How to Encrypt Gmail
Securing Your Google Email with End-to-End Encryption
In 2023, more than 300,000 organizations adopted Gmail as their go-to email management tool. However, even though it has seen widespread use, Google relies on encryption standards to safeguard Gmail data that are relatively basic such as TLS (Transport Layer Security). This poses a significant challenge for organizations that rely on Gmail as their main communication channel, as these encryption methods may not provide the level of security needed to defend data against sophisticated attacks.
With attacks on Gmail by groups such as Iran’s Charming Kitten and other rogue actions, how can organizations that heavily depend on Gmail ensure the security of their email data? Considering the limitations of Gmail’s encryption methods, organizations must explore alternative solutions to maintain the confidentiality and integrity of their sensitive information. By doing so, they can effectively protect their email data and mitigate the risks associated with potential attacks.

Why Gmail’s TLS Doesn’t Provide Adequate Security
Standard Gmail uses Transport Layer Security, or TLS, a cryptographic protocol that provides secure communication over the internet. TLS establishes a secure connection between the client (an organization’s computer) and the server (in this case, Gmail’s server), ensuring that data transmitted between the two parties is encrypted and protected from unauthorized access. This encryption helps safeguard sensitive information while it is being transferred, preventing potential eavesdropping or tampering.
#footable_5749 tbody tr td span.fooicon-plus:before { background-color: rgba(15, 1, 1, 1) !important; } #footable_5749 tbody tr td span.fooicon-minus:before { background-color: rgba(15, 1, 1, 1) !important; }
#footable_5749 tbody tr:hover td span.fooicon-plus:before { background-color: !important; } #footable_5749 tbody tr:hover td span.fooicon-minus:before { background-color: !important; }
#footable_5749 thead tr.footable-header th span::before { background-color: !important; } #footable_5749, #footable_5749 table { background-color: !important; color: rgba(15, 1, 1, 1) !important; border-color: !important; } #footable_5749 thead tr.footable-filtering th { background-color: rgba(50, 10, 10, 1) !important; color: !important; } #footable_5749:not(.hide_all_borders) thead tr.footable-filtering th { border : 1px solid transparent !important; } #footable_5749 .input-group-btn:last-child > .btn:not(:last-child):not(.dropdown-toggle) { background-color: !important; color: rgba(50, 10, 10, 1) !important; } #footable_5749 tr.footable-header, #footable_5749 tr.footable-header th, .colored_table #footable_5749 table.ninja_table_pro.inverted.table.footable-details tbody tr th { background-color: rgba(240, 95, 42, 1) !important; color: !important; }
#footable_5749 tbody tr:hover { background-color: !important; color: !important; } #footable_5749 tbody tr:hover td { border-color: !important; } #footable_5749 tbody tr:nth-child(even) { background-color: rgba(234, 234, 235, 1) !important; color: !important; } #footable_5749 tbody tr:nth-child(odd) { background-color: !important; color: !important; } #footable_5749 tbody tr:nth-child(even):hover { background-color: !important; } #footable_5749 tbody tr:nth-child(odd):hover { background-color: !important; }
#footable_5749 tbody tr:nth-child(even) td span.fooicon-plus:before { background-color: !important; } #footable_5749 tbody tr:nth-child(even) td span.fooicon-minus:before { background-color: !important; }
#footable_5749 tbody tr:nth-child(odd) td span.fooicon-plus:before { background-color: !important; } #footable_5749 tbody tr:nth-child(odd) td span.fooicon-minus:before { background-color: !important; }
#footable_5749 tbody tr:nth-child(even) tr:hover td span.fooicon-plus:before { background-color: !important; } #footable_5749 tbody tr:nth-child(even) tr:hover td span.fooicon-minus:before { background-color: !important; }
#footable_5749 tbody tr:nth-child(odd) tr:hover td span.fooicon-plus:before { background-color: !important; } #footable_5749 tbody tr:nth-child(odd) tr:hover td span.fooicon-minus:before { background-color: !important; }
#footable_5749 tfoot .footable-paging { background-color: !important; } #footable_5749 tfoot .footable-paging .footable-page.active a { background-color: !important; } #footable_5749:not(.hide_all_borders) tfoot tr.footable-paging td { border-color: !important; }
#footable_parent_2468 tbody > tr > tr { margin-bottom: 1rem; background-color:#f05f2a;}
@media screen and (min-width: 800px) { #footable_parent_2468 th, #footable_parent_2468 td { padding: 1.125em 1.375em; }}
However, it’s important to note that while TLS protects data in transit, it doesn’t address data security when the data is stored at rest on the server. In the case of Gmail, although Google claims to use “modern encryption protocols” to protect information on their servers, it’s critical to consider that all Gmail messages are encrypted with keys that Google owns and manages. To enable features like spam filtering, authorized individuals or programs within Google have access to the decryption keys and, thus, can potentially access your organization’s data. Equally important to note is that if Google has access to your decryption keys then so do attackers.
