UPDATE Aug. 3, 2020: Cybersecurity experts discovered a new (new window)v(new window)ulnerability(new window) that allows access to the private encryption keys stored in old versions of Apple’s Secure Enclave chips. The Secure Enclave chip is a security feature that protects the private encryption keys your iOS device uses to encrypt all the sensitive data on your device. Proton Mail’s AppKey is stored alongside this data if you enabled Touch ID or Face ID protection in the app.
This vulnerability is a hardware issue with Apple’s Secure Enclave chip, which means it cannot be patched or fixed with an update. It only affects older versions of the Secure Enclave chip, so only devices that use processors version A7 through A11 (iPhones between version 5S and X) are impacted. It also requires the attacker to have physical access to your device, so it is only an issue if your device is stolen or confiscated.
If you have an older iOS device and want to maintain the security of Proton Mail’s AppKey Protection System, you should only enable PIN protection in the Proton Mail iOS app. The PIN protection system is unaffected by this vulnerability.
One of the unique innovations of the Proton Mail iOS app is the AppKey Protection System. This is an extra layer of encryption on top of Apple’s built-in local encryption that protects sensitive Proton data stored on your device.
When you have AppKey Protection System enabled, your Proton Mail data is more secure against malware from hackers and governments, stalkerware, and phone extraction tools used by authoritarian regimes and border agents without a warrant.
It’s easy to turn on AppKey. Simply enable Face ID, Touch ID, or PIN code lock in your Proton Mail iOS app settings, and turn on the AppKey protection switch.
Why you should enable AppKey
Our end-to-end encryption(new window) secures your email contents as they travel over the Internet, blocking anyone who might try to intercept them: hackers, Internet service providers, governments, and even Proton Mail itself. Zero-access encryption(new window) locks up your data at rest on our servers so that we can’t access it, even for emails that came from a non-Proton Mail account.
But what about the “ends”? How is your data secured on your device?
As a general rule, mobile apps do not protect your data if your device is compromised. Instead, apps rely on the built-in security of the device. For iPhones and iPads, the Apple Keychain is responsible for securing the access tokens, passwords, and certificates that keep the data on your mobile apps safe. Usually that built-in security is enough — but sometimes it’s not.
There are many instances where Apple Keychain is insufficient to protect your data. Here are just a few real-world examples:
- Poison Carp — In September, security researchers at The Citizen Lab discovered an apparent state-sponsored attack(new window) on prominent Tibetans and connected them to other spyware attacks on thousands of Uyghurs. They nicknamed the attacker “Poison Carp,” but it seems highly likely that the Chinese government is behind it because of the sophistication of the attacks and the fact that the victims belong to ethnic groups near the top of Beijing’s enemies list. Victims only needed to click on a phishing(new window) link sent via WhatsApp to trigger the exploit, which installs spyware on the device.
- Mobile forensics — When police want to crack open an iPhone, it’s not easy, especially on newer models. The iPhone is famously secure, as the FBI learned(new window) when it sought a backdoor to a terrorist’s device. But it’s not impossible, and there are companies that claim to have exploits, such as Cellebrite’s “Advanced Services(new window).” Cellebrite markets its spyware products for everything from warrantless border inspections(new window) to spying on refugees(new window), and it is thought to sell its spyware products(new window) to authoritarian regimes.
- Stalkerware — Also called “spouseware,” stalkerware is commercially available spyware that enables people to spy on their partners. Usually this requires the attacker to have physical access to the device to install the malware, but in a domestic situation that may not be difficult. As noted in this analysis of stalkerware applications(new window), it can be very difficult to know whether there is stalkerware installed on your device. (If you’re unsure, you should reboot your device and change your iCloud password.)
Recognizing these security challenges, we decided to go above and beyond the standard threat model of most apps. We now provide Proton Mail iOS users with even more security, even if their device is compromised.
How the AppKey Protection System works
If an attacker can penetrate your iOS device’s security system, they might be able to steal the key that unlocks your Proton Mail data. Our solution is an extra lock whose key is much more difficult to steal because it is not present on your device: your face, your fingerprint, or your secret PIN.
When you enable Face ID, Touch ID, or PIN code lock and AppKey protection in your Proton Mail iOS app settings, the Proton Mail app won’t be able to decrypt data or pull data from our servers unless the AppKey is present in the device’s memory.
Learn more: Read our iOS client security model for more technical details.
