Mergers and Acquisitions in API Security and Bot Management
Continued Consolidation in API Security and Bot Management – A Need for Unified API Protection
As we have seen of late, in attempts to offer end-to-end application protection, web application firewall (WAF) vendors have been acquiring bot management companies. Examples of this activity include Imperva and Distil Networks, and F5 and Shape. However, the merging of two bot management companies, the industry didn’t necessarily see coming. But the rise of bot attacks is increasing the need for organizations to look to protect their organization from theft, fraud, and disruption. This means not only protection from sophisticated bots that exploit API vulnerabilities but also other kinds of API attacks that use business logic abuse and automated attacks such as ATO, credential theft, DDoS, and content scraping. We believe there will be continued consolidation of point solutions such as bot management, but customers’ needs will only be met by a solution that covers the entire API protection lifecycle which involves achieving visibility into all APIs, including public-facing, internal and unmanaged, and the mitigation of API vulnerabilities, ensuring API compliance, and the detection and prevention of attacks on APIs.
As pointed out by Sandy Carielli, Principal Analyst at Forrester, in a blog post, and an evaluation of the bot management company’s acquisition, the number of bot management specialists continues to decrease as they are acquired by WAF or API security vendors or they expand their own offerings. HUMAN and PerimeterX are two of the remaining bot management specialists — neither has WAF or API protection capabilities. The WAF and API protection gap is one that HUMAN will need to address soon, either through partnership, acquisition, or homegrown development.
According to Gartner, APIs have bubbled to the top as the #1 attack vector for web applications1 supporting the hypothesis that while bot management is important, unmanaged, and unsecured APIs are as important, providing easy targets for attacks, and resulting in security and privacy incidents. And with more than half of businesses having between 50 and 500 APIs deployed, either internally or publicly, while some have over a thousand active APIs2, security breaches related to APIs can be a constant challenge with the scale of use of APIs being enormous. Of the 21.1 billion transactions analyzed by Cequence Security in the last half of 2021, 14 billion were API transactions.
Click here to request a free API Protection assessment to get an attacker’s view
into your organization.
Complicating matters is that there’s over three million open cybersecurity jobs and this lack of skilled cybersecurity professionals is cited as the number one factor in securing web applications3.
The selection of a bot management-only point solution by businesses, along with the huge volumes of API transactions, and a lack of skilled personnel has resulted in gaps in protecting APIs.
Automated bot attacks involve large-scale campaigns that are used by attackers to disrupt services, steal credentials, and gain unauthorized access to critical systems. Shopping bots are technically sophisticated bots, and their use is driven primarily by the revenue opportunity in secondary markets for high demand items such as sneakers, game consoles, luxury products, and graphics cards.
These automated attacks hide in plain sight, masking themselves as legitimate transactions, making the block or not decision difficult for security teams. Organizations try to stay one step ahead with bot management solutions to continually track sophisticated bot attacks, even as attackers retool to avoid detection can help close the automated bot attack gap.
However, bot management is only the tip of the iceberg when it comes to API security for every aspect of the API protection lifecycle.
To stay ahead of sophisticated and relentless attackers, what’s needed for an effective API protection program is not just a bot management solution. And no amount of industry consolidation of these solutions will help.
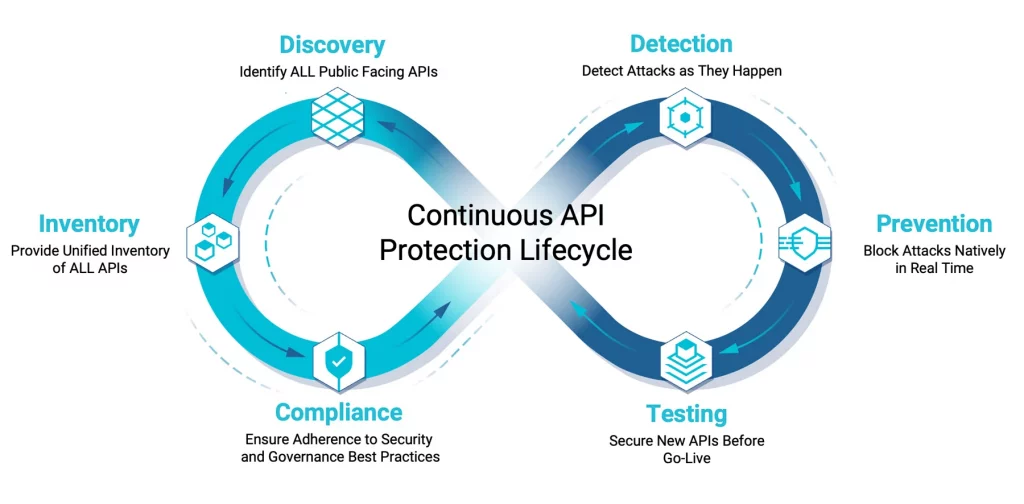
An effective program involves a continuous API protection lifecycle that starts with discovery and inventory of all your APIs. How can you detect and protect automated bot attacks on APIs that you don’t even know about? You might have a great handle on internal APIs but what about those 3rd-party APIs hosted elsewhere? Or the fact that developers are constantly developing and deploying new applications and APIs?
In addition, you must be able to continuously assesses your public facing APIs and resources to show you exactly what an attacker sees from an outside-in perspective such as sub-domains, the cloud hosting service in use, any associated API endpoints, and the servers that may be exploitable using vulnerabilities such as Log4j and LoNg4J.
Click here to request a free API Protection assessment to get an attacker’s view
into your organization.
Beyond that tip of the iceberg, you’ll need an inside-out view of your APIs by integrating with any network infrastructure element to create an up-to-the-minute catalog of all your APIs, managed, unmanaged. Then, adding predefined ML-based risk assessment rules help uncover sensitive data handling, weak or missing authentication, and specification conformance coding errors for remediation. Having this will also help you achieve compliance assessment and remediation against best practices and standards.
Then, you can add in the detection of sophisticated and persistent attackers and their always changing attacks through native, real-time attack detection, which leverages ML, AI, and global API threat intelligence to fingerprint and identify attacks well beyond the OWASP API Top Ten, and evadable, least common denominator Domain-based signatures. As important, your API protection lifecycle will include inline stealthy and native mitigation that uses behavioral fingerprints to block threats with unmatched efficacy, regardless of the evasive tactic employed, leveraging a threat database comprised of threat patterns observed, known malicious infrastructure used and 3rd-party threat intelligence continuously analyzed for out-of-the-box protection.
This is what the complete “iceberg” would look like. No matter where you are in your API protection lifecycle, you’ll have all the components you need versus only point solutions.
To get more insights into how to protect your organization from Bot and API attacks request a free assessment or read our blog Why Unified API Protection – A Solution Whose Time Has Come.
1 Gartner Webinar – API Security: Protect your APIs from Attacks and Data Breaches
2 Marsh McLennan Cyber Risk Analytics Center
3 World Economic Forum (WEF)
The post Mergers and Acquisitions in API Security and Bot Management appeared first on Cequence Security.
*** This is a Security Bloggers Network syndicated blog from Cequence Security authored by Tony Bailey. Read the original post at: https://www.cequence.ai/blog/mergers-and-acquisitions-in-api-security-and-bot-management/





