Weekly Cyber Risk Roundup: Record-Setting DDoS Attacks, Data Breach Costs
Last week, researchers observed a 1.35 Tbps distributed denial-of-service attack (DDOS) attack targeting GitHub. It was the largest DDoS attack ever recorded, surpassing the 1.2 Tbps attack against DNS provider Dyn in October 2016.
The attack leveraged a newly observed reflection and amplification vector known as memcached. Akamai researchers warned that other organizations experienced similar DDoS attacks using the new method following the GitHub attack and that even larger attacks may be possible in the future.
“Memcached can have both UDP and TCP listeners and requires no authentication,” the researchers wrote. “Since UDP is easily spoofable, it makes this service vulnerable to use as a reflector. Worse, memcached can have an amplification factor of over 50,000, meaning a 203 byte request results in a 100 megabyte response.”
The attack was mitigated within 10 minutes, GitHub said. The following day GitHub was the target of a second DDoS attack that disrupted availability for a 15-minute period, ThousandEyes reported.
“Because of its ability to create such massive attacks, it is likely that attackers will adopt memcached reflection as a favorite tool rapidly,” Akamai researchers wrote. “The good news is that providers can rate limit traffic from source port 11211 and prevent traffic from entering and exiting their networks, but this will take time.”
Wired reported there are approximately 100,000 memcached servers that currently have no authentication protection and can be abused by malicious attackers to carry out similar potentially massive, botnet-free DDoS attacks.
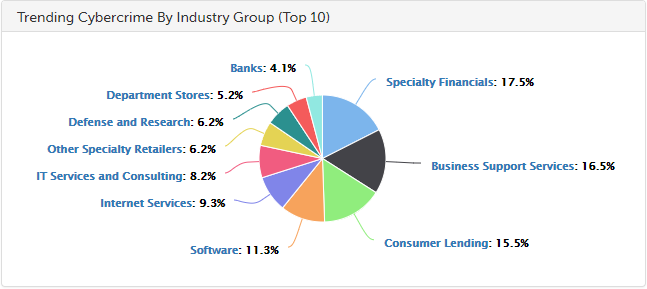
Other trending cybercrime events from the week include:
- W-2 information breached: The University of Alaska said that 50 current and former employees and students had their personal information compromised when hackers gained access to their university accounts by answering security questions and resetting their passwords. The Association for Supervision and Curriculum Development is notifying employees that their W-2 information was compromised due to a spear phishing attack. Wallace Community College Selma said that current and former employees had their W-2 information compromised when an employee fell for a phishing scam. Curtis Lumber is notifying employees that their personal information was stolen in a spear phishing attack, and some of those employees have reported issues related to filing their federal taxes following the incident.
- Ransomware infections continue: The Colorado Department of Transportation said that computers had been reinfected with ransomware eight days after an initial attack. Both the Children’s Aid Society of Oxford County and the Family and Children’s Services of Lanark, Leeds and Grenville in Canada were the victims of a ransomware infection. Jemison Internal Medicine is notifying 6,550 patients of a ransomware infection that may have compromised their personal information.
- Payment card breaches and service disruptions: A number of Tim Hortons locations in Canada were temporarily shut down or were forced to close their drive-throughs after malware was discovered targeting Panasonic cash registers. NIS America said that customers of its online stores had their information compromised due to being redirected to a malicious site that would harvest their information during the checkout process. North 40 is notifying customers that their payment card information may have been compromised due to unauthorized access to its e-commerce website.
- Notable data breaches: A hacker gained access to the intranet of Germany’s government and accessed confidential information. St. Peter’s Surgery and Endoscopy Center is notifying patients that their personal and medical information may have been compromised due to unauthorized access to its servers. Healthcare vendor FastHealth submitted a data breach notification regarding unauthorized access to its web server. Porsche Japan said that the information of customers was exposed due to a hack. Metro Wire Rope Corporation said that an employee email account was compromised after the employee opened a malicious attachment with credential-stealing capabilities. The French news magazine L’Express exposed a database containing the personal information of readers and after being notified of the exposure took a month to secure the data. U.S. Marine Corps Forces Reserve may have compromised the personal information of 21,426 individuals due to sending an unencrypted email with an attachment to the wrong email distribution list.
