Weekly Cyber Risk Roundup: Olympic Malware and Russian Cybercrime
More information was revealed this week about the Olympic Destroyer malware and how it was used to disrupt the availability of the Pyeonchang Olympic’s official website for a 12-hour period earlier this month.
It appears that back in December, a threat actor may have compromised the computer system’s of Atos, an IT service provider for the Olympics, and then used that access to perform reconnaissance and eventually spread the destructive wiper malware known as “Olympic Destroyer.”
The malware was designed to delete files and event logs by using legitimate Windows features such as PsExec and Windows Management Instrumentation, Cisco researchers said.
Cyberscoop reported that Atos, which is hosting the cloud infrastructure for the Pyeongchang games, was compromised since at least December 2017, according to VirusTotal samples. The threat actor then used stolen login credentials of Olympics staff in order to quickly propagate the malware.
An Atos spokesperson confirmed the breach and said that investigations into the incident are continuing.
“[The attack] used hardcoded credentials embedded in a malware,” the spokesperson said. “The credentials embedded in the malware do not indicate the origin of the attack. No competitions were ever affected and the team is continuing to work to ensure that the Olympic Games are running smoothly.”
The Olympic Destroyer malware samples on VirusTotal contained various stolen employee data such as usernames and passwords; however, it is unclear if that information was stolen via a supply-chain attack or some other means, Cyberscoop reported.

Other trending cybercrime events from the week include:
- Organizations expose data: Researchers discovered a publicly exposed Amazon S3 bucket belonging to Bongo International LLC, which was bought by FedEx in 2014, that contained more than 119 thousand scanned documents of U.S. and international citizens. Researchers found a publicly exposed database belonging to The Sacramento Bee that contained information on all 19 million registered voters in California, as well as internal data such as the paper’s internal system information, API information, and other content. Researchers discovered a publicly exposed network-attached storage device belonging to the Maryland Joint Insurance Association that contained a variety of sensitive customer information and other credentials. The City of Thomasville said that it accidentally released the Social Security numbers of 269 employees to someone who put in a public record request for employee salaries, and those documents were then posted on a Facebook page.
- Notable phishing attacks: The Holyoke Treasurer’s Office in Massachusetts said that it lost $10,000 due to a phishing attack that requested an urgent wire payment be processed. Sutter Health said that a phishing attack at legal services vendor Salem and Green led to unauthorized access to an employee email account that contained personal information for individuals related to mergers and acquisitions activity. The Connecticut Airport Authority said that employee email accounts were compromised in a phishing attack and that personal information may have been compromised as a result.
- User and employee accounts accessed: A phishing attack led to more than 50,000 Snapchat users having their credentials stolen, The Verge reported. A hacker said that it’s easy to brute force user logins for Freedom Mobile and gain access to customers’ personal information. Entergy is notifying employees of a breach of W-2 information via its contractor’s website TALX due to unauthorized individuals answering employees’ personal questions and resetting PINs.
- Other notable events: Makeup Geek is notifying customers of the discovery of malware on its website that led to the theft of personal and financial information entered by visitors over a two-week period in December 2017. The Russian central bank said that hackers managed to steal approximately $6 million from a Russian bank in 2017 in an attack that leveraged the SWIFT messaging system. Western Union is informing some customers of a third-party data breach at “an external vendor system formerly used by Western Union for secure data storage” that may have exposed their personal information.
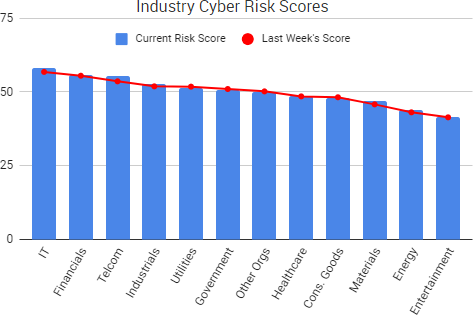
SurfWatch Labs collected data on many different companies tied to cybercrime over the past week. Some of the top trending targets are shown in the chart below.

Cyber Risk Trends From the Past Week
 The U.S. government issued a formal statement this past week blaming the Russian military for the June 2017 outbreak of NotPetya malware. Then on Friday, the day after the NotPetya accusations, the Justice Department indicted 13 Russian individuals and three Russian companies for using information warfare to interfere with the U.S. political system, including the 2016 presidential election. Those stories have once again pushed the alleged cyber activities of the Russian government into the national spotlight.
The U.S. government issued a formal statement this past week blaming the Russian military for the June 2017 outbreak of NotPetya malware. Then on Friday, the day after the NotPetya accusations, the Justice Department indicted 13 Russian individuals and three Russian companies for using information warfare to interfere with the U.S. political system, including the 2016 presidential election. Those stories have once again pushed the alleged cyber activities of the Russian government into the national spotlight.
A statement on NotPetya from White House Press Secretary Sarah Huckabee Sanders described the outbreak as “the most destructive and costly cyber-attack in history” and vowed that the “reckless and indiscriminate cyber-attack … will be met with international consequences.” Newsweek reported that the NotPetya outbreak, which leveraged the popular Ukrainian accounting software M.E. Doc to spread, cost companies more than $1.2 billion. The United Kingdom also publicly blamed Russia for the attacks, writing in a statement that “malicious cyber activity will not be tolerated.” A spokesperson for Russian President Vladimir Putin denied the allegations as “the continuation of the Russophobic campaign.”
It remains unclear what “consequences” the U.S. will impose in response to NotPetya. Politicians are still urging President Trump to enforce sanctions on Russia that were passed with bipartisan majorities in July. Newsday reported that congressmen such as democratic Sen. Chuck Schumer and republican representative Peter King have urged those sanctions to be enforced following Friday’s indictment of 13 Russians and three Russian companies.
The indictment alleges the individuals attempted to “spread distrust” towards U.S. political candidates and the U.S. political system by using stolen or fictitious identities and documents to impersonate politically active Americans, purchase political advertisements on social media platforms, and pay real Americans to engage in political activities such as rallies. For example, the indictment alleges that after the 2016 presidential election, the Russian operatives staged rallies both in favor of and against Donald Trump in New York on the same day in order to further their goal of promoting discord.
As The New York Times reported, none of those indicted have been arrested, and Russia is not expected to extradite those charged to the U.S. to face prosecution. Instead, the goal is to name and shame the operatives and make it harder for them to work undetected in future operations.
*** This is a Security Bloggers Network syndicated blog from SurfWatch Labs, Inc. authored by Jeff Peters. Read the original post at: https://blog.surfwatchlabs.com/2018/02/19/weekly-cyber-risk-roundup-olympic-malware-and-russian-cybercrime/





