What Is Two-Factor or Multi-Factor Authentication?
Traditional password-and-username authentication can leave users vulnerable. In 2010 Christopher Chaney, a celebrity obsessed cyber-stalker, got hold of a number of celebrity emails. Using data gleaned from social media and Wikipedia, he successfully guessed the passwords to over 50 personal email accounts belonging to famous women, including Scarlett Johansson, Mila Kunis, and Christina Aguilera. He had access to these accounts for almost a year, and he was responsible for posting nude photos of Scarlett Johanssen and several non-celebrity women. He has since been sentenced to 10 years in jail.
Almost everyone’s email address has been exposed online somewhere (luckily there are ways to find out if this has happened). And traditional password-based authentication is inherently insecure. Given these two facts, it’s essential to offer customers additional ways to protect their accounts.
Two-factor or multi-factor authentication (2FA or MFA) is an extra authentication method that’s becoming increasingly common. But just what are 2FA and MFA, and how can they help protect your customers?
What Is Multi-Factor Authentication?
The only difference between multi-factor authentication and two-factor authentication is that 2FA only uses two of the available additional checks to verify customer identity, whereas MFA may use three or more checks.
More checks mean more security, but customers can find them onerous, so it’s wise to choose the number of extra checks based on both the minimum security level suitable for that service or account, and the frequency and proximity to other verification checks.
If customers repeatedly have to go through multiple checks on their customer journey, they will soon become frustrated and drift away to your competitors. Of course, if you lose their data, they will also be someone else’s customer soon enough.
Using multi-factor authentication as part of your customer identity and access management (CIAM) platform helps you build and maintain a solid customer opinion as the world evolves towards industry 4.0.
What Types of Multi-Factor Authentication Are There?
There are a number of different checks you can use to implement MFA, and this list is always growing. When choosing which checks to use, take into account things like the level of security needed, the types of technology most often used by your customers to access your assets, and, to some extent, cost.
SMS token
A relatively straightforward measure to implement, especially for consumers and the general public, this check most often consists of a text message containing a PIN number. This PIN is then used as a one-time password (OTP), usually in addition to traditional username-and-password verification.
If your customers frequently access your services from mobile devices, it’s wise to offer them this or another mobile-device-based authentication method to help smooth the customer journey.
Email token
This method is Identical to SMS tokens, but the code is sent via email. Since not everyone has their phone with them all the time, it’s a good idea to offer this option. It can act as a backup method if your customer has had their mobile device lost or stolen. It’s also a convenient way to access an OTP from any platform that can receive email.
Hardware token
Using a separate hardware token is considered one of the most secure authentication methods available, as long as the key remains in the customer’s possession. This method is more expensive, although it can be cost-effective to provide your high-value customers with dongles for free. Business customers tend to be more willing to go the extra mile to use a hardware token, and adoption of hardware tokens is increasing. But it’s still not a good idea to make them compulsory for anyone but the most high-value, at-risk customers such as banking, insurance, and investment clients.
Users just need to insert the hardware token into their device to use it. If they use a mobile device for access, they may need another dongle to add a USB or USB-C port to their smart device.
Software token
By using an authentication application on a mobile device, you can get almost the same level of security as with a hardware token. Essentially, the smart device becomes the token. This can be tied in with services like Google Authenticator.
Getting customers to use a third-party solution can help encourage them to use MFA for more of their services outside of your business, thus increasing their overall security. It also makes a great alternative to carrying an additional dongle to attach a hardware token to a smart device.
Phone call
Another way to get a one-time password is via automated phone call.
Biometric verification
People with a smart device or computer with biometric authentication (such as fingerprint ID or facial recognition) can use this check to confirm their identity as part of MFA. Biometric ID verification tends to be less hassle than typing in an OTP, so customers find it less aggravating to use it frequently. The lower friction makes it an ideal option when extra checks are unavoidable.
Other forms of multi-factor authentication
There are a few other digital verification methods available to your customers.
Social login, also called social identity verification, is something many users find convenient, since they’re usually already logged in to the relevant accounts. Bear in mind though that social media platforms are high-value targets for hackers, so social ID verification shouldn’t be the only method used on top of username/password in most cases.