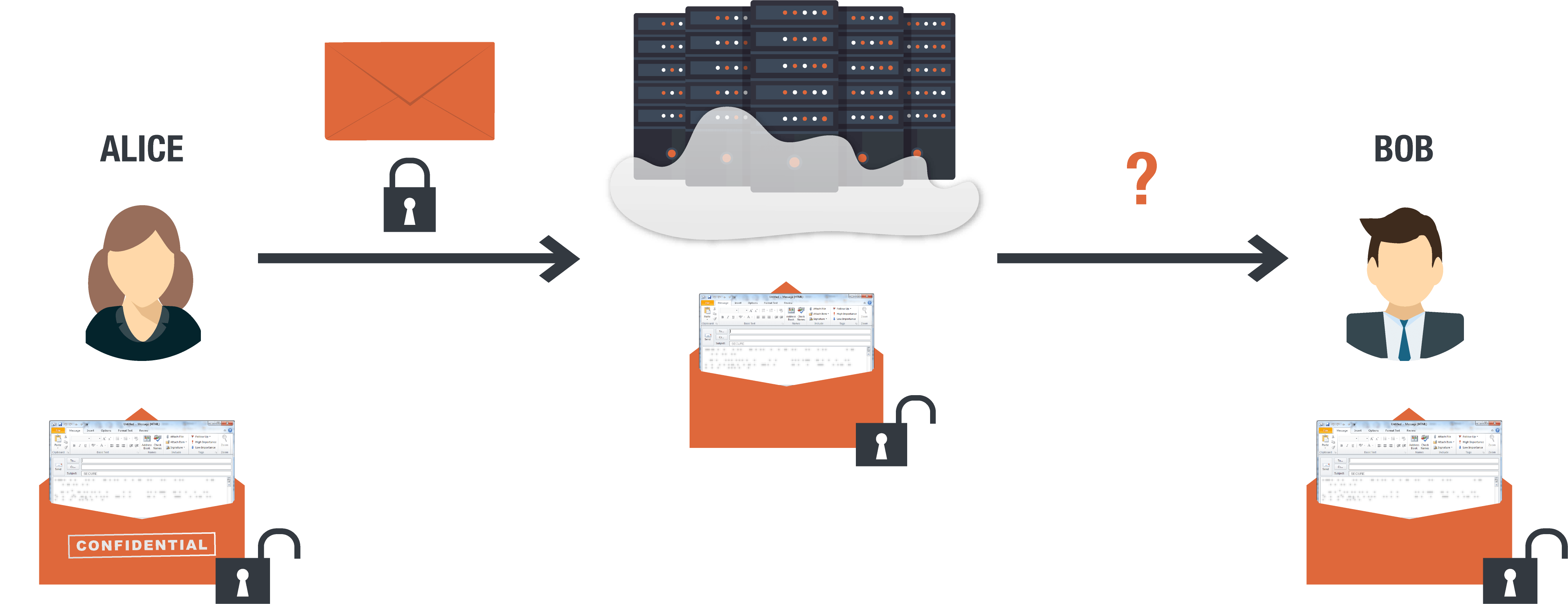
For TLS encryption to be effective, both the sender and the recipient of the message must be using it. If you use TLS to email someone, their reply may be sent insecurely.
