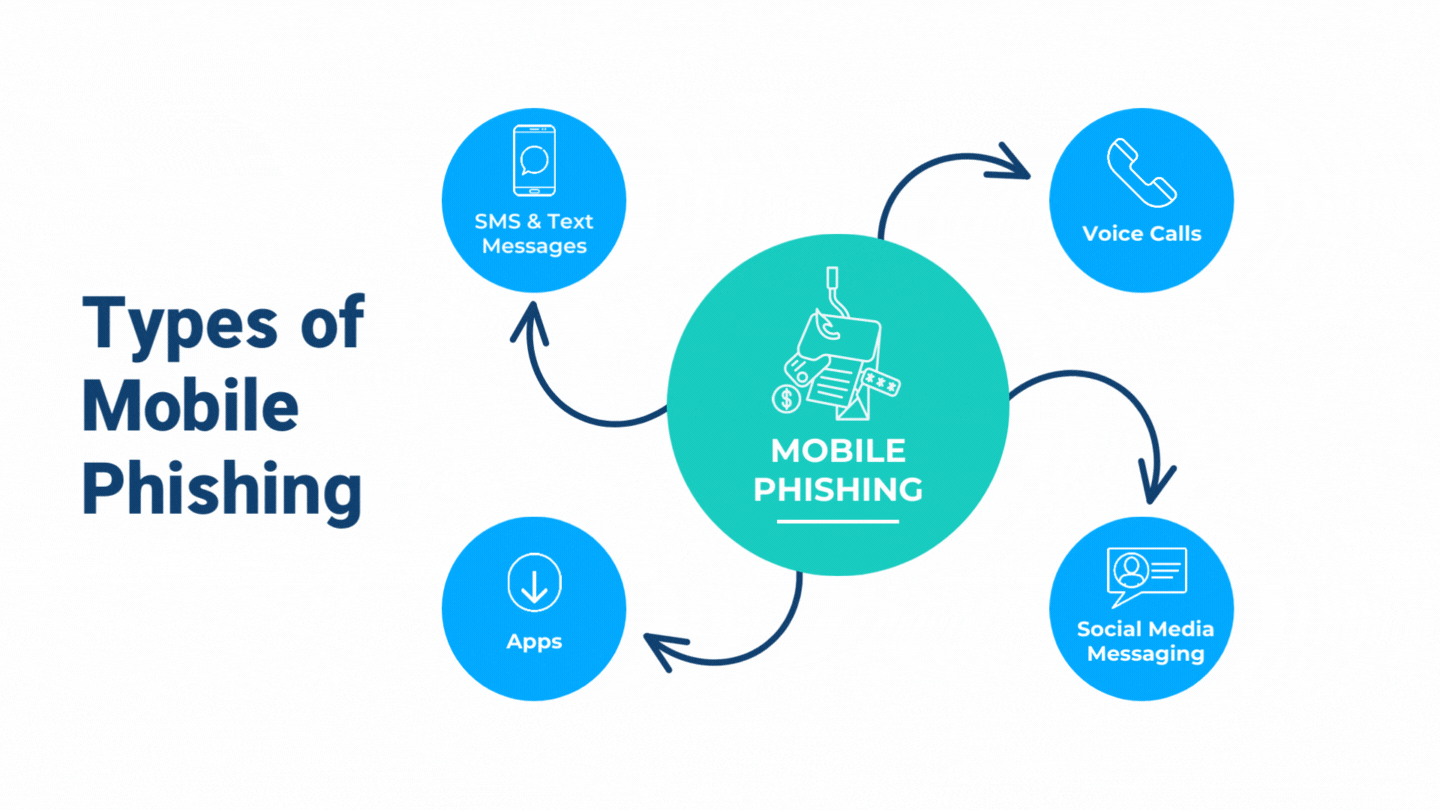
What Makes Mobile Phishing Different From Traditional Phishing?
The difference between mobile phishing and traditional phishing is simple: the medium. While traditional phishing emails are sent through email, mobile phone phishing takes advantage of the fact that many people use their phones for banking, shopping, and business. This expanded attack surface includes SMS/text messaging, phone calls, voice mails, apps, and social media platforms.
Mobile Phishing Statistics
-
74% of companies faced smishing attacks last year.
-
In 2021, 61% of surveyed companies dealt with social media phishing attacks.
-
51% of organizations allow employees to access corporate applications on their personal mobile devices.
-
Phishing attacks on mobile devices have grown at a consistent rate of 85% annually.
-
42% of organizations report that vulnerabilities in mobile devices and web applications have led to a security incident.
-
75% of the phishing sites specifically targeted mobile devices.
-
There are almost 75x more phishing sites than malware sites on the internet, according to Google Safe Browsing.
-
The Bank of Ireland was forced to pay out €800,000 to 300 bank customers as the result of a single smishing attack.
Your Mobile Phishing Response Checklist
Mobile phishing scams happen around the clock, so make sure your defense is always ready. Here are a few areas to consider for your phishing defense and response:
-
Educate Employees: Prevention is your best defense. Ensure that mobile phishing safety is included in regular employee security training. Highlight common red flags and real-life examples so that employees know what to look out for. Establishing a security-first culture within your organization can reduce the number of successful phishing attacks.
-
Collect Evidence: Encourage employees to send screenshots of any malicious texts, messages, and emails from the targeted mobile device (and remind them to block the sender). If an employee falls victim to a phishing attempt, it’s critical to know what the successful attack looked like.
-
Analyze Data: Your security team can quickly identify attack trends once enough data is collected. For instance, if you notice an uptick in smishing attacks that impersonate the CEO, that is a great opportunity to send out company-wide security alerts.
-
Have an Incident Response Plan: Did an employee click a bad link or share private information? Then it’s go time – activate your IR procedures. Make sure that your team has documentation of what steps to follow: anything from quarantining devices, to searching internal systems, to reviewing logs for other affected users.
-
Establish a BYOD Policy: Creating a Bring Your Own Device policy is a necessity, whether in-office, hybrid, or remote. Include parameters around employee offboarding, device loss, theft, and device updates.
Triage Phishing with Modern Tools:
Security Automation
Mobile phishing attacks will continue to grow in frequency and sophistication. Remote work and our reliance on mobile devices will fuel these attacks even more. And with security teams receiving thousands of alerts daily, leaders are on the search for options to stay ahead of phishing threats.
Security automation platforms offer solutions to combat the rise of mobile phishing attacks. Benefits of automation include:
-
Save SOC analyst time with automatic investigation and quarantine
-
Gain visibility into phishing attempts from the dashboard
-
Block false positives with entirely automated workflows
-
Increase efficiency with real-time case collaboration
-
Improve security metrics, such as reducing mean time to resolve (MTTR)
The purpose of adding automation is to empower SOC teams to stop more threats faster. These platforms automate the repetitive, mundane tasks that suck time away from SOC analysts.
Watch how low-code security automation can be used to triage phishing alerts.
Whether you introduce security automation into your SOC or establish a manual IR process, mobile phishing needs to be on your threat radar. Educate employees, secure the growing attack surface, and have a thorough incident response process.
*** This is a Security Bloggers Network syndicated blog from Swimlane (en-US) authored by Ashlyn Eperjesi. Read the original post at: https://swimlane.com/blog/mobile-phishing/





