Home » Cybersecurity » Threats & Breaches » Vulnerabilities » Log4shell by the numbers- Why did CVE-2021-44228 set the Internet on Fire?
Log4shell by the numbers- Why did CVE-2021-44228 set the Internet on Fire?
On Friday, the news broke about Log4Shell, an easy-to-exploit vulnerability being exploited across the world. We have kept our blog from Friday up to date with the latest news, mitigations and strategies that you can take as a maintainer or operator of software using log4j.
The news is big enough to have been featured in the media, and the crunch has been felt by industry insiders – but there are a few unanswered questions. Why exactly is this so widespread?
Sonatype are the stewards of the default location for most Java software to fetch their components: the Maven Central Repository. It’s also the go-to-destination for producers of open source to distribute their products. As such, we have been diving into download statistics to see how quickly the transition from vulnerable to fixed versions is happening.
Firstly, how popular is Log4j exactly?
When looking at download statistics for the affected coordinates at org.apache.logging.log4j :log4j-core over a period of the last 4 months, we observe 28.6 million downloads to date.
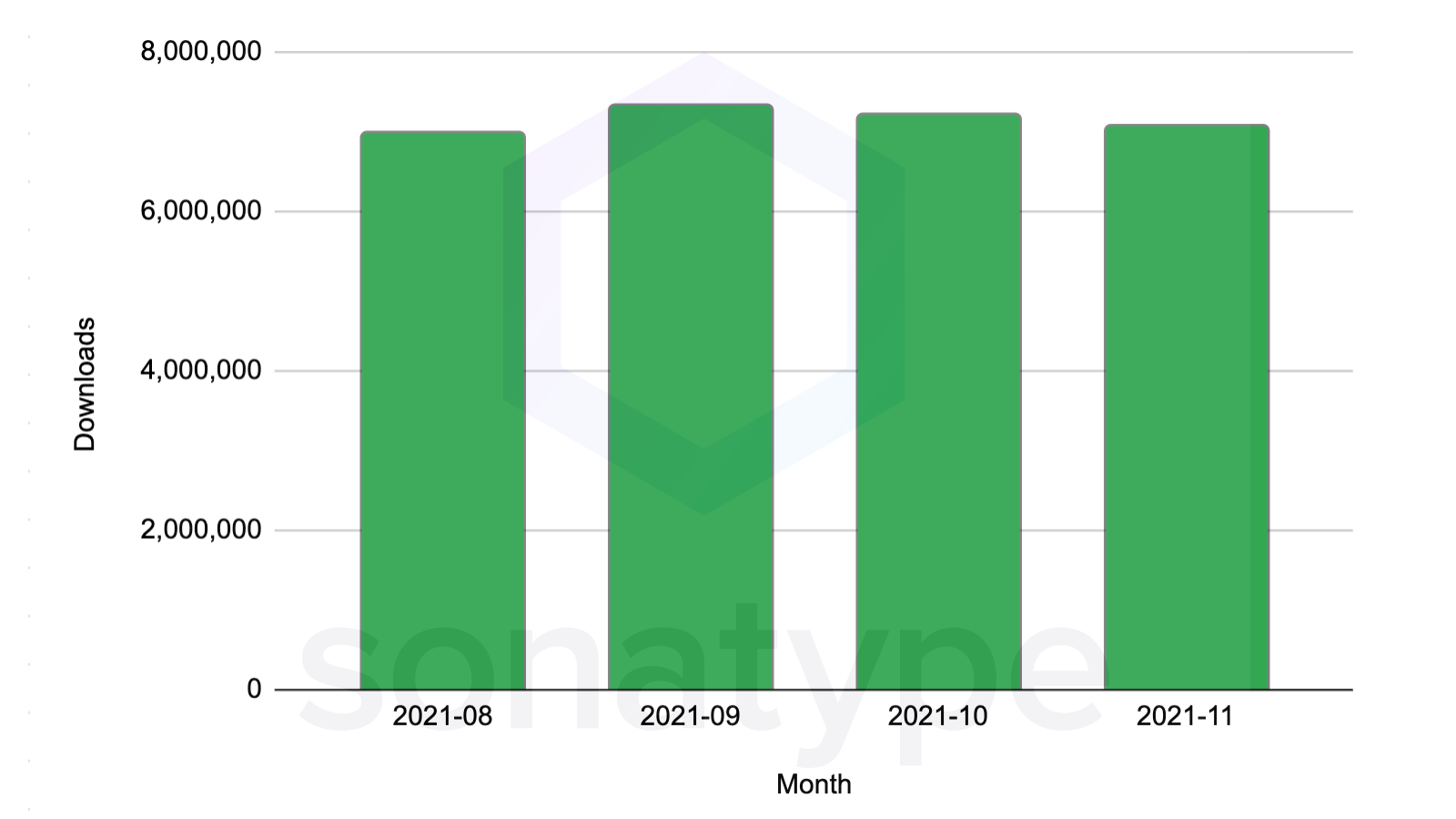
log4j-core is the top 252nd most popular component by download volume in Central out of 7.1 million total artifacts in November 2021 – and that’s just the vulnerable versions.
Log4j 2.x is in the top 0.003% percentile in popularity by downloads out of a total population of 7.1 million.
In short – it’s as popular as components get.
All versions taken into account in the aggregate, log4j ranks as one of the most popular components across the total population.
Log4j is seen as a dependency in almost 7,000 other open source projects – it’s such a common piece of code that it’s even a building block in the Ingenuity helicopter aboard the Mars rover.
Did you know that Ingenuity, the Mars (Read more...)
*** This is a Security Bloggers Network syndicated blog from Sonatype Blog authored by Ilkka Turunen. Read the original post at: https://blog.sonatype.com/why-did-log4shell-set-the-internet-on-fire





