Home » Cybersecurity » Threats & Breaches » Vulnerabilities » Deep Diving into CVE-2021-22114 Spring-integration-zip Path Traversal
Deep Diving into CVE-2021-22114 Spring-integration-zip Path Traversal
Guess who’s back? Earlier this month, CVE-2021-22114 in spring-integration-zip, returned for the second time to cause havoc.
The vulnerability originates due to failure to sufficiently sanitize user supplied input, which is perhaps one of the biggest problems in secure development. In this case, failure to sanitize archive entry names prior to extraction allows an attacker to traverse beyond the intended root directory and extract files to an arbitrary location, possibly overwriting existing ones.
To help everyone understand what this all actually means, we’re taking a deep dive into this returning vulnerability.
Name/Vulnerability Identifier: CVE-2021-22114
Type of Vulnerability: Path Traversal
Severity:
CVSS 3.1 Score: 5.3 / Medium
CVSS 3.1 Metrics: CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:U/C:N/I:H/A:N
Components Affected:
Mave:
Org.springframework.integration:spring-integration-zip
[1.0.2.RELEASE, 1.0.4.RELEASE)However, this is not the first time we see this issue. This is the second attempt at fixing a Path Traversal vulnerability which was originally reported as CVE-2018-1261. In the fix released for this CVE, the project developers made an initial effort to identify traversal characters and throw an exception if malicious behavior was detected.
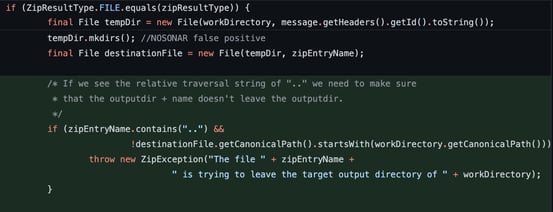
Image: Fix implemented for CVE-2018-1261. Path check on FILE type only.
This was done only for the file type and did not cover the case of Byte Arrays. An attacker could use Byte Arrays to bypass the initial check and the framework would return the errant path to the user application to further process. This insufficient fix resulted in CVE-2018-1263.
This time around, the path checks were implemented in their own function, ‘checkPath’, and respectively called where needed.
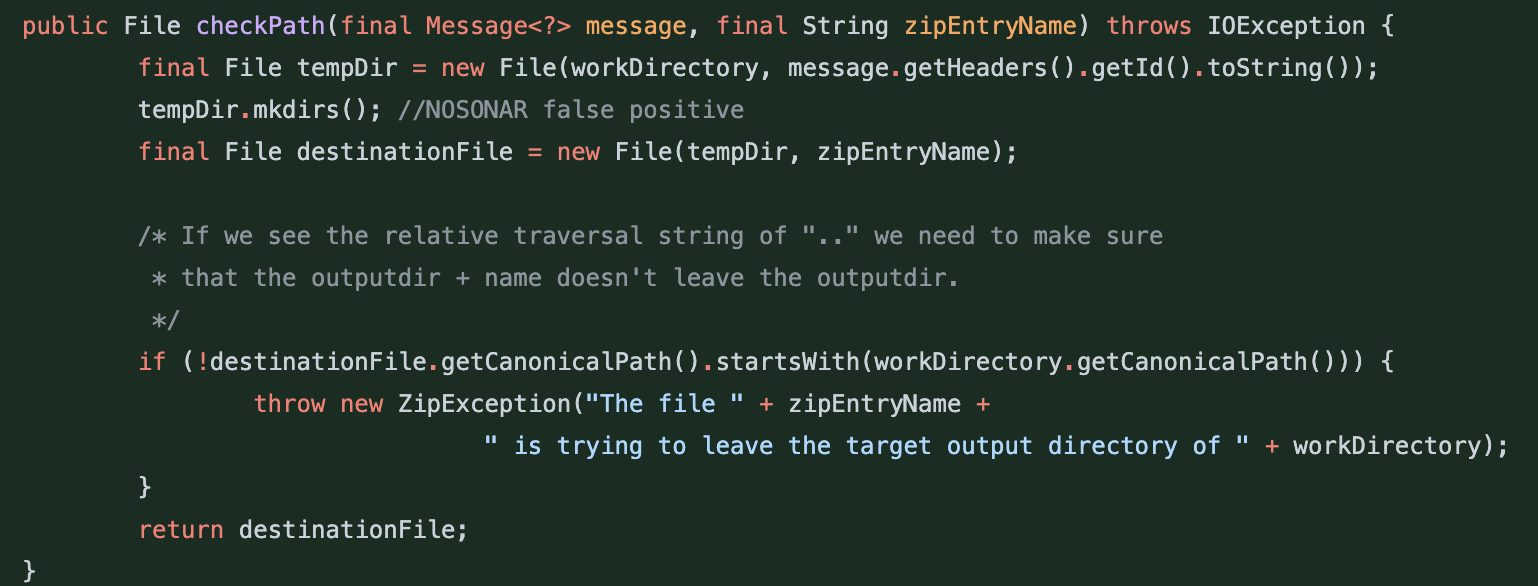
Image: Fix implemented for CVE-2018-1263. Path check moved to a helper function.
Now, 2 vulnerabilities and 1 insufficient fix into our journey, 3 years later researchers were able to bypass previous restrictions and a third vulnerability arose, (Read more...)
*** This is a Security Bloggers Network syndicated blog from Sonatype Blog authored by Juan Aguirre. Read the original post at: https://blog.sonatype.com/deep-diving-into-cve-2021-22114-spring-integration-zip-path-traversal





