Automox Allies With Rapid7 to Automate Patch Management
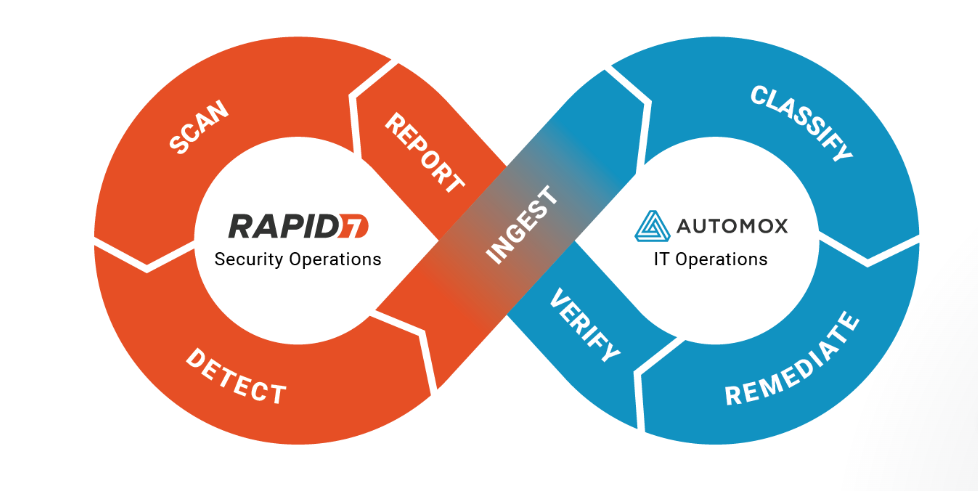
Automox this week at the RSAC 2022 event launched an automated vulnerability identification and remediation platform in collaboration with Rapid7, a provider of a cloud platform for assessing the severity of vulnerabilities.
Paul Zimski, vice president of product strategy for Automox, said the combined capabilities of the two companies will enable cybersecurity teams to remediate security vulnerabilities using an Automox Automated Vulnerability Remediation (AVR) platform without needing to wait for a developer to patch an application.
Automox makes use of a lightweight agent to enable cybersecurity teams to make use of Worklets, a set of scripts created using PowerShell and Bash tools that are reusable across Windows, Linux and macOS devices.
A recent Automox survey found 93% of respondents still rely on some degree of labor-intensive scripting to automate endpoint management. A full 84% said there’s room for improvement in managing endpoints. Historically, the major cybersecurity challenge is that organizations have been reluctant to automatically patch applications for fear of breaking them.
However, Zimski said there are large numbers of patches that could be automatically applied without the aid of a developer. Organizations need to strike a balance between cybersecurity and any potential operational disruption that might result from patching applications faster. A large percentage of the cybersecurity incidents that most organizations involve known vulnerabilities that cybercriminals have exploited within an application that was kept current.
Zimski said the Automox approach dramatically reduces the mean-time-to-remediate (MTTR) in a way that alleviates the need to add additional tasks to a developer’s workload. Too many organizations are suffering from “learned helplessness” that stems from cybersecurity teams feeling they always need to rely on a developer to address any application issue, he added.
The Automox approach to automating patch management is arriving at a time when many organizations are reviewing their software supply chain processes. In theory, responsibility for application security is shifting further left toward development teams that build and deploy applications. However, it’s not clear to what degree organizations are embracing DevSecOps best practices to achieve that goal. The average developer has a limited amount of cybersecurity expertise, and the more developers there are on a team the more likely it’s one of them will make a mistake. As such, there will always be a need for cybersecurity teams to review applications for vulnerabilities.
The challenge, of course, has always been the cultural divide that exists between cybersecurity teams and application developers. Cybersecurity teams have, for the most part, never been fully integrated within application development and deployment workflows. The tools cybersecurity teams use to discover vulnerabilities are not easily integrated with the DevOps workflows that many organizations use to build applications. Automox isn’t making a case against DevSecOps as much as it is providing a way to automatically implement most routine patches on endpoint devices.
It’s too early to say what the right balance of responsibility for security will be. It will likely vary widely from one organization to the next. The one thing that is clear is that, given the number of applications that are not being kept up-to-date, the current approach to application security isn’t working.