Even if both sender and recipient use TLS and the communication channel’s encryption is not broken, the more significant issue remains: the data is not encrypted at rest. It exists naked on the server, vulnerable to hackers and the infamously overreaching surveillance of Google itself.
What is Gmail Confidential Mode
After coming under a barrage of well-deserved media fire for privacy policies that amounted to a constant digital surveillance state as the default, Gmail tried to improve its reputation by releasing Gmail Confidential.
Google’s Confidential Mode is a means of enhancing email security. This feature limits recipient actions, such as forwarding, copying, printing, or downloading the message. It’s important to note though that Confidential Mode does not encrypt the message.
Google’s Confidential Mode utilizes the same encryption standards as regular Gmail and offers no improvement in terms of encryption. The Confidential Mode includes the option to set expiration dates for messages, which can be helpful in specific contexts. Still, it’s essential to understand that these expiration dates do not enhance the underlying encryption of the message itself. Moreover, Google can potentially access your messages.
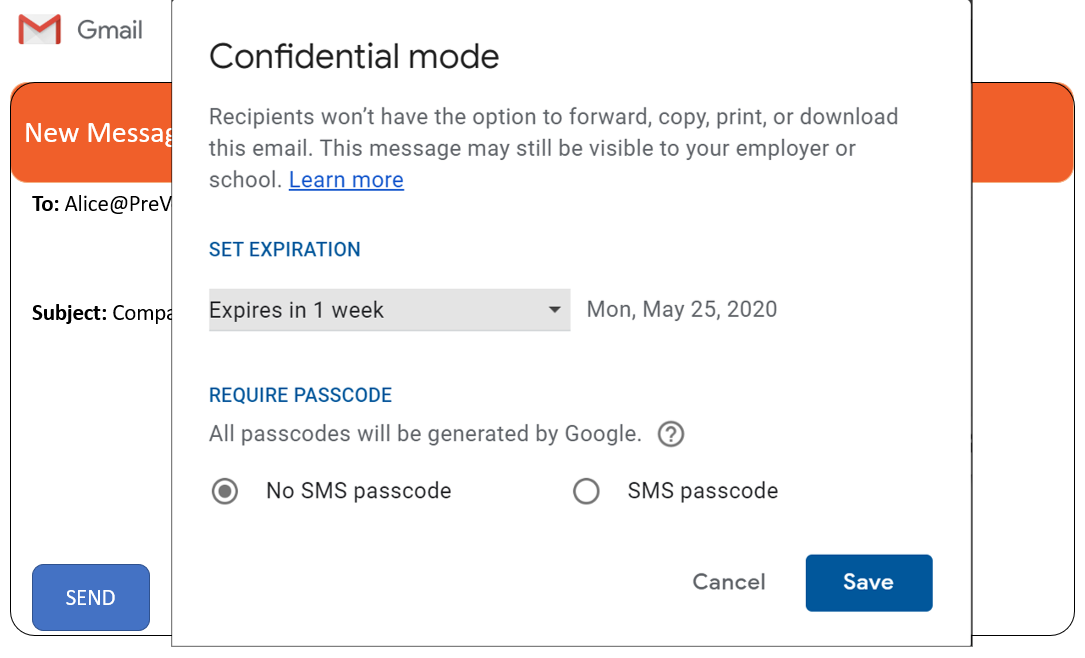
Note that in Gmail Confidential, messages can still be visible to employers or schools.
Gmail Confidential is not private and secure. Providing users with a genuinely secure option would mean giving up access to users’ data and private communications. That’s just not in Google’s DNA. Google Confidential still allows Google to read your emails.