Security questions are a type of knowledge-based authentication (KBA) where the questions and answers are static. The questions could be defined by the business or the customer, and the customer provides the answers that are later verified. Dynamic KBA, which is more secure than static KBA, uses questions that are generated in real-time based on data records such as credit history or transactions.
Risk-based authentication (RBA) can also be used in conjunction with MFA. By monitoring things like location, device, and even user keystrokes, you can tailor the frequency of MFA checks to the security situation. RBA helps avoid asking customers for extra verification repeatedly when they’re signing in from their “home” machine and location.
How Secure Is MFA?
The security of your MFA solution depends on a few different things. First of all, you need engaged, willing customers to apply the above solutions. As mentioned earlier, hardware keys offer greater security than social verification, but they cost money and effort to use.
It’s also important to make sure your MFA set up follows a few basic security steps:
- Make sure that new users can’t set up MFA the first time they log in. An attacker with a valid password could steal the account and set up MFA with their choice of phone number.
- Make sure automated phone calls use clear messages that let the user know someone is trying to log in.
- Educate customers about their chosen MFA methods; make sure they know what to do and who to contact if there is an issue.
- Don’t allow high-value, high-risk clients to authenticate with less secure MFA methods like social verification.
- Make sure you use multi-factor authentication rather than two-factor authentication. 2FA with SMS and username/password for the two factors is increasingly vulnerable to SIM swapping.
At the end of the day, no system is ever 100% secure. What MFA does is protect your customers from all but the most determined hackers, and it protects them many thousands of times better than username/password alone.
What Is Adaptive Multi-Factor Authentication?
Adaptive MFA is a method that your CIAM provider uses to apply the right level of authentication security depending on the risk profile of the actions currently being attempted by the customer. Adaptive MFA goes beyond a static list of rules and adapts to ask customers for the types of verification that best suit a user session.
By adding risk-based authentication as a final security layer on top of your other MFA layers, adaptive MFA avoids annoying your customers, while keeping their data safe from attacks. By using adaptive multi-factor authentication, you can relax with the assurance that your customers are happy and safe when they’re using your online services and products.
The Benefits of Multi-Factor Authentication
The benefits of multi-factor authentication form part of a customer experience that modern customers have come to expect from any well-managed organization in the 21st century. You can see that MFA is rapidly becoming a standard offering from the biggest tech companies that we deal with day to day. Failing to meet these customer expectations leaves you at risk of losing clientele to companies that are using CIAM and MFA to keep their data from harm.
