Why Understanding Cyber Criminals Behavior and Tools is Vital
The attack landscape continues to grow rapidly, and with that growth comes the complex challenge of tracking the Tactics, Techniques, and Procedures (TTPs) used by different threat actors. The National Institute of Standards and Technology’s (NIST) Computer Security Resource Center describes TTPs as the behavior of a threat actor; tracking that behavior has become an essential concept for Cyber Threat Intelligence (CTI) Analysts. By profiling and documenting criminal TTPs network defenders can better understand criminal behavior and how specific attacks are orchestrated, allowing them the ability to prepare, respond and mitigate current and future threats.
Defining Tactics, Techniques, and Procedures
To further break down TTP, Tactics refer to the high-level descriptions of the behavior or action the threat actor is trying to accomplish. For example, Initial Access is a tactic a threat actor would leverage to gain a foothold into your network.
Techniques are detailed descriptions of the behavior or actions that are expected from a specific Tactic. For example, a Technique to gain Initial Access to a network could include a phishing attack.
Procedures are technical details or directions about how a threat actor will leverage the Technique to accomplish their objective. For example, the Procedures for a phishing attack would include the order of operation or phases of the campaign. This would include details about the infrastructure leveraged to send the malicious email, whom they plan to target and how they plan on compromising their machine.
Unfortunately, tracking the behaviors of threat actors has been a complex challenge for our industry, mainly because we did not have a single and universally adopted, standardized framework to adhere to. As mentioned in part 1 of our Hackers Almanac series, depending on the security organization who is attributing a digital attack, a threat group known as APT10 by Mandiant also goes by: menuPass by Fireeye, Stone Panda by Crowdstrike, or Red Apollo, Cloud Hopper and POTASSIUM by Microsoft. Making documenting, reporting, and speaking about threat actors extremely difficult.
Fortunately, over the last few years, the industry has begun to widely adopt MITRE’s ATT&CK Enterprise Framework; which aims to provide a community-based standardization and a catalog of TTPs used by threat actors and their known aliases.
What is MITRE ATT&CK?
The MITRE ATT&CK Enterprise framework is an open and available knowledge base that contains adversary tactics and techniques based on actual observations. The MITRE Corporation developed the framework developed the framework, a not-for-profit organization that manages Federally Funded Research and Development Centers (FFRDCs) supporting the US government. Over the years, the MITRE ATT&CK framework has become a valuable resource for enterprises worldwide who wish to better understand specific threats they may face.
The MITRE ATT&CK Enterprise framework tracks adversary threats and profiles them in a simple to view format that details actions adversaries may take to compromise your enterprise network. The MITRE ATT&CK framework provides an exhaustive list of known attack techniques organized into 14 different tactic categories ranging from Reconnaissance to Impact.

This framework is constantly updated to perform up-to-date audits and better structure its defensive policies and detection methods. The MITRE ATT&CK framework also provides a common language across industries. Incorporating the structure and naming conventions used in the MITRE ATT&CK matrix in an organization’s security policy will help enable a common language across the organization and the industry, making it easier to document, report and speak about threat groups.
ATT&CK – Azure Platform Native Security Controls
In June, in collaboration with MITRE’s Center for Threat-Informed Defense (CTID), Microsoft released a matrix mapping the security controls native to the Azure platform to the MITRE ATT&CK framework. The Azure Security Stack framework is the first of its kind, mapping security controls of a product, Azure, back to the ATT&CK Enterprise framework and setting the foundation for others to follow. And, as reports in a recent blog post by MITRE Engenuity, the next platform to release a map in collaboration with MITRE is Amazon Web Services (AWS).
[You may also like: Consistent Security Meets Continuous Deployment on Azure]
The Microsoft Azure Security Stack framework for native security controls maps back to the original TTPs covered in the MITRE ATT&CK Enterprise framework, providing network defenders with resources specific to the Azure platform. This allows network defenders to prepare, respond and mitigate current and future threats to the Azure environment. For instance, in our previous example of Initial Access via phishing, when applied to the Microsoft Security Stack Mapping for Azure, suggests users leverage: Azure DNS Analytics, Azure Defender for App Services and Microsoft Anti-Malware for Azure for a minimal level of protection and detection against this attack vector.
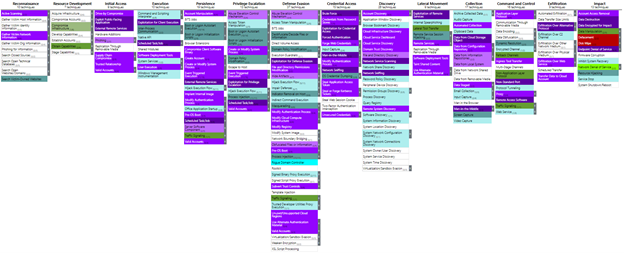
Mapping security controls for products back to the MITRE ATT&CK framework to enable organizations the ability to assess their coverage against real-world threat actor TTPs is precisely what this industry needs at the moment. However, as addressed in the MITRE Engenuity blog, the task of mapping a security stack back to the MITRE Enterprise framework is a labor-intensive and subjective undertaking given the nature of a constantly evolving threat landscape. Regardless of the difficulties producing such maps, I believe the industry is moving quickly to adopt and map their security stacks back to the MITRE ATT&CK Enterprise framework. These kinds of collaborative and public projects enable a common language across the industry and creates a cornerstone for network defenders to document reports and speak about product-specific threats.
Why Understanding The Threat Landscape Is Important
Today’s threats, without a doubt, require full-spectrum solutions, but they also require an in-depth knowledge of the threat landscape. One of the best ways to stay on top of the ever-evolving threat landscape is by studying and contributing to the standardization of threat intelligence. By analyzing and profiling the patterns of threat actors and contributing them to the community, we can better understand criminal behavior and how they orchestrate specific attacks. A deeper understanding of cyber criminals’ TTPs will help the community and organizations understand how to prepare, respond, and mitigate most threats.
Once you begin to understand your enemies’ TTPs you can then start to map them back to your specific security stack. This allows users the ability to harden, detect, isolate, deceive, and evict threat actor TTPs from targeting their particular environment.

Download Series 1 of Radware’s Hacker’s Almanac 2021.
*** This is a Security Bloggers Network syndicated blog from Radware Blog authored by Daniel Smith. Read the original post at: https://blog.radware.com/security/attack-types-and-vectors/2021/07/why-understanding-cyber-criminals-behavior-and-tools-is-vital/