What Protection is Provided by Google’s S/MIME Feature
Organizations utilizing Google Workspace ( a fee-based version of Google’s business apps designed for the enterprise) can leverage Secure/Multipurpose Internet Mail Extension, or S/MIME. This feature enables using the S/MIME encryption standard for email protection in Gmail. With S/MIME, organizations can safeguard their email communications through encryption.
However, implementing S/MIME for Gmail can be a cumbersome and inefficient endeavor. To utilize S/MIME, organizations must acquire third-party certificates from a certificate authority (CA) for each user and device, adding complexity and cost to the process. Additionally, these certificates from a CA must be individually installed on each user’s machine, leading to an administrative overhead.
In the S/MIME framework, certificates from a CA function as public and private keys, granting the ability to encrypt and decrypt messages. Unfortunately, managing these certifications centrally can be a daunting task. In addition, users with S/MIME for Gmail can only securely communicate with other users with the necessary certifications.
Another challenge organizations face with S/MIME is updating certificates when they expire. This ongoing maintenance adds to the complex management process, burdening organizations’ resources with updating expired certifications.
While S/MIME offers the potential for email encryption, its inefficiencies in central management, individual installation, and limited communication scope make it a less-than-ideal option for organizations seeking streamlined and user-friendly email security solutions.
Implementing PreVeil for End-to-End Encryption with Gmail
End-to-end encryption represents the gold-standard of data security and Google has attempted to provide end-to-end encryption for Gmail users. However, these efforts have yet to come to fruition and it’s unlikely they will as end-to-end encryption would not allow Google to every see your data. As a result, organizations relying on Gmail must turn to third-party solutions to achieve the desired level of security.
End-to-end encryption ensures that information is encrypted and decrypted only on users’ devices. Even when an attacker compromises the server, they only get gibberish. Nobody but the intended recipient, not even PreVeil, can read users’ messages and files.
One outstanding email solution in the market is the PreVeil email platform. PreVeil specializes in providing easy-to-use end-to-end encryption for Gmail users. End-to-end encryption ensures your data is encrypted from device to device so no one but you and the recipient can ever see the data. By installing a seamlessly integrated Chrome extension, organizations can enjoy the benefits of end-to-end encryption with Gmail.
While PreVeil’s encryption solution operates independently from Google’s encryption mechanisms, it allows Gmail users to manage their regular and encrypted inboxes side by side. This integration provides a convenient and efficient user experience while maintaining the highest security standards.
Moreover, adopting PreVeil’s end-to-end encryption standards helps organizations to meet essential compliance requirements such as ITAR and support DoD security standards like NIST 800-171, DFARS 7012, and CMMC. By leveraging these features, Gmail accounts can align with necessary security regulations while safeguarding sensitive communications.
End-to-end encryption with PreVeil enhances your organization’s email security and provides a user-friendly solution that seamlessly integrates with your existing Gmail infrastructure.
Conclusion
Organizations relying on Gmail face challenges regarding securing data and reducing attack surfaces. While Google has attempted to provide some security measures, none provide the level of convenience and security strength that end-to-end encryption offers. This is where PreVeil comes in, giving Gmail users an innovative Chrome extension solution that seamlessly integrates with existing Gmail accounts to provide end-to-end encryption.
With PreVeil, organizations can effortlessly encrypt their emails, ensuring only intended recipients can access sensitive data. This user-friendly solution allows for the seamless coexistence of regular and encrypted inboxes, streamlining workflows while maintaining the highest security standards. Moreover, PreVeil received PC Magazine’s Editors’ Choice award which noted that PreVeil is “tough enough for business but extremely easy to use, all while keeping your existing email address.”
Take the initiative to enhance your organization’s email security. Try PreVeil’s Chrome extension for Gmail today and experience the difference it can make in safeguarding your confidential communications.
![]()
Get started with securing your Gmail. Download PreVeil today!
The post How to Encrypt Gmail appeared first on PreVeil.
*** This is a Security Bloggers Network syndicated blog from Blog Archive - PreVeil authored by Orlee Berlove. Read the original post at: https://www.preveil.com/blog/how-to-encrypt-gmail/





