Top 5 Cybersecurity Frameworks to Secure Your Organization
Cybersecurity Frameworks 101
Before we get into what the top cybersecurity frameworks are, let’s go through what exactly a cybersecurity framework is. All of these different cybersecurity frameworks provide standards and guidelines to secure your organization against cyber adversaries. Many industries have different cybersecurity requirements and standards. For example, the energy sector has the NERC CIP standards and the medical industry has HIPAA. Organizations often use cybersecurity platforms or frameworks to secure their organization and ensure compliance with these mandates. To select the best security framework for your organization you’ll need to make a few considerations:
- The maturity of your current cyber risk security program
- Your company policies and goals
- Any regulation requirements you have to comply with
Overall, your team should take some time to understand the different cybersecurity frameworks so that you can select one that best suits your business needs.
Cybersecurity Frameworks, a Guiding Light
Cybersecurity frameworks provide guidance for improving and building your cyber risk program. Having a security framework can allow for consistency across different functions and show a uniform set of goals. Many frameworks provide guidance on where to begin when securing your organization from common cybersecurity threats. Most begin with basic practices and processes that are essential to the foundation of your cyber risk reduction management. With the help of the best cybersecurity frameworks, you can move past compliance requirements and obtain a secure cyber state. These top cybersecurity frameworks will allow your organization to achieve a more cyber resilient program.
NIST CSF
The NIST Cybersecurity Framework is highly 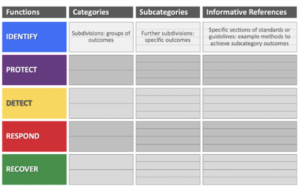

CIS 20
The Center for Internet Security has a set of 20 critical security controls that outline best practices for internet security and cyber threats. These 20 critical security controls are broken down into three buckets – basic, foundational and organizational. The CIS 20 is acclaimed by many to be one of the best cybersecurity frameworks. According to a TripWire article “A study of the previous release found that by adopting just the first five controls, 85 percent of attacks can be prevented”. These best practices empower organizations to push past compliance and holistically secure their organization. One of the biggest benefits of CIS20 is that it helps users easily prioritize. The controls in the basic bucket are the most critical and have high payoff. These controls are your starting point to enabling risk reduction.
ISO/IEC 27001
The International Organization for Standardization and International Electrotechnical Commission developed the ISO/IEC 27001 and it’s one of the most vastly used security controls frameworks. More than a third of organizations use the ISO/IEC 27001 as their primary regulatory framework. Organizations of all sizes and industries can become certified in ISO/IEC 27001 by an external auditor. This framework consists of 11 clauses and an Annex that provides guidelines to controls that can be implemented. Like some of the other frameworks on this list, it can be integrated with other frameworks. And due to its widespread use, there’s a variety of resources that can inform and guide users.
C2M2
The Cybersecurity Capability Maturity Model has 10 domains, and within each domain are approach and management objectives. The approach objectives outline what needs to be implemented and the management objectives outline how well these cybersecurity activities are implemented. Each activity within the objectives are broken down into 3 maturity levels. In order to get to the next maturity level, they must complete all activities in the previous level. The C2M2 framework is a thorough and comprehensive framework that gives a holistic view of an organization’s cyber risk management. Authors created the C2M2 for those in the electricity and oil/natural gas sector, but it can be used by any company. It’s a robust cyber risk assessment that helps you improve your organization’s cyber resilience.
CMMC
Structured into 17 domains with 5 levels of certification within each domain and 171 technical practices, CMMC empowers a “collaborative risk management approach” to secure your organization. Moreover, CMMC not only prepares organizations for cyber events but also helps develop a route to recovery for when a cyber-attack unfolds. Similar to C2M2, to get to the next maturity level/certification, all the practices within the previous maturity level must be implemented. Government defense contractors use CMMC to not only protect their organizations, but also national security.
Preparing for Cyber Recovery
The use of cybersecurity frameworks can allow organizations to go beyond compliance and secure your infrastructure and confidential information. When it comes to cybersecurity it’s not a matter of “if” a cyber event occurs, it’s about “when”. With more cyber threats than ever, these best practices can decrease organizations’ susceptibility and help you develop a path to recovery when a cyber-attack is successful. The increase in cyber risks has led to discussion of more government regulations and security requirements. For example, due to the rise in cyber-attacks from China, U.S. Cybersecurity and Infrastructure Security Agency (CISA) encouraged organizations to implement a number of mitigation strategies. The current cyber best practices may become security requirements in the future. By utilizing these frameworks, you can get ahead of the game.
Making These Top Cybersecurity Assessments Work for You
Our platform, Axio360 supports a number of the frameworks mentioned above including CMMC, C2M2, CIS20 and NIST CSF. Our NIST CSF assessment includes mappings to ISO 27001 and a number of other standards such as the NIST 800-53, COBIT, NERC CIP and more. Using Axio360 to assess your organization will allow you to identify weak points. With that knowledge, your team will be able to address vulnerabilities by implementing controls or buying insurance. Axio360 makes it easy to pinpoint your cyber risk management gaps and roadmap towards your target. Having a roadmap and understanding your current cyber risk vulnerabilities will decrease susceptibility and build up capability to recover. Our Kanban road-mapping tool makes planning easy, adjustable and collaborative. Moreover, our milestone feature tracks progress and improvement, while our target profile feature allows for goal setting across the organization. Bring these top cybersecurity assessments to life with Axio360.

To learn more about cybersecurity assessments, read our recent blog.
*** This is a Security Bloggers Network syndicated blog from Axio authored by Axio. Read the original post at: https://axio.com/insights/top-5-cybersecurity-frameworks-to-secure-your-organization/