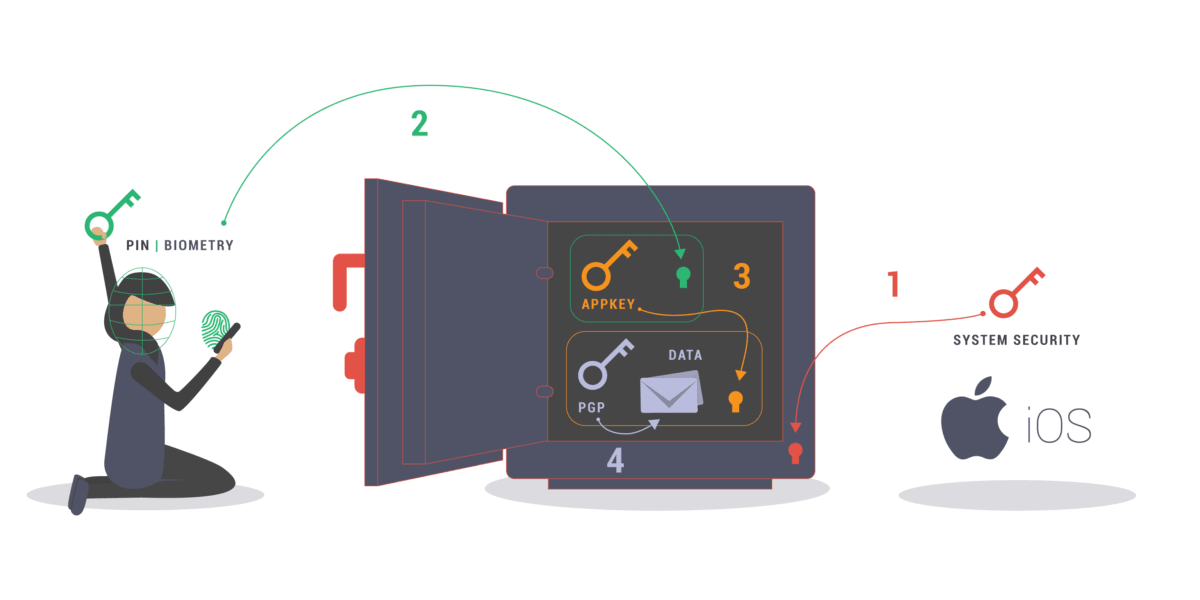
The AppKey protects the following information with an extra layer of encryption:
- Authentication tokens (which allow you to stay logged in to your Proton Mail account in the app rather than having to enter your password each time)
- Your Proton Mail username
- Encryption keys
- Attachments
- Message metadata (such as subject lines and email recipients)
- Contacts
- Account settings
If you don’t have Face ID, Touch ID, or PIN protection enabled, the AppKey is stored in cleartext (but still protected by iOS Keychain) and your data is vulnerable if your device is compromised. (However, you might still be safe from attacks that exploit iTunes or cloud backup through device pairing.)
AppKey also enables some interesting features, such as the Wipe Local Data shortcut described in the tweet below. This works by simply destroying the AppKey, rendering local data impossible to decrypt and causing the account to log out.
Here's a privacy feature you can set up with Proton Mail and iOS 13. 👍
— Proton Mail (@ProtonMail) October 28, 2019(new window)
1. Tap Shortcuts > Automation > Create Personal Automation
2. Select Arrive > Choose "USA" for Location
3. Tap Add Action > Select the Proton Mail app > Tap Wipe Local Data pic.twitter.com/62spB3zgX7(new window)
Final thoughts
We’ve gone to great lengths to protect our users — from developing AppKey to releasing our iOS app open source(new window), allowing other security researchers to test for vulnerabilities. But no system is 100% secure. There are always weaknesses that hackers will try to exploit. You can help improve the security of your iOS device by following these security tips:
- Install all the latest software updates.
- Set long, alphanumeric passcodes in your device settings.
- Never click on links(new window) or download attachments in any app if you don’t know the sender.
- Do not install untrusted configuration profiles or root certificates in your device settings.
- Enable Touch ID, Face ID, or PIN protection in your Proton Mail app settings, which is the only way to take advantage of the AppKey Protection System.
- Use strong, unique passwords(new window) and two-factor authentication(new window) for your accounts.
Thank you for supporting Proton Mail and our mission to make secure Internet a reality for all.
Best Regards,
The Proton Mail Team
You can get a free secure email account from Proton Mail here.
We also provide a free VPN service(new window) to protect your privacy.
Proton Mail and Proton VPN are funded by community contributions. If you would like to support our development efforts, you can upgrade to a paid plan(new window) or donate(new window). Thank you for your support.