JumpCloud Adds MFA Capability to Enable Zero-Trust
JumpCloud today announced it is adding a free one-touch multifactor authentication (MFA) capability to its directory to make it simpler to implement a zero-trust IT environment.
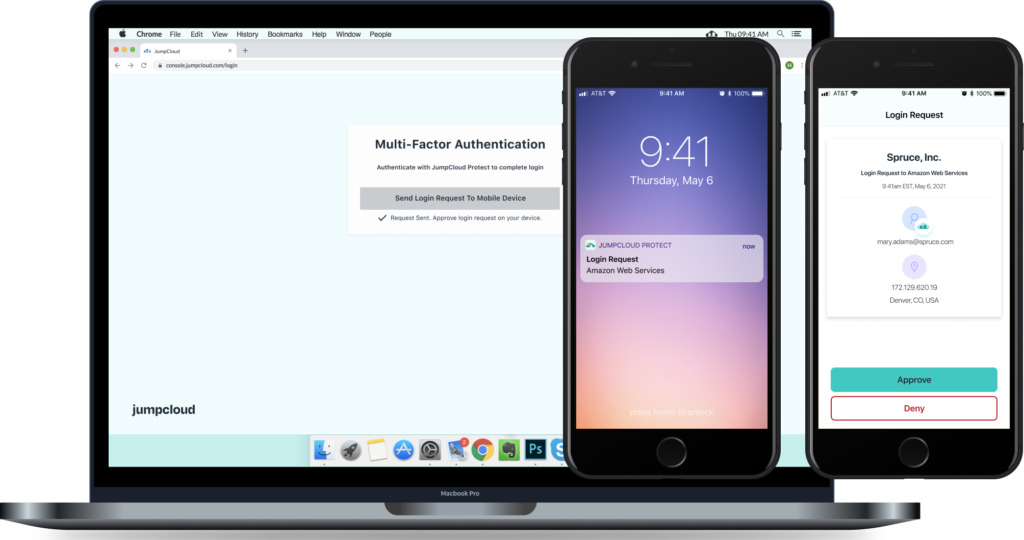
Greg Keller, JumpCloud CTO, says JumpCloud Protect enables IT organizations to enforce MFA policies via iOS and Android devices that only requires the end user to push a button when prompted to authenticate their identity. That simpler approach eliminates the friction and frustration many end users complain about whenever an organization attempts to implement MFA, added Keller.
Designed as an extension of the JumpCloud Directory Platform, this capability provides a time-based one-time password (TOTP) based on a token that is sent to the mobile computing device.
Keller said IT teams will no longer have to implement and manage third-party MFA or authenticator applications; however, JumpCloud will continue to provide integrations with those offerings that organizations may have standardized on.
JumpCloud Protect is also integrated with a Conditional Access authentication policy framework the company previously made available that grants access based on parameters such as device trust, location, network trust and application-specific step-up challenges.
Keller said that while interest in MFA is on the rise, it has not been widely implemented because the processes employed to authenticate end users are viewed as being too cumbersome. JumpCloud Protect is designed to enable MFA to be enabled via a single click across a base of more than 100,000 customers in a way most end users will accept, noted Keller. In the longer term, JumpCloud will extend the core MFA capability it has developed to include support for additional biometric forms of authentication.
Zero-trust as a concept has, of course, been around for years, but it’s only been since the majority of employees began working from home (WFH) that organizations have begun to try to actually implement it. The assumption used to be that any device behind a firewall could be trusted. Now that many more employees will be working from anywhere (WFA), more organizations are looking to implement zero-trust policies mainly because they don’t know when employees might be working from home and generally lack visibility into how those devices might have been employed when not connected to a corporate network.
The challenge cybersecurity teams face, of course, is getting the funding required to implement a zero-trust IT architecture, an issue JumpCloud is trying to help address by making JumpCloud Protect available for free.
It’s not quite clear how aggressively organizations are moving down the path toward zero-trust IT environments. Most are, at the very least, investigating what’s required to achieve that goal. However, as it becomes apparent that employees will be coming to the office less frequently than they did prior to the pandemic, most organizations will need to revisit their entire cybersecurity strategy to accommodate that level of flexibility. Regardless of how that’s achieved, some form of MFA will be required. The primary issue is finding a way to implement MFA in a way that end users won’t reject or, more troubling still, try to work around.