Nation State Actors Target Vulnerabilities in Critical Infrastructure
Conti Leaks Confirm Ransomware Gang’s Nation State Connection to Russia
In the past two years, the innovative and formidable Conti ransomware gang has wrought havoc across 1000+ US and international organizations, making themselves a mainstream name across the cybersecurity community. The group recently made headlines again with the infamous Conti leaks, which turned the tables back on the ransomware group, revealing thousands of internal messages as well as its “most prized possession of all,” the source code of its ransomware. The leaks are thought to be an act of retaliation against Conti’s pro-Russia stance following its invasion of Ukraine. Given this latest news regarding one of the most ruthless ransomware-as-a-service groups (RaaS), we wanted to look at its history of attacking critical infrastructure organizations across the globe and examine lessons in cybersecurity operations that all businesses, but especially critical infrastructure organizations, can take away.
“To say your organization should be aware of the Conti gang, and ransomware attacks in general, cannot be overstated,” noted Gerald Auger at SimplyCyber. During the past two years, Conti has collected over $150 million dollars in ransom payments. Businesses with poorly configured systems, sprawling attack surface(s), immature privileged access control, and intertwined IT/OT environments are appetizing prey for hackers. Further, from an impact perspective, Conti typically focuses its efforts on sizeable critical infrastructure targets to accelerate ransom payments. According to CISA, Conti actors are known to exploit legitimate remote monitoring and management software and remote desktop software as backdoors to maintain persistence. What makes Conti different from other RaaS factions is that its developers pay the virus deployers a wage in addition to a percentage of the proceeds from successful attacks. This increased incentivization has made being a part of Conti even more lucrative. Additionally, there is ample evidence that Conti is a group of nation-state actors with ties to the FSB, Russia’s main internal security service, adding to the motivations behind its hacking activities and making it more likely to put effort into “big game hunting,” by hacking high-profile targets.
Critical Infrastructure Under Assault
With the current geopolitical tensions, repeated supply chain issues, and rising inflation, the last thing any business or government organization wants is to face the threat of ransomware. Yet, critical infrastructure organizations are highly susceptible and have become the focus of Conti’s ransomware attacks. Early in the COVID19 pandemic, Conti targeted healthcare organizations such as the Irish healthcare system. This led to the cancellation of dozens of outpatient services, inoperable vaccine portals, and many weeks of service restoration. Ultimately, Ireland declined to pay the $20M ransom, deciding to incur the costs of restoring services instead. After all was said and done, Ireland’s recovery and restoration costs added up to an estimated $100M.
Today, Conti actors have shifted gears, focusing on oil & gas, manufacturing, and government-dependent systems to disrupt the delivery of essential goods and services. To find an example, one need only look to the RaaS gang’s more recent attack on Costa Rica. This breach caused the Central American country to declare a state of emergency as the attack disrupted essential government operations, including tax collection, exports and customs services, payment for government employees, and more. As former President Carlos Alvarado publicly declined to pay the $10M ransom, 672GB of data was exfiltrated and released on a Conti affiliated website.
Whether an organization pays the ransom in such a scenario is a difficult decision that depends on countless factors unique to every business and organization. It seems an impossible task, yet in these instances, it is possible to be prepared with an estimation and understanding of the financial cost for each risk scenario. With Axio’s Risk Quantification Methodology, business leaders can consider the secondary risks when faced with a ransomware attack by quantifying a Conti ransomware scenario:
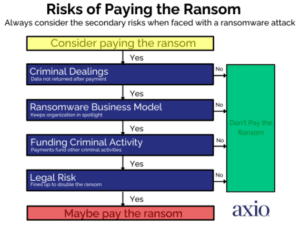
Understanding the range of impacts makes it much easier to select the best types of controls to reduce the fiduciary impact if a Conti event threatens your business and recovery will be quicker.
Given the great number of insights and data available from the number of Conti (and other ransomware groups’) victims, we can leverage that data to help you prepare for a similar attack. Some prioritized actions Axio can help with:
- Know how susceptible you are
- Model out cost scenarios
- Select the best improvements for your business; AND
- Get started with a ransomware preparedness assessment today.
Threat actors aren’t going anywhere, and they’ll only continue to increase the frequency and sophistication of their attacks. Critical infrastructure organizations have no time to lose. Take the necessary steps today to lower your cyber risk exposure and strengthen your cybersecurity posture. Check out Axio’s free tool to assess your risk preparedness. For a deeper dive into ransomware and its implications to businesses across the globe, you can view Axio’s 2021 State of Ransomware Preparedness Report. Finally, if you’d like to speak with one of Axio’s critical infrastructure experts, please contact us.
*** This is a Security Bloggers Network syndicated blog from Axio authored by Axio. Read the original post at: https://axio.com/insights/nation-state-actors-target-vulnerabilities-in-critical-infrastructure/




