Qualys Unfurls Ransomware Risk Assessment Service
Qualys today launched a Ransomware Risk Assessment Service through which organizations can proactively identify, prioritize, track and ultimately remediate assets that are vulnerable to ransomware attacks.
Sumedh Thakar, Qualys CEO, said the service leverages the vulnerability discovery capabilities at the core of the Qualys vulnerability management, detection and response (VMDR) platform to specifically pinpoint vulnerabilities that are often targeted by cyberattacks involving malware carrying ransomware payloads.
Qualys researchers have analyzed ransomware attacks over the last five years and identified approximately 100 attack vectors listed as Common Vulnerability and Exposures (CVEs) such as Locky, Ryuk/Conti and WannaCry along with specific misconfigurations that are commonly used by cybercriminals. Sources for that analysis included darknet forums, open source tools, attack playbooks, threat intelligence feeds, MITRE ATT&CK mitigations, tactics recommended by the Cybersecurity and Infrastructure Security Agency (CISA) and best practices published by Fireye Mandiant.
Once identified, vulnerabilities are mapped to available patches that can be directly deployed from the service without requiring additional tools or virtual private network (VPN) connections. The Qualys VMDR platform makes use of agent software developed by Qualys to drive a cloud-based security service.
Alternatively, organizations can take advantage of an appliance to connect to the Ransomware Risk Assessment Service if they are not yet a Qualys customer, said Thakar.
As part of an effort to promote Cybersecurity Awareness Month, Qualys is also making Ransomware Risk Assessment Service available at no cost for 60 days.
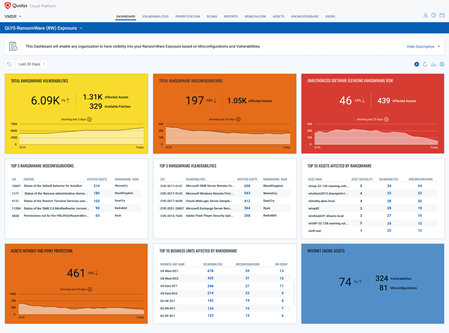
The service specifically identifies via a single dashboard the number of assets affected by each ransomware vulnerability or misconfiguration and the number of open unpatched ransomware vulnerabilities. It also recommends which ransomware vulnerabilities to prioritize based on how lethal they are and provides tools to measure and track remediation effectiveness and provides best practice guidance based on recommendations created by CISA.
Beyond ransomware vulnerabilities, the Qualys Ransomware Risk Assessment Service will also surface internet-facing assets, unauthorized software and flag use of the Remote Desktop Protocol (RDP) that could potentially create blind spots for cybersecurity teams.
Previous Qualys research suggested that, on average, it currently takes organizations 194 days to apply patches for ransomware-related vulnerabilities. The average age of ransomware-related vulnerabilities is five years, with many ransomware-related CVEs left unpatched for more than eight years, according to Qualys research. The automated patching capabilities provided by the Ransomware Risk Assessment Service close that window of opportunity for cybercriminals, said Thakar.
In effect, Qualys is now providing a more prescriptive approach to thwarting ransomware attacks. Most organizations today have no clear, comprehensive means of monitoring risk exposure let alone implementing a remediation plan. There is generally a lack of alignment between the discovery of a vulnerability by security teams and the IT operations team that typically manage patch updates.
In most cases, creating such a plan requires a level of expertise many organizations simply lack. In the absence of an ability to create that plan the next best thing is to rely on an automated service. Clearly, the process today is either not managed at all or is done so slowly that cybercriminals have all the time they need to wreak havoc.