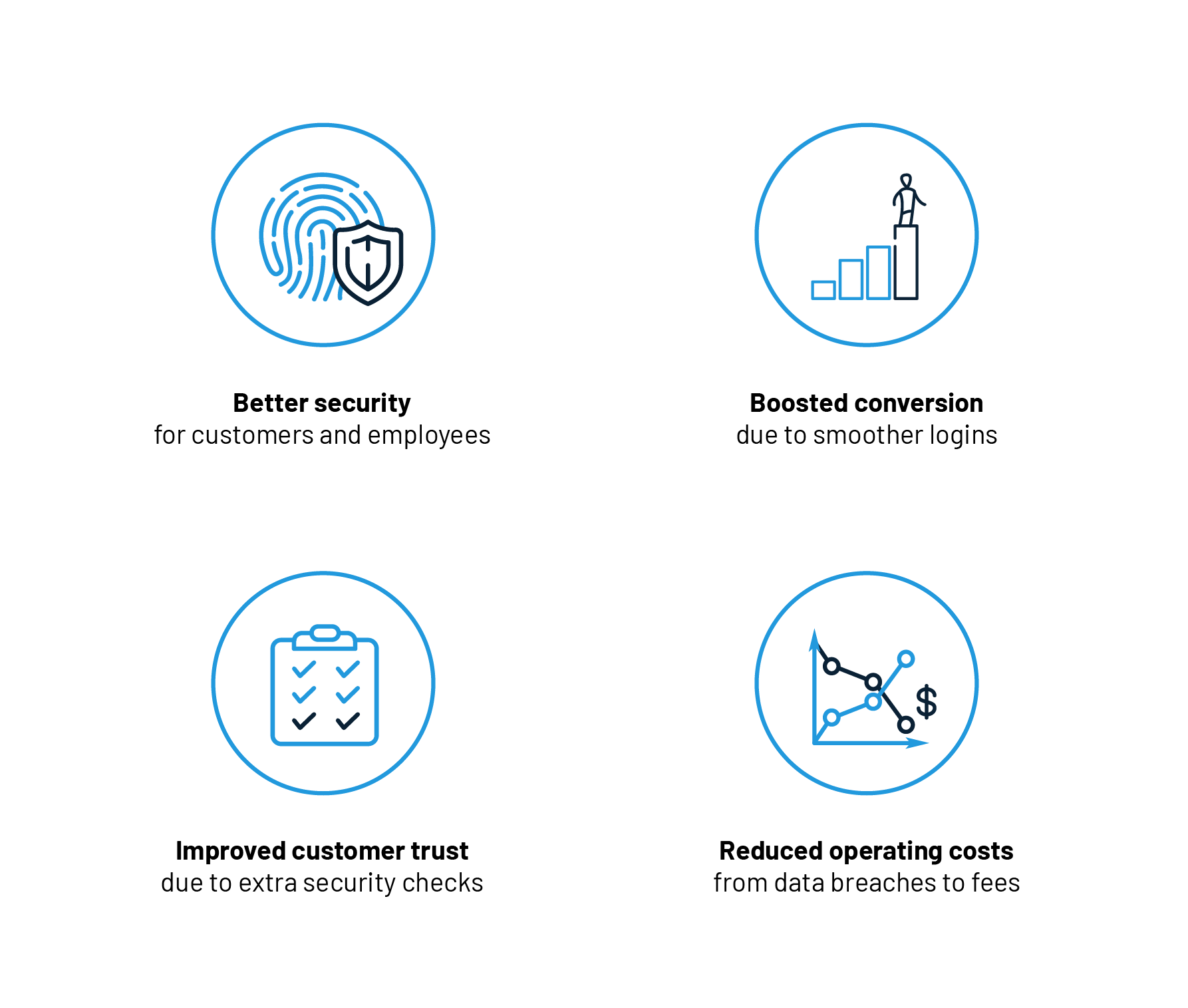
Here’s what MFA gives you and your customers:
- Better security for customers and employees
- Boosted conversion due to smoother logins
- Improved customer trust due to extra security checks
- Reduced operating costs from data breaches to service fees
This list is, of course, not exhaustive. There are also plenty of secondary benefits which may vary from industry to industry.
Implementing MFA with LoginRadius
If you want to get the most out of the LoginRadius Identity platform, you need to enable MFA. This process is relatively easy, with options for your customers to use SMS or Google Authenticator.
First of all, decide whether SMS verification is secure enough for your customers’ purposes. For most use cases, SMS verification is fine, but there have been cases where a hacker has poached an email account and mobile number. So if your customers are dealing with high-value, high-risk tasks such as financial transactions or gambling, you may want to stick with Google Authenticator, which allows the use of hardware keys or a software key attached to a mobile device.
There are just a few steps in the LoginRadius Admin Console to enable SMS verification, with options to choose your own SMS template and SMS provider. You then have a choice of options to use as the first verification factor: standard email and password login, username and password, access token, or automated phone call. The second factor is, of course, a one-time password/code sent by SMS.
To enable Google Authenticator, you’ll need to set up your ID in the Admin Console for Google to identify your website or app on Authenticator. You can then set up your QR code specifications and whether MFA is mandatory. Again, you can choose from standard email and password login, username and password, access token, or automated phone call for the first verification factor. Google Authenticator supports FIDO 2UF hardware tokens and app-based software tokens on smart devices, so if you want to enable these methods you need to use Authenticator.
Whichever option you choose, LoginRadius is always on hand to help you if you have any questions or issues.
Conclusion
Multi-factor authentication gives you a flexible way to balance customer experience with today’s security requirements. Not only is it one of the best ways to secure your login process, it also shows your customers that you care about their security and take it seriously.
Download the Buyer’s Guide to Multi-Factor Authentication to find out more, or get in touch with the LoginRadius team if you have any questions.
The post What Is Two-Factor or Multi-Factor Authentication? appeared first on Identity Blog.
*** This is a Security Bloggers Network syndicated blog from Identity Blog authored by Kundan Singh. Read the original post at: https://www.loginradius.com/blog/2019/06/two-factor-authentication-mfa/