- Other notable events: The Financial Services Information Sharing and Analysis Center said that one of its employees was successfully phished, and the compromised email account was used to send further phishing messages to other members, affiliates, and employees. The recent hack of the PyeongChang Winter Olympics that led to Internet disruptions and website downtime was a false-flag operation carried out by Russian military spies to make it appear as if the attack was carried out by North Korea, U.S. intelligence officials said. An Arkansas man who developed the remote-access Trojan NanoCore and marketed it on Hack Forums has been sentenced to 33 months in prison.
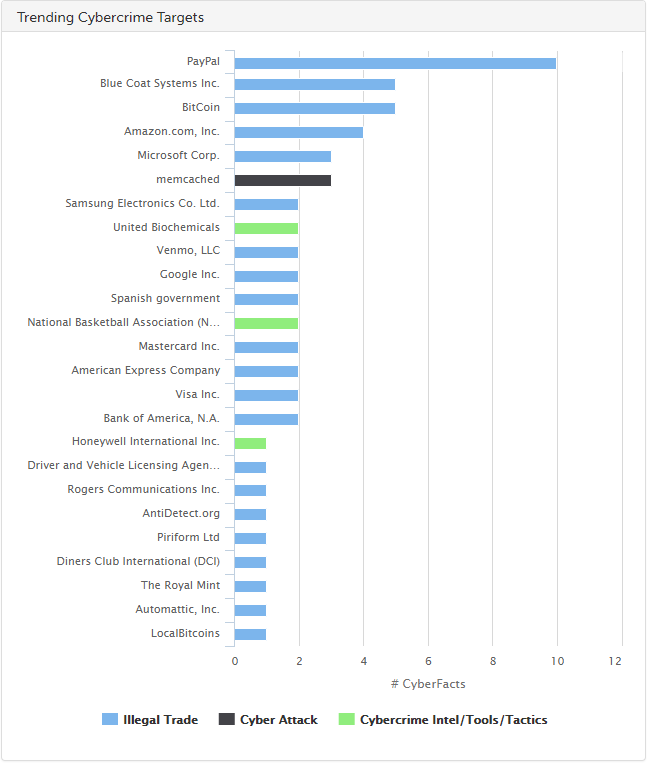
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of the top trending targets are shown in the chart below.
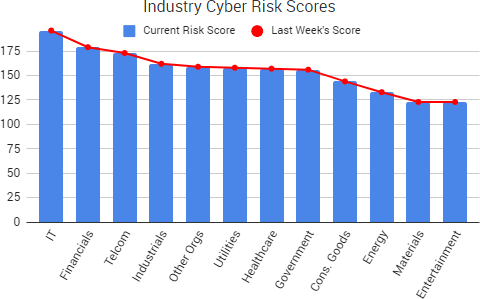
Cyber Risk Trends From the Past Week
Equifax was back in the news this week after announcing it had discovered an additional 2.4 million U.S. consumers who were affected by its massive 2017 data breach, bringing the total number of people impacted to 147.9 million.
“This is not about newly discovered stolen data,” said Paulino do Rego Barros, Jr., Interim chief executive officer in a press release. “It’s about sifting through the previously identified stolen data, analyzing other information in our databases that was not taken by the attackers, and making connections that enabled us to identify additional individuals.”
The company also said that it expects breach-related costs to hit $275 million in 2018, which Reuters noted could make the Equifax breach the most costly hack in corporate history:
The projection, which was disclosed on a Friday morning earnings conference call, is on top of $164 million in pretax costs posted in the second half of 2017. That brings expected breach-related costs through the end of this year to $439 million, some $125 million of which Equifax said will be covered by insurance.
Those breach-related costs could rise further once legal actions from consumers and regulators are finally resolved. However, Sen. Elizabeth Warren recently stated that “Equifax is still making money off their own breach” and that even consumers who do not want to do business with them may end up buying credit protection services from another company who “very well may be using Equifax to do the back office part.”
It’s the same criticism she waged in January when introducing a bill with Sen. Mark Warner to address problems related to credit agencies collecting data without strict protections in place to secure that information. As CNET noted, if such a bill was in place at the time of the Equifax breach, the company likely would have faced a fine of at least $14.3 billion.
*** This is a Security Bloggers Network syndicated blog from SurfWatch Labs, Inc. authored by Jeff Peters. Read the original post at: https://blog.surfwatchlabs.com/2018/03/05/weekly-cyber-risk-roundup-record-setting-ddos-attacks-data-breach-costs/




